Question: Suppose Alice wants to send Bob an encrypted message using asymmetric cryptography. Consider the diagram below. Which of the following algorithms could be used in
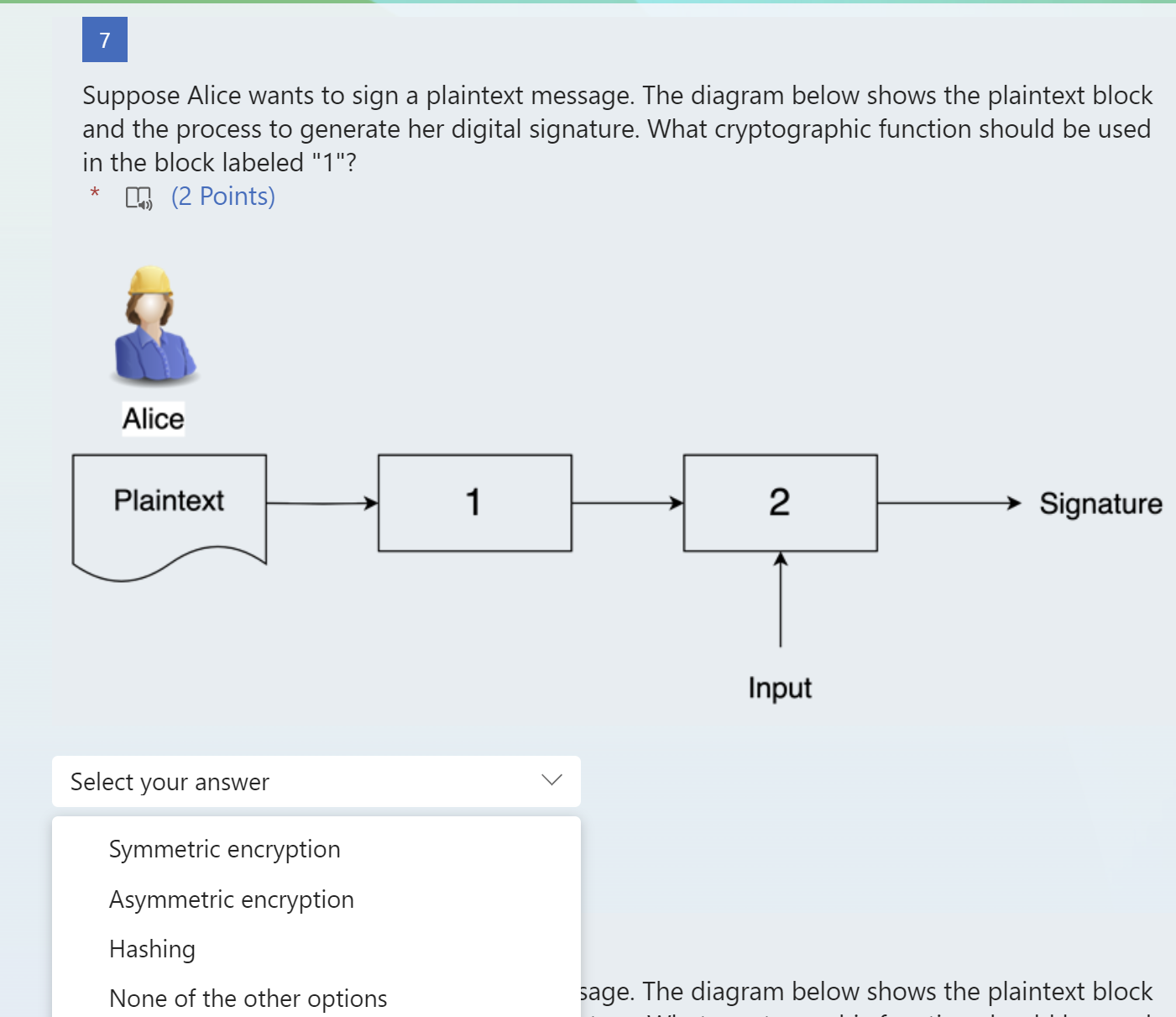
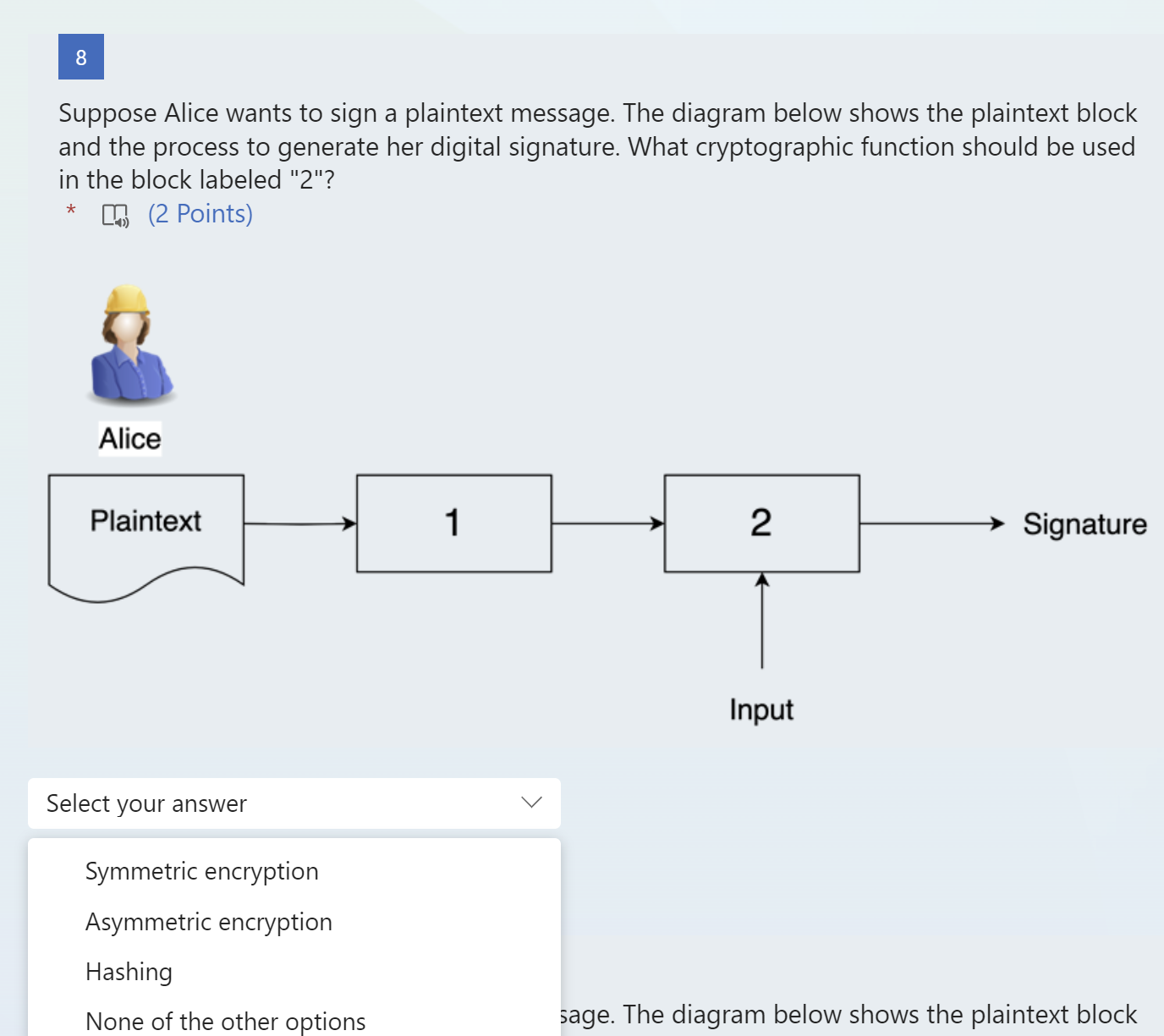
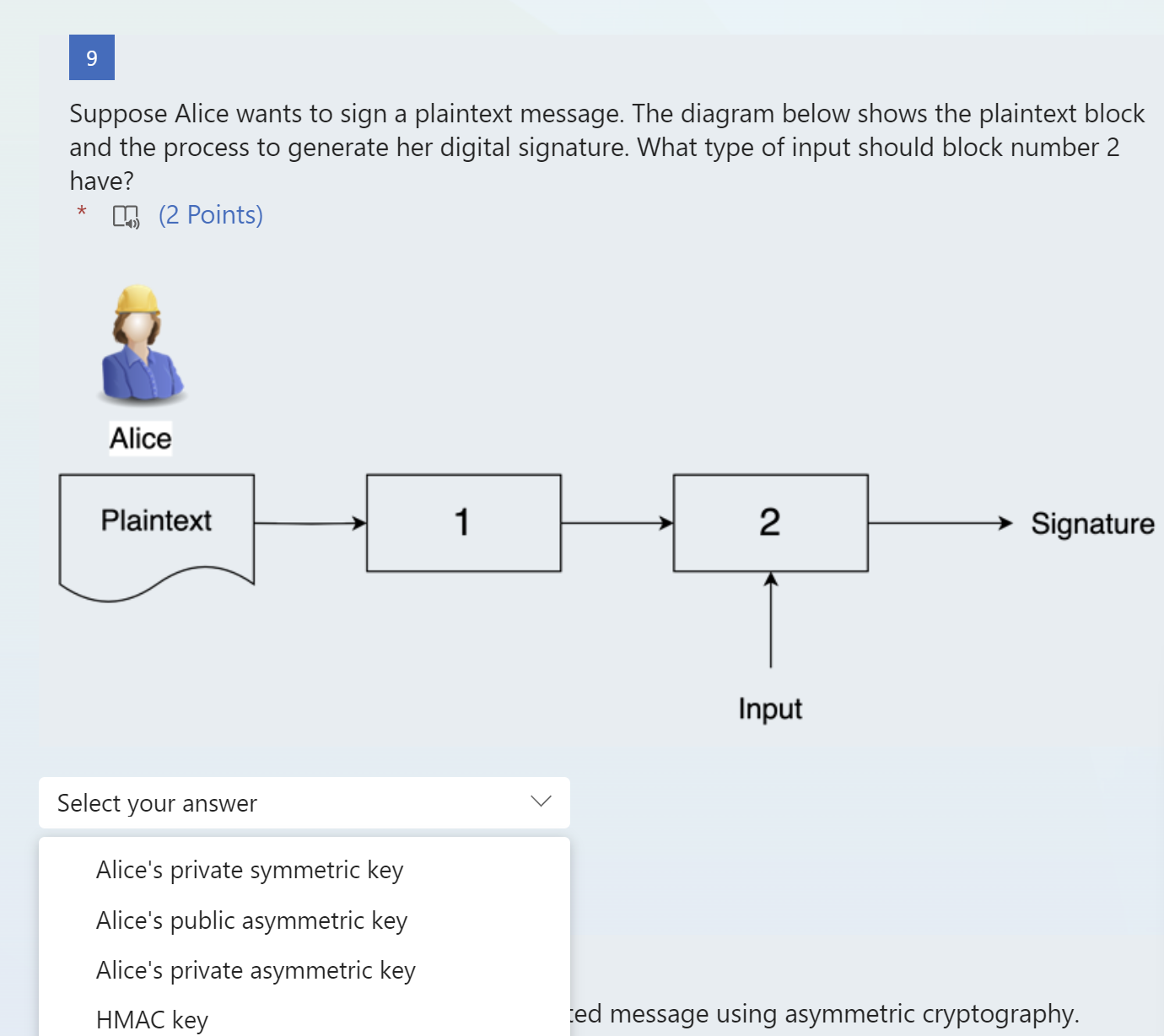
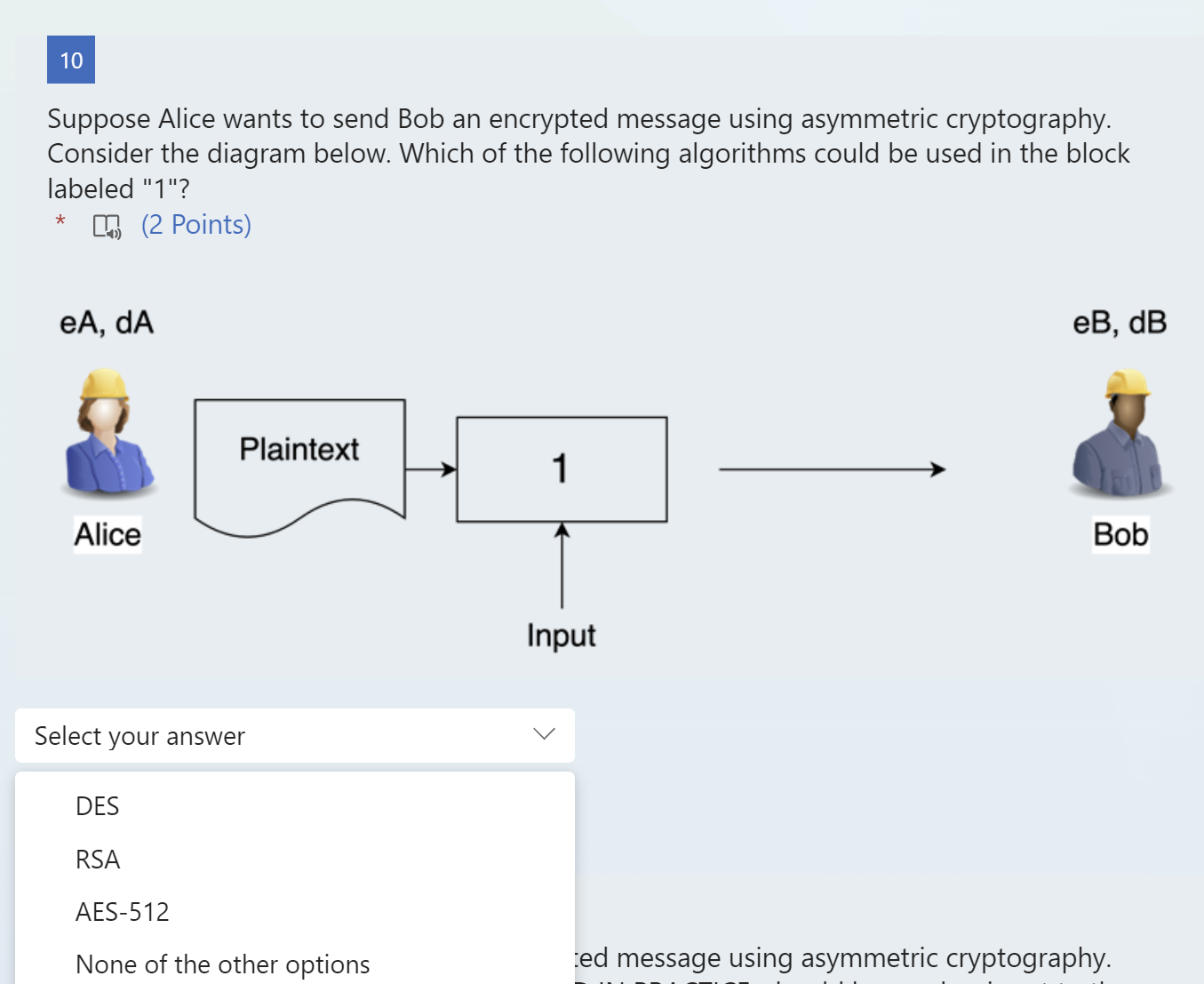
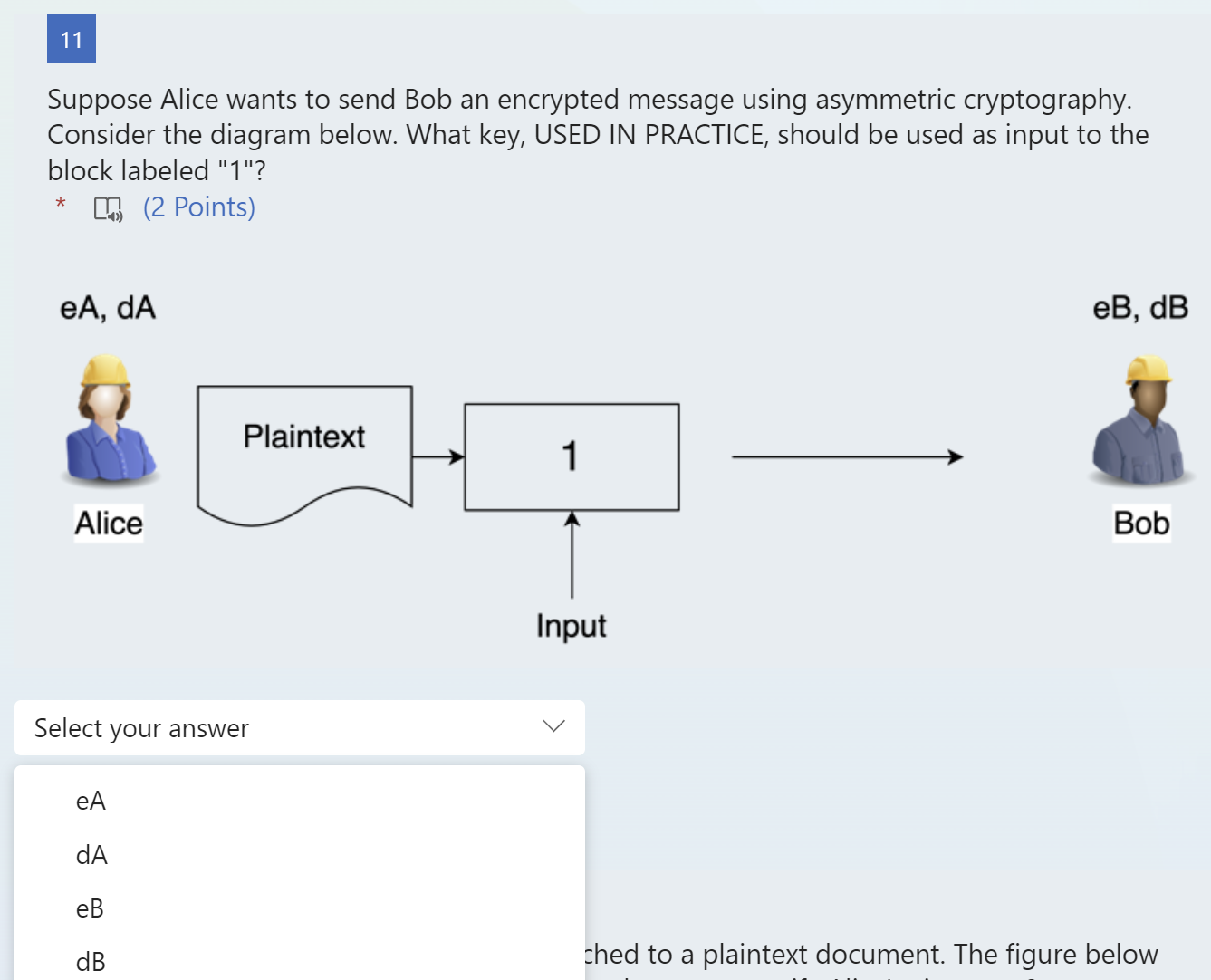
Suppose Alice wants to send Bob an encrypted message using asymmetric cryptography. Consider the diagram below. Which of the following algorithms could be used in the block labeled "1"? * 40(2 Points) ed message using asymmetric cryptography. Suppose Alice wants to send Bob an encrypted message using asymmetric cryptography. Consider the diagram below. What key, USED IN PRACTICE, should be used as input to the block labeled "1"? * 4)(2 Points) hed to a plaintext document. The figure below Suppose Alice wants to sign a plaintext message. The diagram below shows the plaintext block and the process to generate her digital signature. What cryptographic function should be used in the block labeled "2"? * 4) (2 Points) age. The diagram below shows the plaintext block Suppose Alice wants to sign a plaintext message. The diagram below shows the plaintext block and the process to generate her digital signature. What cryptographic function should be used in the block labeled "1"? * 41)(2 Points) age. The diagram below shows the plaintext block Suppose Alice wants to sign a plaintext message. The diagram below shows the plaintext block and the process to generate her digital signature. What type of input should block number 2 have? (2 Points) !d message using asymmetric cryptography
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


