Question: Tcpdump and analyzing network traces Ignore any error messages about bad tcp cksum, they are not relevant. For all of the following, show both the
Tcpdump and analyzing network traces
Ignore any errormessages about bad tcp cksum, they are not relevant.
For all of the following, show both the tcpdump command you used, and the output of the command, DO NOT FORGET TO ANSWER ANY QUESTIONS POSED ABOUT THE OUTPUT. This assignment is as much about following instructions carefully as well as using tcpdump and reading network traces. Do not use grep, all results must be filtered with tcpdump filters or macros.
You should always use the nn option to prevent DNS and port lookups on the addresses in the records.
File TEST.pcap:
9. Show all records with an ICMP type of 8 and ICMP code of 0. (5 points)
9b) Find all records with a TTL less than 255. Use the -v option to see the TTL field. (5 points)
File DG2.pcap:
9c) Examine the traffic between hosts 1.1.1.1 and 10.10.10.160. What type of activity is occurring? (5 points)
9d) Examine the traffic between hosts 1.1.1.1 and 10.10.10.20. What caused the ICMP error ip reassembly time exceeded? (5 points)
9e) Examine the traffic to destination port 21. Are these spoofed packets from the same host or multiple hosts performing scans? (use the vv flag to see more info like TTLs) Why or why not?
First image is test.pcap and second is dg2.pcap
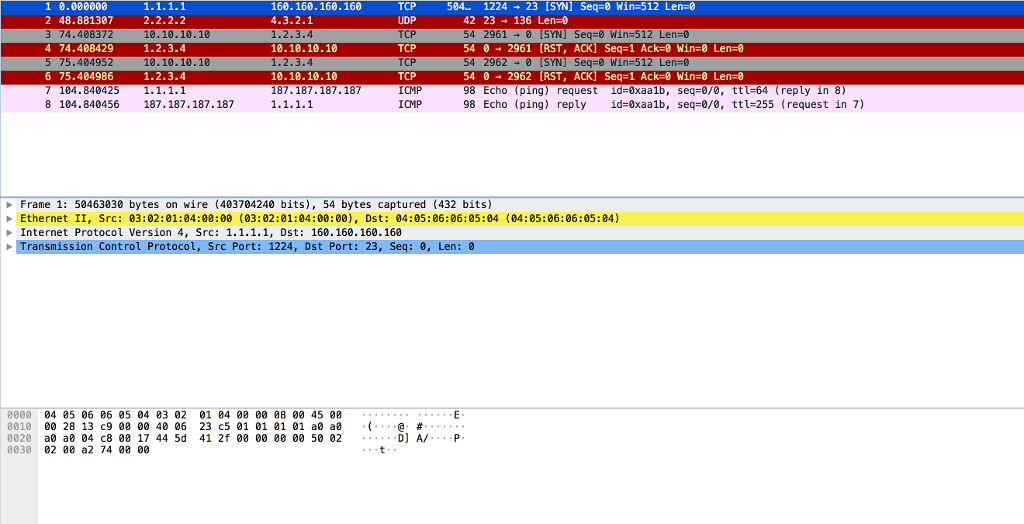
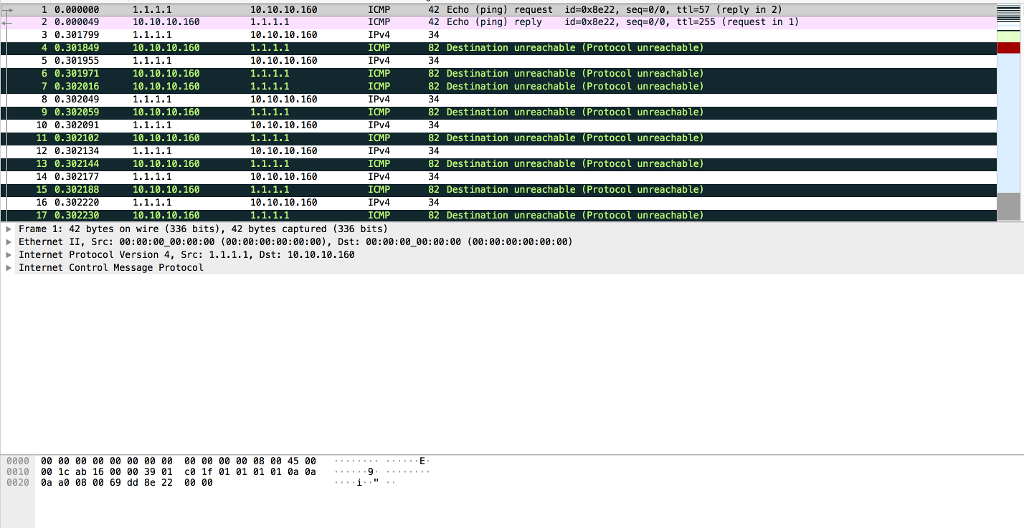
160.160.160.160 1 0.000000 2 48.881307 3 74.408372 4 74.408429 5 75.404952 6 75.404986 7 104.840425 8 104.840456 TCP UDP TCP TCP TCP TCP ICMP ICMP 584 1224 23 [SYN] Seq-0 Win-512 Len-0 2.2.2.2 10.10.10.18 1.2.3.4 10.10.10.10 1.2.3.4 4.3.2.1 1.2.3.4 10.10.10.10 1.2.3.4 10.10.10.10 187.187.187.187 42 23136 Len-0 54 2961-0 [SYN] Seq=0 Win=512 Len=0 54 0 2961 [RST, ACK] Segel Ack=0 win=0 Len 54 29620 [SYN] Seq=0 Win=512 Len=0 54 02962 [RST, ACK] Seq 1 Ack-0 Win-0 Len-0 98 Echo (ping) request id=0xaa1b, seq=0/0, ttl-64 (reply in 8) 98 Echo (ping) reply id-0xaa1b, seq-0/0, ttl-255 (request in 7) 187.187.187.187 Frame 1: 50463030 bytes on wire (403704240 bits), 54 bytes captured (432 bits) Ethernet II, Src: 03:02:01:84:08:00 (03:02:01:04:00:00), Dst: 04:05:06:06:05:04 (04:05:06:06:05:84) Internet Protocol Version 4, Src: 1.1.1.1, Dst: 160.160.160.160 Transmission Control Protocol, Src Port: 1224, Dst Port: 23, Seq: , Len: 0 8000 04 85 06 06 85 04 83 02 01 04 08 00 88 00 45 08 0010 0028 13 c9 08 00 40 06 23 c5 01 01 01 01 a0 a0 .( e 8020 a0 a8 04 c8 00 17 44 5d 41 2f 00 00 08 00 50 02D] A/.P 8030 02 80 a2 74 08 00 160.160.160.160 1 0.000000 2 48.881307 3 74.408372 4 74.408429 5 75.404952 6 75.404986 7 104.840425 8 104.840456 TCP UDP TCP TCP TCP TCP ICMP ICMP 584 1224 23 [SYN] Seq-0 Win-512 Len-0 2.2.2.2 10.10.10.18 1.2.3.4 10.10.10.10 1.2.3.4 4.3.2.1 1.2.3.4 10.10.10.10 1.2.3.4 10.10.10.10 187.187.187.187 42 23136 Len-0 54 2961-0 [SYN] Seq=0 Win=512 Len=0 54 0 2961 [RST, ACK] Segel Ack=0 win=0 Len 54 29620 [SYN] Seq=0 Win=512 Len=0 54 02962 [RST, ACK] Seq 1 Ack-0 Win-0 Len-0 98 Echo (ping) request id=0xaa1b, seq=0/0, ttl-64 (reply in 8) 98 Echo (ping) reply id-0xaa1b, seq-0/0, ttl-255 (request in 7) 187.187.187.187 Frame 1: 50463030 bytes on wire (403704240 bits), 54 bytes captured (432 bits) Ethernet II, Src: 03:02:01:84:08:00 (03:02:01:04:00:00), Dst: 04:05:06:06:05:04 (04:05:06:06:05:84) Internet Protocol Version 4, Src: 1.1.1.1, Dst: 160.160.160.160 Transmission Control Protocol, Src Port: 1224, Dst Port: 23, Seq: , Len: 0 8000 04 85 06 06 85 04 83 02 01 04 08 00 88 00 45 08 0010 0028 13 c9 08 00 40 06 23 c5 01 01 01 01 a0 a0 .( e 8020 a0 a8 04 c8 00 17 44 5d 41 2f 00 00 08 00 50 02D] A/.P 8030 02 80 a2 74 08 00
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


