Question: There is a login protocol between a user (ATM card) and a server (ATM machine), which works as follows: The user U has a password
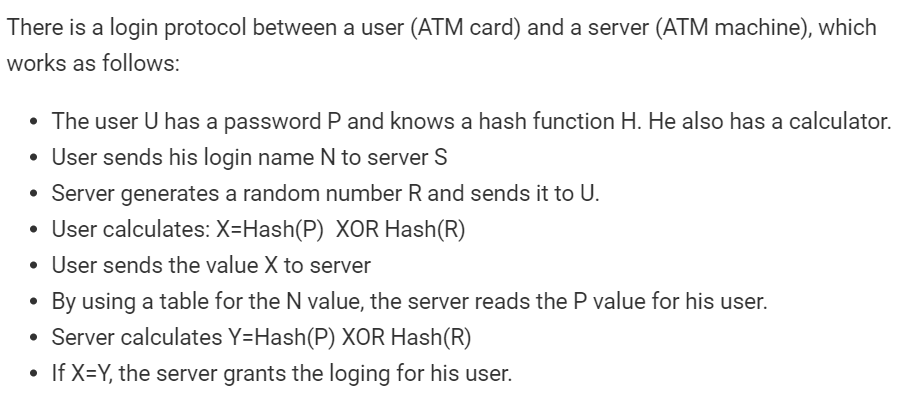
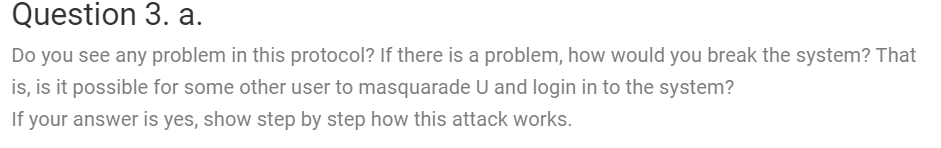
There is a login protocol between a user (ATM card) and a server (ATM machine), which works as follows: The user U has a password P and knows a hash function H. He also has a calculator. User sends his login name N to server S Server generates a random number R and sends it to U. User calculates: X=Hash(P) XOR Hash(R) User sends the value X to server By using a table for the N value, the server reads the P value for his user. Server calculates Y=Hash(P) XOR Hash(R) If X=Y, the server grants the loging for his user. . Question 3. a. Do you see any problem in this protocol? If there is a problem, how would you break the system? That is, is it possible for some other user to masquarade U and login in to the system? If your answer is yes, show step by step how this attack works
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


