Question: THESE ARE THE VALUES U NEED TO ADD IN TASK 2 AND TASK 5. Task 2 When you configure the TCP/IP protocol on a Microsoft
THESE ARE THE VALUES U NEED TO ADD IN TASK 2 AND TASK 5.
Task 2
When you configure the TCP/IP protocol on a Microsoft Windows computer, an IP address, subnet mask, and usually a default gateway are required in the TCP/IP configuration settings. Subnetting allows you to create multiple logical networks that exist within a single Class A, B, or C network.
Each student is given a separate Class B IP address.
Based on the information shown in the above diagram, design a network-addressing scheme (by completing the table below) that will supply the minimum number of subnets for all the devices on the Technology Centre. You need to allow enough extra subnets and hosts for 50% growth in all circled areas and explain how subnetting of TCP/IP suit of protocols will enable the effectiveness of above network systems.
Task 3
You will need to produce a discussion of the operating principles of the main networking devices and server types and relate this to the interdependence of workstation hardware to the appropriate networking software that could be used in the above network:
- Networking devices:
Servers; Hub, routers, switches, access point (wireless/wired), Load balancer, VPN, Firewall, HIDS, IOT gateway
- Networking software:
Client operating system, server operating system, Internetwork Operating System (IOS) used on many Cisco Systems routers and current Cisco network switches using show version command.
- Workstation: the inter-dependence of workstation hardware with relevant networking software and hardware, e.g. network card, cabling (Fibre Optic, UTP, STP), file permissions.
Task 5
In most cases, having the same subnet mask for all subnets ends up wasting address space wasted address space due to the fact that the same subnet mask is being used for all the subnets. Use the Variable Length Subnet Masks (VLSM) to address the efficient utilisation of a networking system and show in the tables below the wasted address spaces and Point-to-Point link networks (only two hosts on each) are used. Furthermore, explain the advantages of using the VLSM in the above network.
Comments ;:
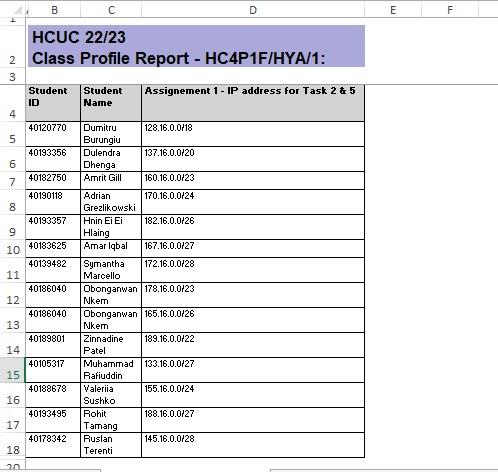
The class profile table report values are to be added in Task 2 and Task 5
Cisco packet tracer screenshots are to be added of Task 3 only.
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


