Question: This assignment is a two-step process. Study the Compromised Personal Network Indicators and Mitigations, its on google, Then create a risk management plan for a
This assignment is a two-step process. Study the Compromised Personal Network Indicators and Mitigations, its on google, Then create a risk management plan for a personal network using the data collected. Use the following template for this assignment: Assignment 2.1 Metric Table Click for more options Note: These recommendations only apply to System Safety and Risk Metrics associated with personal networks. Therefore do NOT copy ALL the indicators from the Indicators of a personal network compromise.
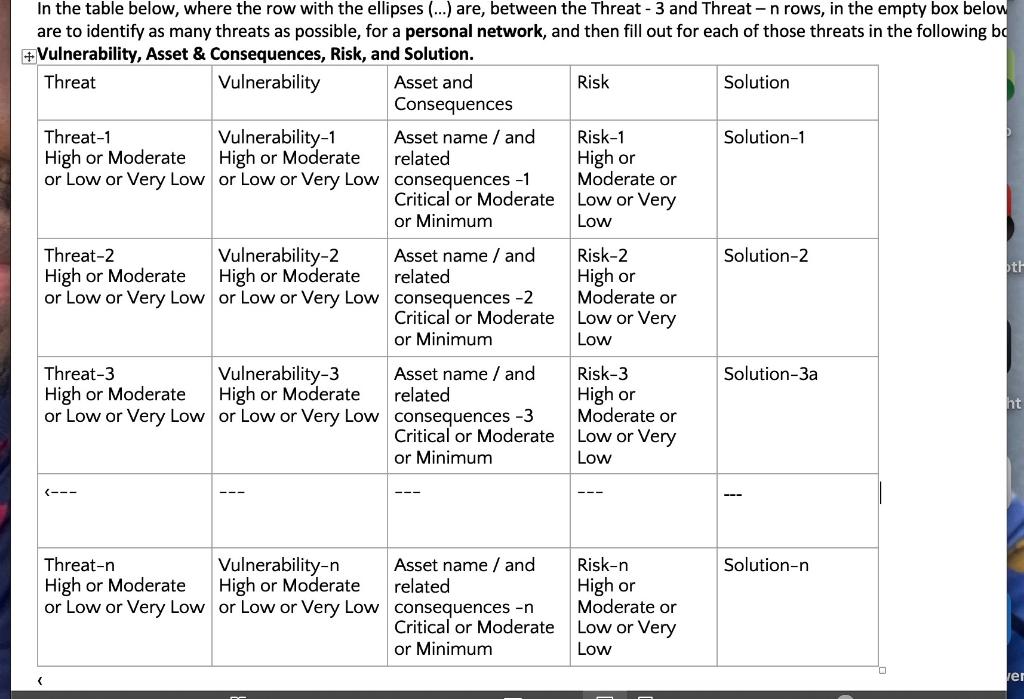
In the table below, where the row with the ellipses (..)are,betweentheThreat3 and Threat n rows, in the empty box below are to identify as many threats as possible, for a personal network, and then fill out for each of those threats in the following be
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


