Question: This question illustrates an attack on two-key triple encryption. Let F be a block cipher with n-bit block length and key length, and set F'_k_1,
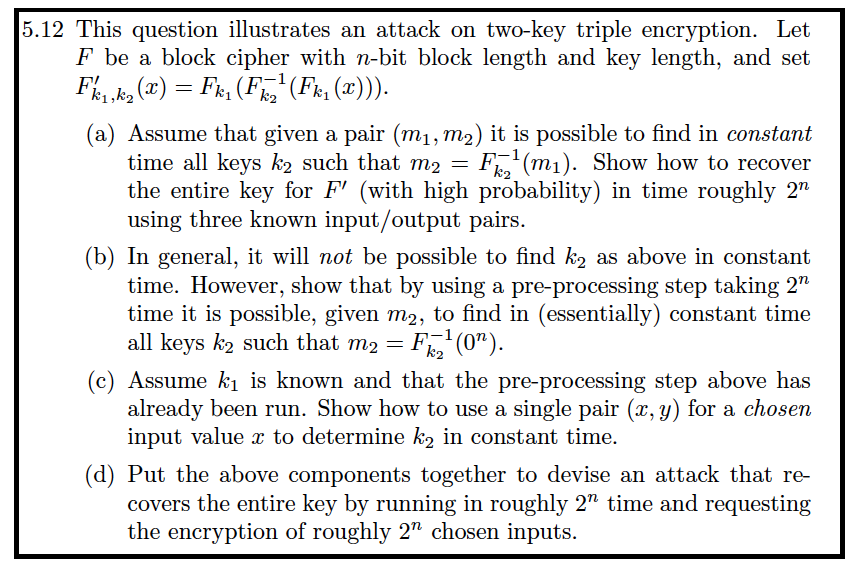
This question illustrates an attack on two-key triple encryption. Let F be a block cipher with n-bit block length and key length, and set F'_k_1, k_2 (x) = F_k_1 (F^-1_k_2 (F_k_1 (x))). (a) Assume that given a pair (m_1, m_2) it is possible to find in constant time all keys k_2 such that m_2 = F^-1_k_2 (m_1). Show how to recover the entire key for F' (with high probability) in time roughly 2^n using three known input/output pairs. (b) In general, it will not be possible to find k_2 as above in constant time. However, show that by using a pre-processing step taking 2^n time it is possible, given m_2, to find in (essentially) constant time all keys k_2 such that m_2 = F^-1_k_2 (0^n). (c) Assume k_1 is known and that the pre-processing step above has already been run. Show how to use a single pair (x, y) for a chosen input value x to determine k_2 in constant time. (d) Put the above components together to devise an attack that recovers the entire key by running in roughly 2^n time and requesting the encryption of roughly 2^n chosen inputs. This question illustrates an attack on two-key triple encryption. Let F be a block cipher with n-bit block length and key length, and set F'_k_1, k_2 (x) = F_k_1 (F^-1_k_2 (F_k_1 (x))). (a) Assume that given a pair (m_1, m_2) it is possible to find in constant time all keys k_2 such that m_2 = F^-1_k_2 (m_1). Show how to recover the entire key for F' (with high probability) in time roughly 2^n using three known input/output pairs. (b) In general, it will not be possible to find k_2 as above in constant time. However, show that by using a pre-processing step taking 2^n time it is possible, given m_2, to find in (essentially) constant time all keys k_2 such that m_2 = F^-1_k_2 (0^n). (c) Assume k_1 is known and that the pre-processing step above has already been run. Show how to use a single pair (x, y) for a chosen input value x to determine k_2 in constant time. (d) Put the above components together to devise an attack that recovers the entire key by running in roughly 2^n time and requesting the encryption of roughly 2^n chosen inputs
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


