Question: Block Cipher Given a two-key triple encryption for block cipher. Let F be a block cipher with n-bit block length and key length, and set
Block Cipher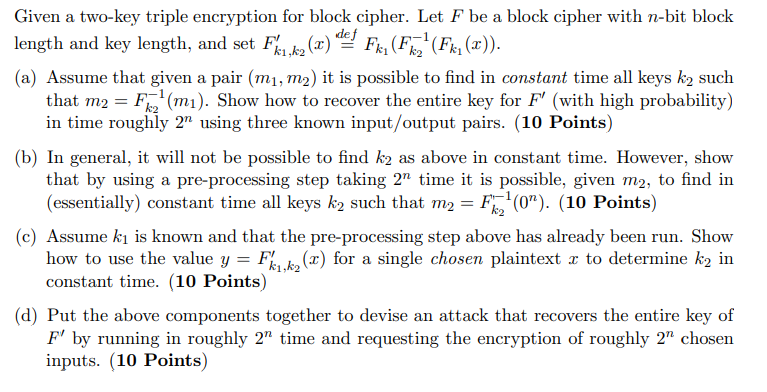
Given a two-key triple encryption for block cipher. Let F be a block cipher with n-bit block length and key length, and set Fx1,22(x) def Fk, (FR?! (Fk (x)). (a) Assume that given a pair (m1, m2) it is possible to find in constant time all keys k2 such that m2 = F2(mi). Show how to recover the entire key for F' (with high probability) in time roughly 2n using three known input/output pairs. (10 Points) (b) In general, it will not be possible to find k2 as above in constant time. However, show that by using a pre-processing step taking 2n time it is possible, given m2, to find in (essentially) constant time all keys k2 such that m2 = FK?! 0). (10 Points) (C) Assume ki is known and that the pre-processing step above has already been run. Show how to use the value y F%1,62() for a single chosen plaintext x to determine ka in constant time. (10 Points) (d) Put the above components together to devise an attack that recovers the entire key of F' by running in roughly 2" time and requesting the encryption of roughly 2" chosen inputs. (10 Points) = Given a two-key triple encryption for block cipher. Let F be a block cipher with n-bit block length and key length, and set Fx1,22(x) def Fk, (FR?! (Fk (x)). (a) Assume that given a pair (m1, m2) it is possible to find in constant time all keys k2 such that m2 = F2(mi). Show how to recover the entire key for F' (with high probability) in time roughly 2n using three known input/output pairs. (10 Points) (b) In general, it will not be possible to find k2 as above in constant time. However, show that by using a pre-processing step taking 2n time it is possible, given m2, to find in (essentially) constant time all keys k2 such that m2 = FK?! 0). (10 Points) (C) Assume ki is known and that the pre-processing step above has already been run. Show how to use the value y F%1,62() for a single chosen plaintext x to determine ka in constant time. (10 Points) (d) Put the above components together to devise an attack that recovers the entire key of F' by running in roughly 2" time and requesting the encryption of roughly 2" chosen inputs. (10 Points) =
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


