Question: USE PYTHON PROGRAMING. File Encryption/Decryption Program: You are to design and write a program that allows a user to interactively select between encrypting or decrypting
USE PYTHON PROGRAMING.

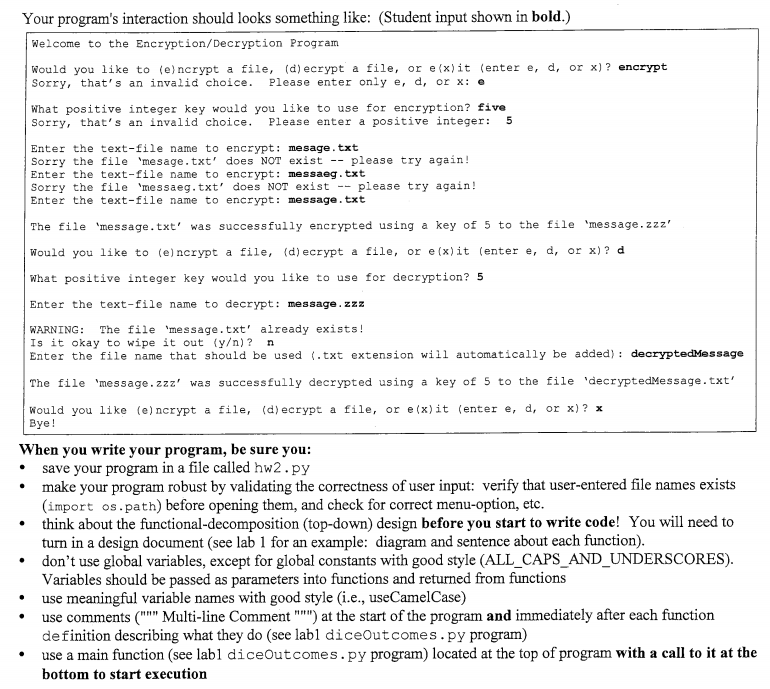
File Encryption/Decryption Program: You are to design and write a program that allows a user to interactively select between encrypting or decrypting files encrypting a user-specified text-file (.txt extension) using the encryption scheme described below to generatea new encoded file with the same name, except with a .zzz extension. decrypting a user-specified encrypted file (. zzz extension) using a user-specified keyword to generate a new text-file with the same name, except with a .txt extension. * The encryption scheme is a form of substitution cipher based on a user-specified positive integer key and the follow sequence of 78 characters: (Note: blank-space character between the "K" and sequece position: 012345678901234567890123456789012345678901234567890123456789012345678901234567 0 The integer key is used to encrypt only the first letter in the message by "shifting" down the above sequence by that amount. For example, an integer key of 5 shifts 'B' to the encrypted d, Shifting past the right end of the sequence wraps back to the beginning of the sequence. For example, shifting 5 from encrypts as*b. The sequence position of the first letter in the message is used as the shift amount for the second letter in the message If the first letter was a 'B,' then 4 is used to shift the second letter in the message since 'B' is at position 4 (start with 'a' at position 0, 'A' at position 1, etc.). The sequence position of the second letter in the message is used as the shift amount for the third letter, etc. Any message character not in the above sequence (eg, ,'f") is copied to the encrypted message without modification with the previous shift amount carrying over to the next letter in the message to be encrypted. Consider the following example with key 5 Four Line Message to Encrypt with Key-5 in file message.txt Encrypted Message in file message.zzz Be by the Union at 6 PM! dF/, z83al/fHvwb& t3RRalg
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


