Question: Using Irvine32.inc in Assembly: Each string-handling procedure assumes the use of null-terminated strings. Even when not explicitly requested, write a short driver program for each
Using Irvine32.inc in Assembly:
Each string-handling procedure assumes the use of null-terminated strings. Even when not explicitly requested, write a short driver program for each exercise solution that tests your new procedure.
Write a procedure called Str_nextWord that scans a string for the ?rst occurrence of a certain delimiter character and replaces the delimiter with a null byte. There are two input parameters: a pointer to the string and the delimiter character. After the call, if the delimiter was found, the Zero ?ag is set and EAX contains the offset of the next character beyond the delimiter. Otherwise, the Zero ?ag is clear and EAX is unde?ned. The following example code passes the address of target and a comma as the delimiter:
.data
target BYTE "Johnson,Calvin",0
.code
INVOKE Str_nextWord, ADDR target, ','
jnz notFound
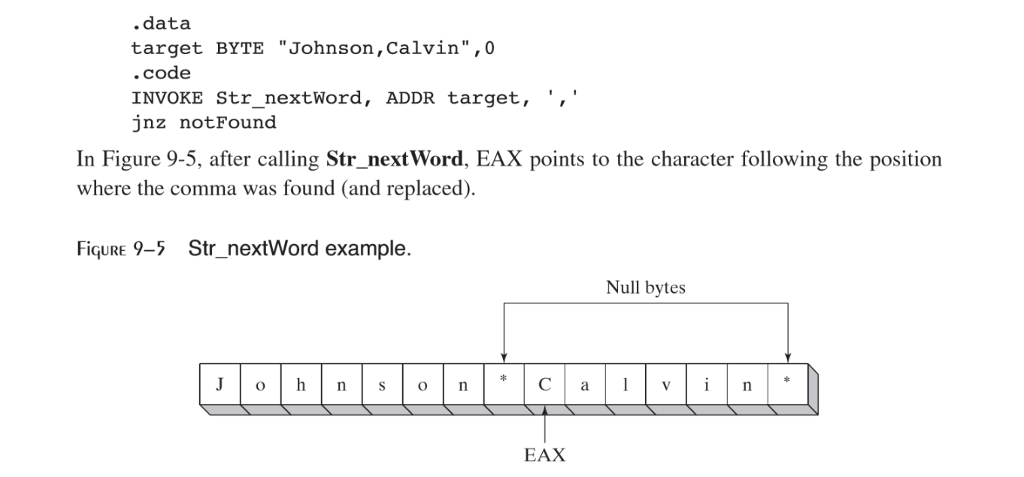
.data target BYTE "Johnson, Calvin", 0 .code INVOKE Str_nextWord, ADDR target, ',' jnz notFound In Figure 9-5, after calling Str_nextWord, EAX points to the character following the position where the comma was found (and replaced). FIGURE 9-5 StrnextWord example. Null bytes EAX .data target BYTE "Johnson, Calvin", 0 .code INVOKE Str_nextWord, ADDR target, ',' jnz notFound In Figure 9-5, after calling Str_nextWord, EAX points to the character following the position where the comma was found (and replaced). FIGURE 9-5 StrnextWord example. Null bytes EAX
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


