Question: Using the Security models listed below place each model into the appropriate lock box. Each Lock represents data in transit, and you have to
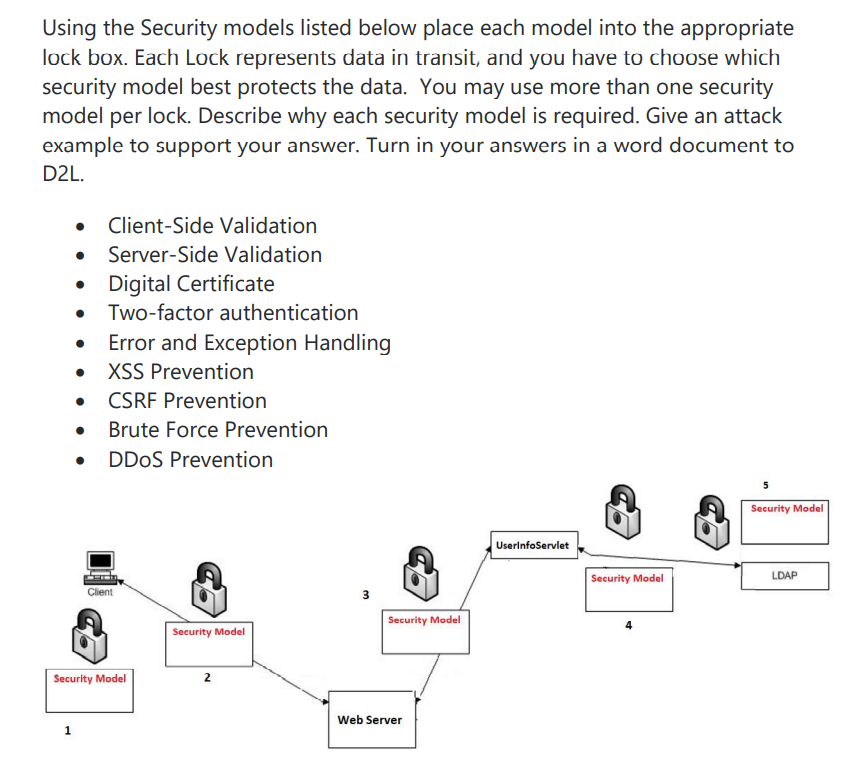
Using the Security models listed below place each model into the appropriate lock box. Each Lock represents data in transit, and you have to choose which security model best protects the data. You may use more than one security model per lock. Describe why each security model is required. Give an attack example to support your answer. Turn in your answers in a word document to D2L. . Client-Side Validation Server-Side Validation Digital Certificate Two-factor authentication Error and Exception Handling XSS Prevention CSRF Prevention Brute Force Prevention DDoS Prevention Client Security Model Security Model 2 1 3 Security Model Web Server 5 Security Model UserInfoServlet Security Model LDAP
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


