Question: Given the following C code file, perform a stack smash on the vuln.c code file using a C program that you create named exploit.c.
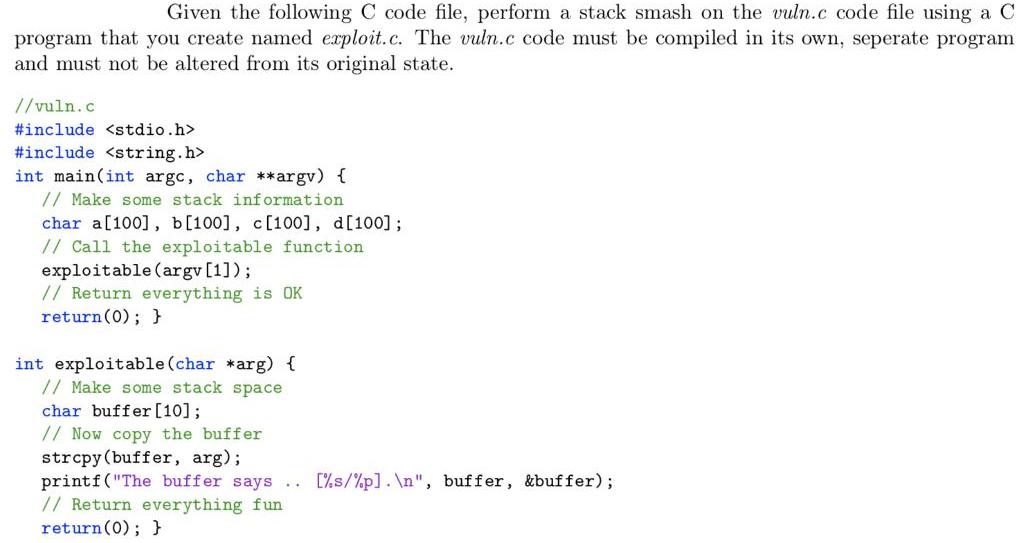
Given the following C code file, perform a stack smash on the vuln.c code file using a C program that you create named exploit.c. The vuln.c code must be compiled in its own, seperate program and must not be altered from its original state. //vuln.c #include #include int main(int argc, char **argv) { // Make some stack inf ormation char a[100], b[100], c[100], d[100]; // Call the exploitable function exploitable (argv [1]); // Return everything is OK return(0); } int exploitable(char *arg) { // Make some stack space char buffer[10]; // Now copy the buffer strcpy(buffer, arg); printf("The buffer says .. // Return everything fun return(0); } [%s/%p]. ", buffer, &buffer);
Step by Step Solution
3.47 Rating (160 Votes )
There are 3 Steps involved in it
include include int exploitablechar arg int mainint argc char argv ch... View full answer

Get step-by-step solutions from verified subject matter experts
Document Format (2 attachments)
635d6671aa812_175237.pdf
180 KBs PDF File
635d6671aa812_175237.docx
120 KBs Word File


