Question: Vulnerabilities are O A. trade-offs between risks and costs OB. assets that are desired by a hacker or spy c. trade-offs between security and freedom

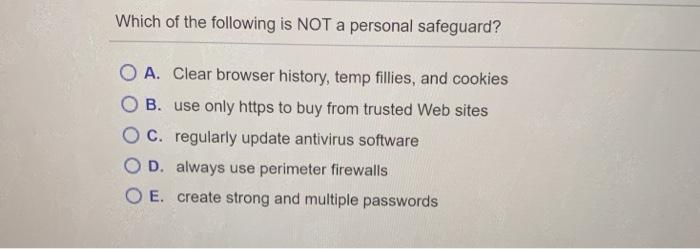
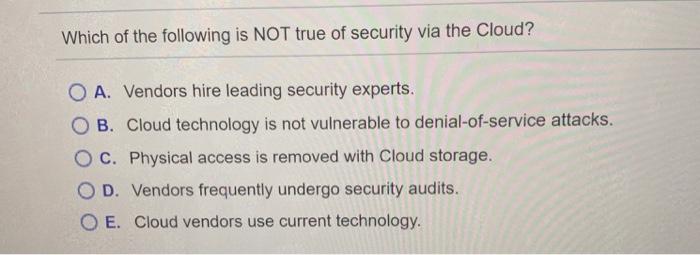
Vulnerabilities are O A. trade-offs between risks and costs OB. assets that are desired by a hacker or spy c. trade-offs between security and freedom OD. actions that individuals or organizations take to protect a weakness O E. weaknesses in an IS that provide an opportunity for threats to gain access Which of the following is NOT a personal safeguard? O A. Clear browser history, temp fillies, and cookies B. use only https to buy from trusted Web sites C. regularly update antivirus software OD. always use perimeter firewalls O E. create strong and multiple passwords Which of the following is NOT true of security via the Cloud? O A. Vendors hire leading security experts. B. Cloud technology is not vulnerable to denial-of-service attacks. Oc. Physical access is removed with Cloud storage. OD. Vendors frequently undergo security audits. O E. Cloud vendors use current technology
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


