Question: When pointers are corrupted from format string vulnerabilities and heap overflows, an adversary can inject arbitrary input into critical parts of a process's memory. One
When pointers are corrupted from format string vulnerabilities and heap overflows, an adversary can inject arbitrary input into critical parts of a process's memory. One such area for corruption is the procedure link table: a table of function pointers that support dynamically linked library calls. The table is filled in at load time to support runtime code relocation and is often left writeable. In this level, you are allowed one arbrtrary write to an arbitrary memory location between x and xff to unlock the program. We have added a call to sleep that you may hijack. To do so use objdump" or gdb to find its PLT entry, the memory location to overwrite and the address of the function to execute instead. We have included the source code for you to peruse. Note that the password will be read in using: scanflx lx;
The password is a hexadecimal address and a hexadecimal value to place at that address.
Here's the full C code:
char msg
From overthewire.org When pointers are corrupted from format string
"vulnerabilities and heap overflows, an adversary can inject arbitrary
"input into critical parts of a process's memory. One such area for
"corruption is the procedure link table: a table of function pointers
"that support dynamically linked library calls. The table is filled in at
"load time to support runtime code relocation and is often left writeable.
In this level, you are allowed one arbrtrary write to an arbitrary memory
"location between x and xff to unlock the program. We have added
"a call to sleep that you may hijack. To do so use objdump or gdb
to find its PLT entry, the memory location to overwrite and the address of
"the function to execute instead. We have included the source code for you
to peruse. Note that the password will be read in using:
scanflx lx;
;
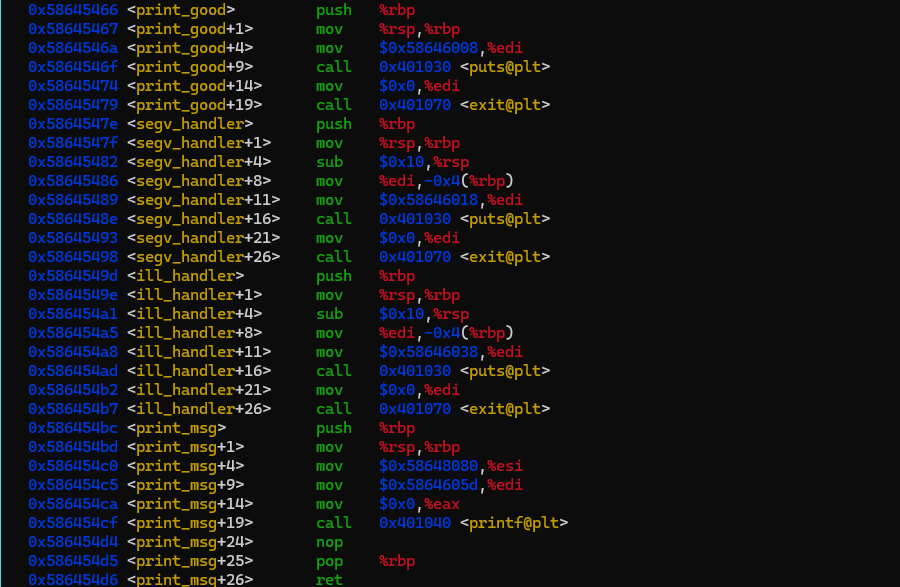
void printgood
printfGood Job.
;
exit;
void segvhandlerint sig
printfSegmentation fault. Try again.
;
exit;
void illhandlerint sig
printfIllegal instruction hit. Try again.
;
exit;
void printmsg
printfsmsg;
int main
unsigned long int ip;
unsigned long int i;
signalSIGSEGV segvhandler;
signalSIGILL illhandler;
printmsg;
printfThe password is a hexadecimal address and a hexadecimal value
;
printfto place at that address.
;
printfEnter the password: ;
scanflx lxunsigned long int &ip&i;
if ip unsigned long int xff
printfAddress too high. Try again.
;
exit;
ip i;
printfThe address: lx will now contain lx
unsigned long int ipi;
sleep;
printfTry again.
;
exit;
Output of objdump D grep printgood:
:
Here's the output of objdump D grep sleep:
a: e d ba db a call
:
: ff ba f jmp xfbarip #
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


