Question: which options best fits the statement ? What do you call a group of compromised computers? A notice that guarantees a user or a website
which options best fits the statement ?
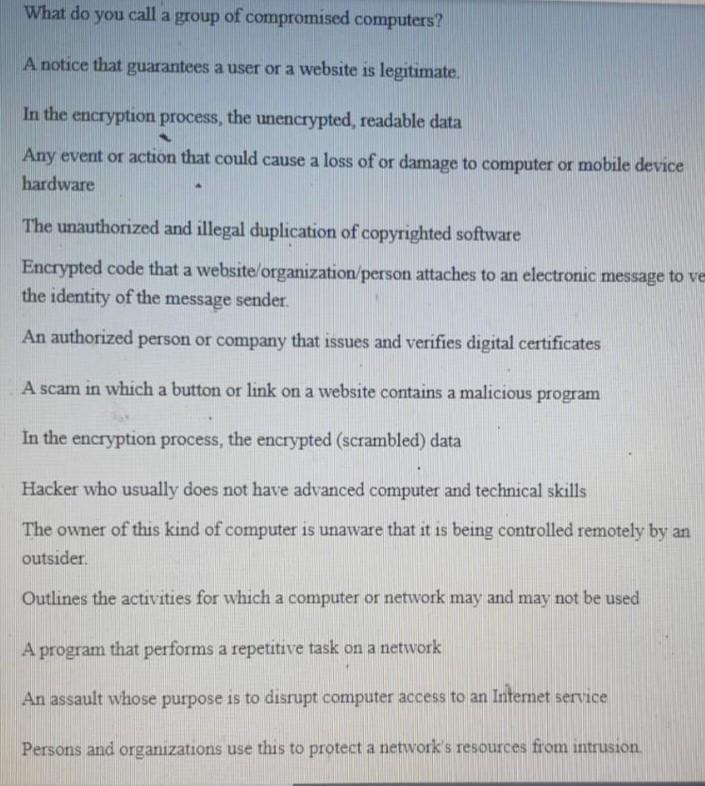
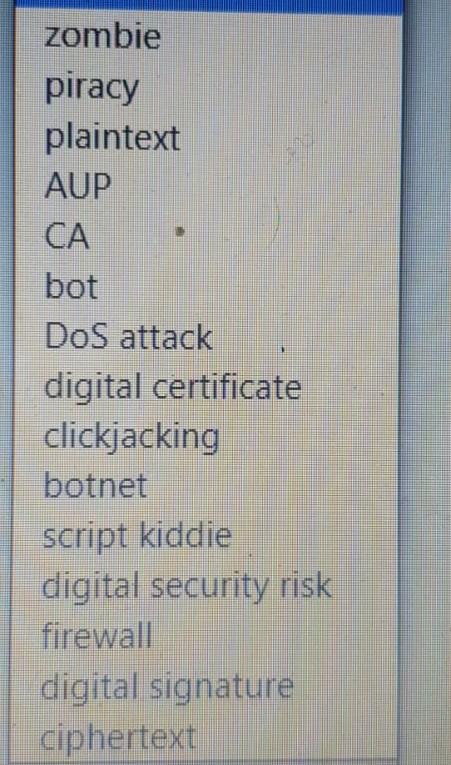
What do you call a group of compromised computers? A notice that guarantees a user or a website is legitimate. In the encryption process, the unencrypted, readable data Any event or action that could cause a loss of or damage to computer or mobile device hardware The unauthorized and illegal duplication of copyrighted software Encrypted code that a website/organization person attaches to an electronic message to ve the identity of the message sender An authorized person or company that issues and verifies digital certificates A scam in which a button or link on a website contains a malicious program In the encryption process, the encrypted (scrambled) data Hacker who usually does not have advanced computer and technical skills The owner of this kind of computer is unaware that it is being controlled remotely by an outsider. Outlines the activities for which a computer or network may and may not be used A program that performs a repetitive task on a network An assault whose purpose is to disrupt computer access to an Internet service Persons and organizations use this to protect a network's resources from intrusion. 12 zombie piracy plaintext AUP CA bot DoS attack digital certificate clickjacking botnet script kiddie digital security risk firewall digital signature ciphertext
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


