Question: Write c++ code using the following classes. Use columnar transposition cipher, follow the hierarchy diagram for inheritance. Define your class in header file and implement
Write c++ code using the following classes. Use columnar transposition cipher, follow the hierarchy diagram for inheritance. Define your class in header file and implement in .cpp file. You can test your code using the main.cpp file, it should follow the given output.


//Exception.h
#include using namespace std;
class Exception { //data member protected: string error; public: //constructor Exception(const string& message) { error=message; //set the message } //function getError string getError() { return error; //returns error message } };
//Cipher.h #include
using namespace std;
class Cipher { //abstract or pure virtual functions below public: virtual string encode(const string&)=0; virtual string decode(const string&)=0; };
//TranspositionCipher.h #include "Exception.h" #include "Cipher.h"
using namespace std;
class TranspositionCipher:public Cipher { //public override methods from Cipher public: string encode(const string&); string decode(const string&); //other methods prototyping protected: virtual string scramble(const string&)=0; //pure virtual virtual string unscramble(const string&)=0; //pure virtual string removeSpaces(const string&); string toUpperCase(const string&); };
//TranspositionCipher.cpp
#include "TranspositionCipher.h"
using namespace std;
//implementation of encode string TranspositionCipher::encode(const string &pt) { //code here string newSt="";//empty new text if(pt.length()
//implementation of decode string TranspositionCipher::decode(const string &ct) { if(ct.length()
//implementation of removespaces() string TranspositionCipher::removeSpaces(const string &st) { string newSt="";//empty string for(unsigned int i=0;i if(st[i]!=' ') //when not a space newSt+=st[i];//concate the char return newSt;//finally return new string without space }
//implementation of toUpperCase() string TranspositionCipher::toUpperCase(const string &st) { string newSt="";//empty string for(unsigned int i=0;i if(st[i]>=97 && st[i]
//main.cpp
#include #include #include "Columnar.h"
using namespace std; /* The following main tests the functionality of various ciphers.
Use at your own discretion, and feel free to extend and/or modify in any way.
This file will be overwritten by the automarker if submitted. */
void testCipher(Cipher& cipher, const string& text) { try { string encoded = cipher.encode(text); cout
int main() { string shortText="Top Secret";
string longText="According to Larry Wall, the original author of the Perl programming language, there are three great virtues of a programmer; Laziness, Impatience, and Hubris. Laziness: The quality that makes you go to great effort to reduce overall energy expenditure. It makes you write labor-saving programs that other people will find useful and document what you wrote so you don't have to answer so many questions about it. Impatience: The anger you feel when the computer is being lazy. This makes you write programs that don't just react to your needs, but actually anticipate them. Or at least pretend to. Hubris: The quality that makes you write (and maintain) programs that other people won't want to say bad things about."; Columnar cc("key"); testCipher(cc, " a "); testCipher(cc, shortText); testCipher(cc, longText); try { cc.setCodeword("bAAA"); } catch(Exception e) { cout
OUTPUT
The provided text is too short to be safely encrypted
OEETSRPCT TOPSECRET
CRNORWLHRILTRTPLOAILGGTRRHEEVTSAOAELISIAEENUILISTQLYAASUTRTFTRUORLEYPDU.MEOREB-VGOATTHPPWLNSUNOMTAOREYD'ATNEONUTNBT.PICTAEOEWNEMTIEGZTSKYWTRRSAOTSETYRE,TTLAIPEEOTAPTD.BSHUITTKYWTAMNIPGMHOEELOTNOYDISO.AOITAYLTOGAUOFERRRMGNA,EATERTREFRRM;ZE,PICAHR.ZE:EATHMEOOGAFRODEELNGXNTETKYWTARANRRSATROELIUFADUNHYWTOUNHEAWSAQSOAUTMTN:EGYFLEHOURBNA.IASUIPGMHD'URCOUESUCAYTITH.AETENOUITQLYAASUI(DIA)OATTHPPW'ATAAHGBTCDGLRA,EINAHOHEPGMNAUEHEERGAIUOPGMRANSMTN,DBSANSHUITTKYGOEEOTECVAEREEIRIASUILOSIPGMHOEELIFDELDCEWTUOSOOTVOSRMYEISOIIAEEHNRUEHTCPESILYHMEOREOATTNJTATONDBAULNCATMRLSRETHR:EATHMEORENATNRRSATROENWTSBTNAUA ACCORDINGTOLARRYWALL,THEORIGINALAUTHOROFTHEPERLPROGRAMMINGLANGUAGE,THEREARETHREEGREATVIRTUESOFAPROGRAMMER;LAZINESS,IMPATIENCE,ANDHUBRIS.LAZINESS:THEQUALITYTHATMAKESYOUGOTOGREATEFFORTTOREDUCEOVERALLENERGYEXPENDITURE.ITMAKESYOUWRITELABOR-SAVINGPROGRAMSTHATOTHERPEOPLEWILLFINDUSEFULANDDOCUMENTWHATYOUWROTESOYOUDON'THAVETOANSWERSOMANYQUESTIONSABOUTIT.IMPATIENCE:THEANGERYOUFEELWHENTHECOMPUTERISBEINGLAZY.THISMAKESYOUWRITEPROGRAMSTHATDON'TJUSTREACTTOYOURNEEDS,BUTACTUALLYANTICIPATETHEM.ORATLEASTPRETENDTO.HUBRIS:THEQUALITYTHATMAKESYOUWRITE(ANDMAINTAIN)PROGRAMSTHATOTHERPEOPLEWON'TWANTTOSAYBADTHINGSABOUT.A
The codeword provided is not going to generate a safe encryption
The codeword provided is not going to generate a safe encryption
OSCEAATRPETA TOPSECRETAAA
CODNTLRYALTERGNLUHRFHPRPORMIGAGAETEERTRERAVRUSFPORME;AIESIPTEC,NHBI.AIESTEULTTAMKSOGTGETFOTOEUEVRLEEGEPNIUEIMKSOWIEAO-AIGRGASHTTEPOLWLFNUEUADOUETHTOWOEOODNTAEONWROAYUSINAOTTIPTEC:HAGROFEWETEOPTRSENLZ.HSAEYURTPORMTADNTUTECTYUNESBTCULYNIIAEHMOALATRTNT.URSTEULTTAMKSOWIEADANANPORMTAOHREPEO'WNTSYATIGAOTAAIALOAOERMN,AETERMZ,IARZ:AHEOARDENXTTYTRNRAREIFDNYTUHASQOUMNEYLHUBAISIGH'ROEUATT.EEOIQYAU(I)ATPWAAHBCRGORW,HIIATOTELGANLUGHREHGEITOAGARLNSMANEDUSLNSHQIYTAYUOREFTRCOALRYEDR.AEURLBSVPOMTOHEPILDSLNCMWAURSYO'VTSEMNETSBI.AIETNEUEHNCMEIIGYTMKOWERASTOJSATORD,ATLACPTERTSPEDHB:HAIHTEYRTNMTIRGSHTEOLNTTOBDNSU. ACCORDINGTOLARRYWALL,THEORIGINALAUTHOROFTHEPERLPROGRAMMINGLANGUAGE,THEREARETHREEGREATVIRTUESOFAPROGRAMMER;LAZINESS,IMPATIENCE,ANDHUBRIS.LAZINESS:THEQUALITYTHATMAKESYOUGOTOGREATEFFORTTOREDUCEOVERALLENERGYEXPENDITURE.ITMAKESYOUWRITELABOR-SAVINGPROGRAMSTHATOTHERPEOPLEWILLFINDUSEFULANDDOCUMENTWHATYOUWROTESOYOUDON'THAVETOANSWERSOMANYQUESTIONSABOUTIT.IMPATIENCE:THEANGERYOUFEELWHENTHECOMPUTERISBEINGLAZY.THISMAKESYOUWRITEPROGRAMSTHATDON'TJUSTREACTTOYOURNEEDS,BUTACTUALLYANTICIPATETHEM.ORATLEASTPRETENDTO.HUBRIS:THEQUALITYTHATMAKESYOUWRITE(ANDMAINTAIN)PROGRAMSTHATOTHERPEOPLEWON'TWANTTOSAYBADTHINGSABOUT.A
The ciphertext is of incorrect length
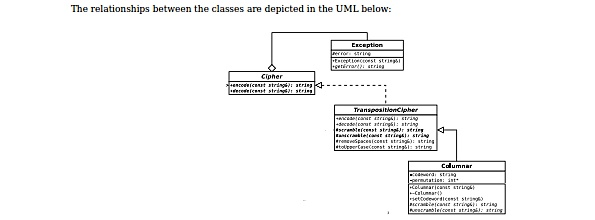
The relationships between the classes are depicted in the UML below: TranspoaitonClpher
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


