Question: Writing Use Cases, Abuse Cases, and Misuse Cases Goal: Learn how to write abuse and misuse cases. System Description: The Internet - based Information Security
Writing Use Cases, Abuse Cases, and Misuse Cases
Goal:
Learn how to write abuse and misuse cases.
System Description:
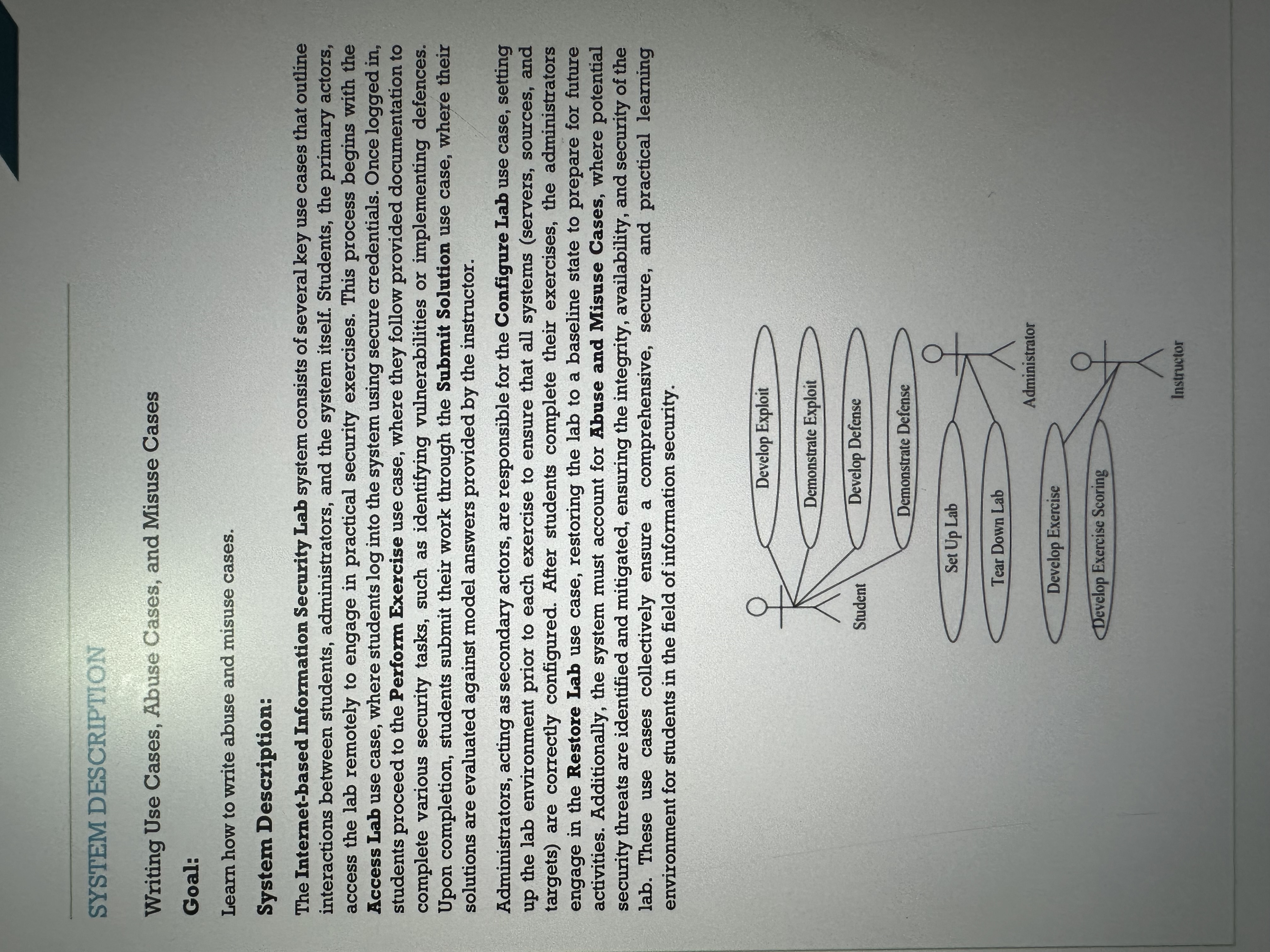
The Internetbased Information Security Lab system consists of several key use cases that outline interactions between students, administrators, and the system itself. Students, the primary actors, access the lab remotely to engage in practical security exercises. This process begins with the Access Lab use case, where students log into the system using secure credentials. Once logged in students proceed to the Perform Exercise use case, where they follow provided documentation to complete various security tasks, such as identifying vulnerabilities or implementing defences. Upon completion, students submit their work through the Submit Solution use case, where their solutions are evaluated against model answers provided by the instructor.
Administrators, acting as secondary actors, are responsible for the Configure Lab use case, setting up the lab environment prior to each exercise to ensure that all systems servers sources, and targets are correctly configured. After students complete their exercises, the administrators engage in the Restore Lab use case, restoring the lab to a baseline state to prepare for future activities. Additionally, the system must account for Abuse and Misuse Cases, where potential security threats are identified and mitigated, ensuring the integrity, availability, and security of the lab. These use cases collectively ensure a comprehensive, secure and practical learning environment for students in the field of information security. Steps:
Create a Document:
Title it "Requirements Specification for Xreplace X with your system's name
Outline Requirements:
Describe the system and its security goals.
Identify actors both normal users and attackers
Choose two use case titles and their actors from the use case diagram and describe them briefly.
Provide one Abuse and one Misuse Case:
Describe how the use case can be abused or misused. Use both the notations to express the selected abuse and misuse cases covered in lecture
Describe one of the abuse and misuse cases. Include everything covered in the lecture steps eg title, actors, preconditions, post conditions, summary, steps or flow of events.
Sketchdraw second one by extending the use case include all elements of the abusemisuse cases.
Define Security Requirements:
Summarize security requirements from the abusemisuse cases chosen.
List them with identifiers eg "Secl" at the document's end.
Submission:
Submit the final document to the learning management system LMS
This exercise helps you understand the interaction between intended use and potential misuse of a system, and how to document security measures accordingly.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


