Question: You are given the following shellcode, essentially identical to that used in Lab #1 (the only difference being that the trap to exit has been
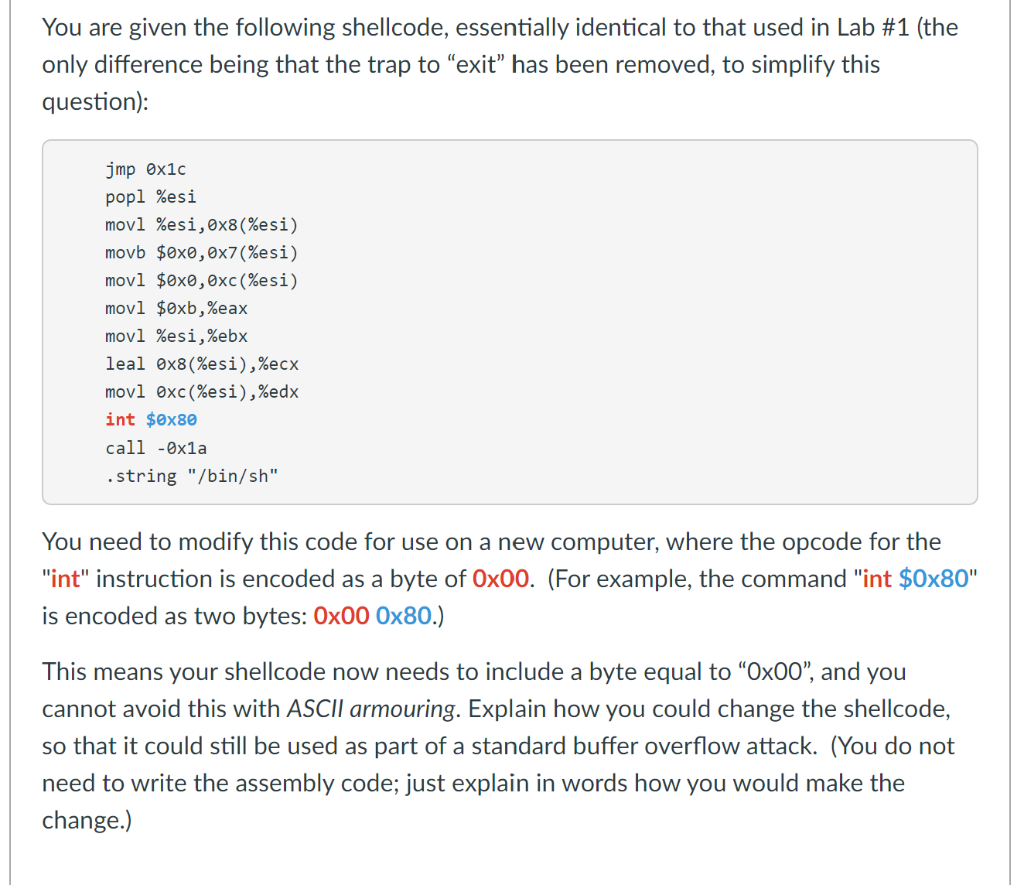
You are given the following shellcode, essentially identical to that used in Lab #1 (the only difference being that the trap to exit has been removed, to simplify this question): jmp Ox1c popl %esi movl %esi, 0x8(%esi) movb $0x0,0x7(%esi) movl $0x0,oxc(%esi) movl $oxb,%eax movl %esi,%ebx leal 0x8%esi),%ecx movl oxc(%esi),%edx int $0x80 call - Oxla .string "/bin/sh" You need to modify this code for use on a new computer, where the opcode for the "int" instruction is encoded as a byte of Ox00. (For example, the command "int $0x80" is encoded as two bytes: 0x00 0x80.) This means your shellcode now needs to include a byte equal to Ox00", and you cannot avoid this with ASCII armouring. Explain how you could change the shellcode, so that it could still be used as part of a standard buffer overflow attack. (You do not need to write the assembly code; just explain in words how you would make the change.)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


