Question: You have a software for a deterministic message authentication code MAC = (K, T) that is known to be UF-CMA secure under some reasonable
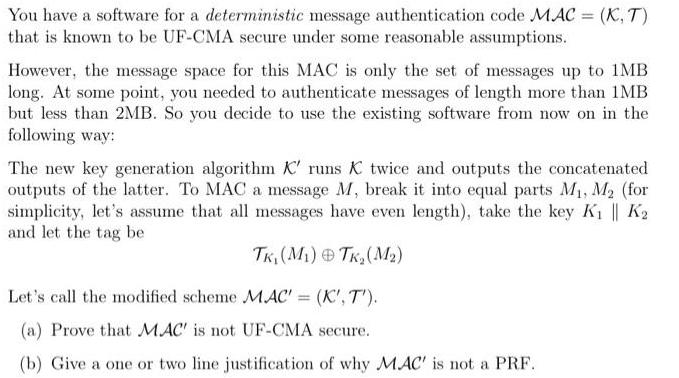
You have a software for a deterministic message authentication code MAC = (K, T) that is known to be UF-CMA secure under some reasonable assumptions. However, the message space for this MAC is only the set of messages up to 1MB long. At some point, you needed to authenticate messages of length more than 1MB but less than 2MB. So you decide to use the existing software from now on in the following way: The new key generation algorithm K' runs K twice and outputs the concatenated outputs of the latter. To MAC a message M, break it into equal parts M, M (for simplicity, let's assume that all messages have even length), take the key K || K and let the tag be TK (M) TK (M) Let's call the modified scheme MAC' = (K', T'). (a) Prove that MAC' is not UF-CMA secure. (b) Give a one or two line justification of why MAC' is not a PRF.
Step by Step Solution
3.34 Rating (148 Votes )
There are 3 Steps involved in it
Answer Consider an adversary who wants to forge a valid tag for a message M by exploiting the fact t... View full answer

Get step-by-step solutions from verified subject matter experts


