Question: 1. Decrypting the cypher text created by an XOR operation is easyjust use the same XOR operation on the encrypted bits! Demonstrate this for the
1. Decrypting the cypher text created by an XOR operation is easy€”just use the same XOR operation on the encrypted bits! Demonstrate this for the example above.
2. Suppose the secret key were longer€”the eight bits 1100 0011. Using this key and an XOR, what is the cypher text for the plain text message €œGo, team€ if the bit configuration for these letters is as shown below.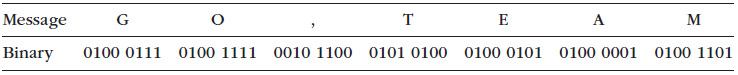
Goose Bay Concrete specializes in creating driveways and curbs for the residential market. Its accounting software uses exclusive OR (XOR) operations to convert the individual bits of a plain text message into cyphertext. The rules are as follows: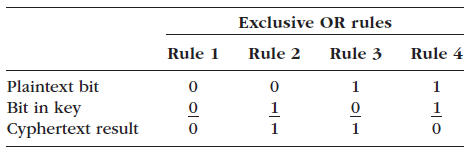
In other words, exactly one of the bits must be a €œ1€ and the other a €œ0€ for the result of an XOR operation to be a €œ1.€ To illustrate, suppose that the bits representing a single plain text character were 1010 0101 and the secret key used just the four bits 1110. Here are the results of the XOR operation, using this key:
Message Binary G E A M 0100 0111 0100 1111 0010 1100 0101 0100 0100 0101 0100 0001 0100 1101 Exclusive OR rules Rule 1 Rule 2 Rule 3 Rule 4 Plaintext bit Bit in key Cyphertext result 0
Step by Step Solution
3.38 Rating (176 Votes )
There are 3 Steps involved in it
This case requires students to use XOR operations to both encrypt and decrypt a message 1 Ap... View full answer

Get step-by-step solutions from verified subject matter experts


