Can you suggest a security improvement to either option in Figure 6.11, using only three DES chips
Question:
Can you suggest a security improvement to either option in Figure 6.11, using only three DES chips and some number of XOR functions? Assume you are still limited to two keys.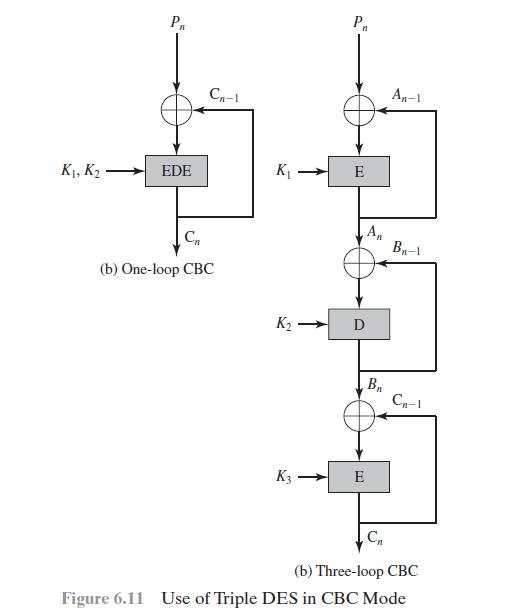
Transcribed Image Text:
K, K P EDE C-1 C (b) One-loop CBC K K K3 Pr n E D A E B C An-1 B-1 C-1 (b) Three-loop CBC Figure 6.11 Use of Triple DES in CBC Mode
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 0% (1 review)
Instead of mathrmCBCmathrmCBCmathrmCBCmathrmX use ECB mathrm...View the full answer

Answered By

PU Student
cost accounting
financial accounting
auditing
internal control
business analyst
tax
i have 3 years experience in field of management & auditing in different multinational firms. i also have 16 months experience as an accountant in different international firms. secondary school certification.
higher secondary school certification.
bachelors in mathematics.
cost & management accountant
4.80+
4+ Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Managing Scope Changes Case Study Scope changes on a project can occur regardless of how well the project is planned or executed. Scope changes can be the result of something that was omitted during...
-
In this exercise, we explore the concept o f marginal rates of substitution (and, in part B, its relation to utility functions) further. A: Suppose I own 3 bananas and 6 apples, and you own 5 bananas...
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
Dream House Builders, Inc. applies overhead by linking it to direct labor. At the start of the current period, management predicts total direct labor costs of $100,000 and total overhead costs of...
-
A meteorite melts and burn up at temperatures of 3000 K. If it hits air at 5 kPa, 50 K how high a velocity should it has to experience such a temperature?
-
A scan path test circuit of the type shown in Figure 10-8 has three flip-flops, two inputs, and two outputs. One row of the state table of the sequential circuit to be tested is as follows: For this...
-
On February 11, 2009, plaintiff Levista, Inc. (plaintiff) filed against defendant Ranbaxy Pharmaceuticals, Inc. (defendant), pursuant to this Courts diversity jurisdiction under 28 U.S.C. 1332(a),...
-
BAP Corporation is reviewing an investment proposal. The initial cost and estimates of the book value of the investment at the end of each year, the net cash flows for each year, and the net income...
-
11. Sinking Fund A company borrows $5000 on which it will pay interest at the end of each year at the annual rate of 11%. In addition, a sinking fund is set up so that the $5000 can be repaid at the...
-
The Merkle-Hellman attack on 3DES begins by assuming a value of A = 0 (Figure 6.1b). Then, for each of the 2 56 possible values of K 1 , the plaintext P that produces A = 0 is determined. Describe...
-
You want to build a hardware device to do block encryption in the cipher block chaining (CBC) mode using an algorithm stronger than DES. 3DES is a good candidate. Figure 6.11 shows two possibilities,...
-
A. Explain two differences between financial accounting and management accounting. B. Give three reasons why capital investment decisions are particularly important to business.
-
A typical AA battery delivers a nearly constant voltage of 1.5 V and stores about 104 J of energy. From the time it takes you to use up the batteries in your calculator. Estimate the resistance of...
-
Both marketing and marketing communication are changing rapidly. New tools and methods are coming up and especially due t o changes in technology and the consumers themselves. Despite all these...
-
Discuss a situation where communication is important. This can be in your daily life, your work life, or in your academic life. Describe your own personal communication style preferences in the...
-
A high voltage resistive divider has bandwidth of 75 MHz. Can this divider be used for monitoring voltage signals shorter than 1.5 ns? Justify your answer?
-
Provide practical tips and strategies to improve communication with individuals with hearing disabilities. This could include using visual aids, gestures, and facial expressions, using assistive...
-
At December 31, 2010, the trial balance of Stine Company contained the following amounts before adjustment. Instructions (a) Based on the information given, which method of accounting for bad debts...
-
7. FALSE DILEMMA 8. GANDWAGON Definition: Fallacy example: How to revise argument: Definition: Fallacy example: How to revise argument:
-
Table shows the process states for the VAX/VMS operating system. a. Can you provide a justification for the existence of so many distinct wait states? b. Why do the following states not have resident...
-
The VAX/VMS operating system makes use of four processor access modes to facilitate the protection and sharing of system resources among processes. The access mode determines Instruction execution...
-
The VMS scheme discussed in the preceding problem is often referred to as a ring protection structure, as illustrated in Figure. Indeed, the simple kernel/user scheme, as described in Section 3.3, is...
-
When young adults leave their parental home to go to college or find employment in a distant part of the country, they face the challenge of establishing new social relationships --one that is not...
-
Although all departments of an organization should work toward a common goal, there are often conflicting objectives. For example, finance wants to keep costs down, whereas the design team wants to...
-
Provide a detailed case study The risks from smoking tobacco are well documented and according to the (WHO), the tobacco epidemic is one of the biggest public health threats the world has ever faced,...

Study smarter with the SolutionInn App


