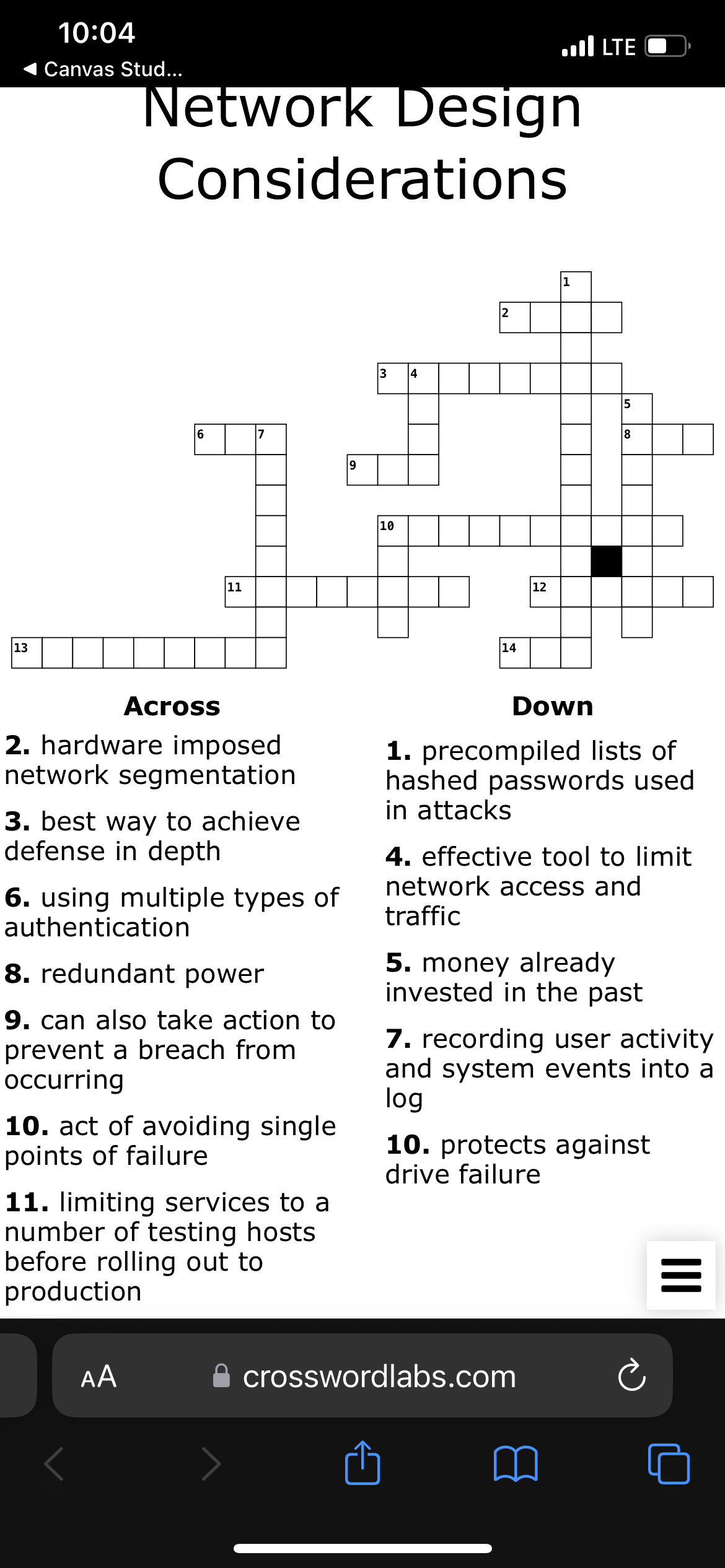
Question: 1 0 : 0 4 . ull LTE Canvas Stud... Network Design Considerations 2 . hardware imposed network segmentation 3 . best way to achieve
:
ull LTE
Canvas Stud...
Network Design
Considerations
hardware imposed network segmentation
best way to achieve defense in depth
using multiple types of authentication
redundant power
can also take action to prevent a breach from occurring
act of avoiding single points of failure
limiting services to a number of testing hosts before rolling out to production
precompiled lists of hashed passwords used in attacks
effective tool to limit network access and traffic
money already invested in the past
recording user activity and system events into a
protects against drive failure
AA
crosswordlabs.com
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


