Question: 1. Using the 2-way set associative D-cache depicted below; give the result of the following memory accesses. These memory accesses are byte fetches. a. The
1. Using the 2-way set associative D-cache depicted below; give the result of the following memory accesses. These memory accesses are byte fetches.
a. The result should be in the format of H: (hit), CM: (compulsory miss) or M: (miss).
b. Use the LRU replacement policy; assuming that 0 denotes LRU and 1 denotes MRU.
c. If you replace a block, assume that only the tag is changed and the data (marked as X) is unchanged.
d. All numeric values are in hexadecimal.
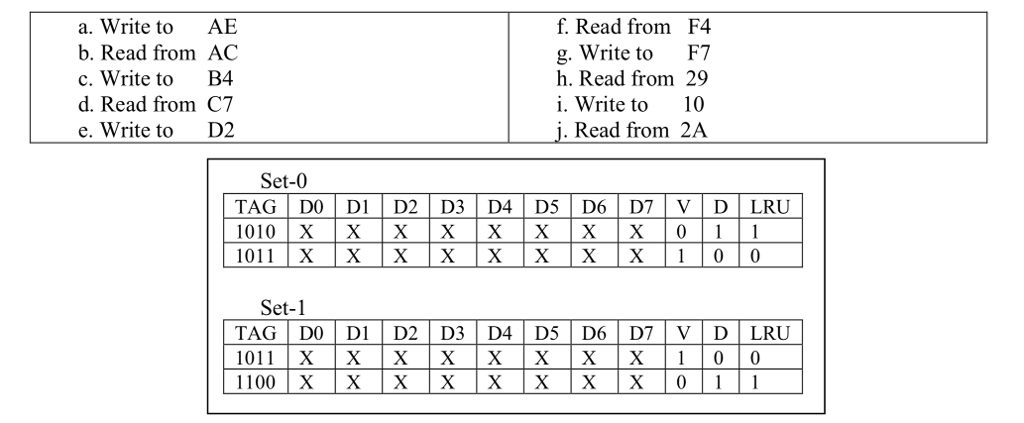
a. Write to AE b. Read from AC c. Write to B4 d. Read from C7 e. Write to D2 f. Read from F4 g. Write to F7 h. Read from 29 i. Write to 10 j. Read from 2A Set-0 TAG I DO | D1 | D2 | D3 | D4 | D5 | D6 | D7 | V | D | LRU 1010 XXXXXXXX01 1011 X X XX X X X X 1 0 0 Set-1 TAG | DO | DI | D2 | D3 | D4 | D5 | D6 | D7 | V | D LRU a. Write to AE b. Read from AC c. Write to B4 d. Read from C7 e. Write to D2 f. Read from F4 g. Write to F7 h. Read from 29 i. Write to 10 j. Read from 2A Set-0 TAG I DO | D1 | D2 | D3 | D4 | D5 | D6 | D7 | V | D | LRU 1010 XXXXXXXX01 1011 X X XX X X X X 1 0 0 Set-1 TAG | DO | DI | D2 | D3 | D4 | D5 | D6 | D7 | V | D LRU
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


