Question: 1. What attacking techniques ( more than 1 ) have been used in the following screenshot. Explain how the attack proceeded. 2. From
1. What attacking techniques (more than 1) have been used in the following screenshot. Explain how the attack proceeded.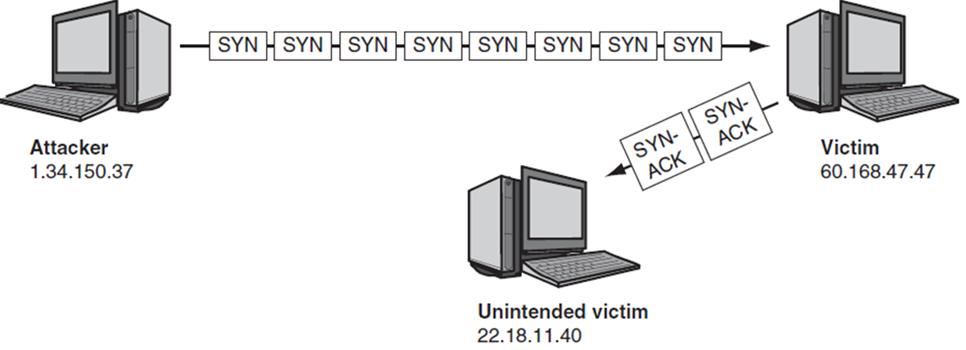 2. From the following screenshot, what kind of device is circled with red? Simply answer the name of the firewall won't give you any marks. You must explain how you determined that.
2. From the following screenshot, what kind of device is circled with red? Simply answer the name of the firewall won't give you any marks. You must explain how you determined that.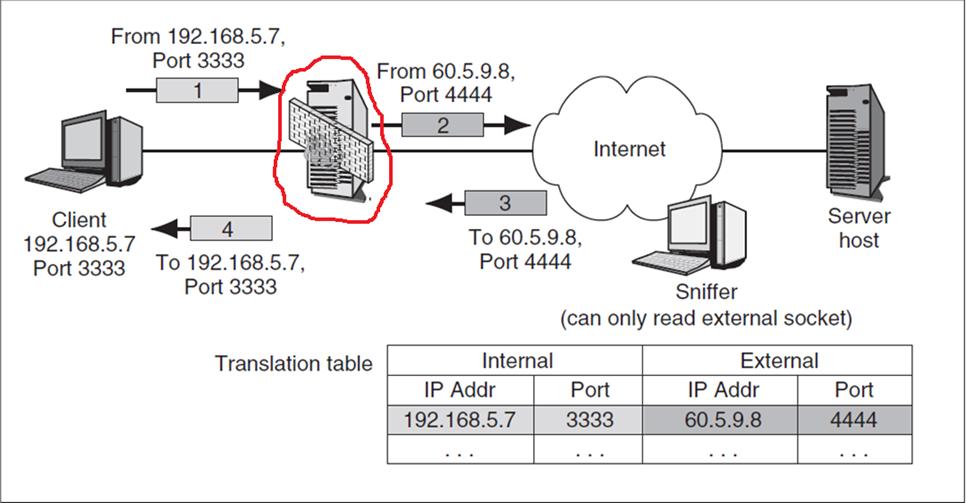
 4. What is the possible situation(s) of the following screenshot referred to? What the attacker is trying to get? How does the victim mitigate the issue? List and explain at least 3 mitigation items could be applied.
4. What is the possible situation(s) of the following screenshot referred to? What the attacker is trying to get? How does the victim mitigate the issue? List and explain at least 3 mitigation items could be applied.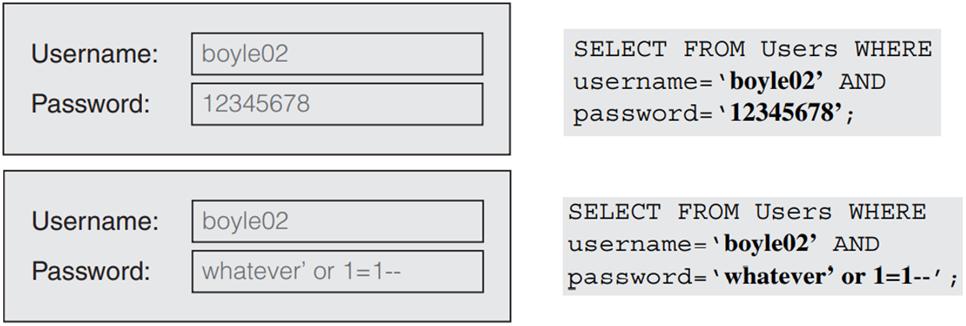
Attacker 1.34.150.37 SYNSYN SYN SYNSYN - SYN SYN - SYN | SYN- ACK Unintended victim 22.18.11.40 SYN- ACK Victim 60.168.47.47
Step by Step Solution
3.40 Rating (159 Votes )
There are 3 Steps involved in it
1 From the screenshots provided The first screenshot shows a SYN flood attack The attacker is sending a flood of SYN packets part of the TCP handshake to the victims server in an attempt to overwhelm ... View full answer

Get step-by-step solutions from verified subject matter experts


