Question: 2rd question: propose a fix for the vulnerability, along with a short explanation why the fix works. For the fix, think about how Bob can
 2rd question: propose a fix for the vulnerability, along with a short explanation why the fix works.
2rd question: propose a fix for the vulnerability, along with a short explanation why the fix works.
For the fix, think about how Bob can be sure that the sender is actually Alice and not Eve.
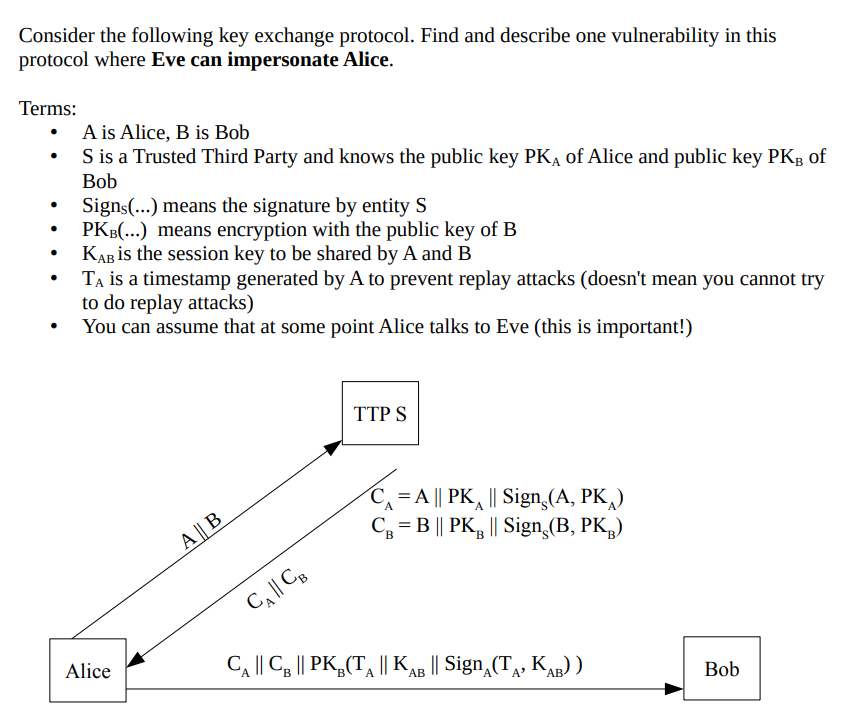
Consider the following key exchange protocol. Find and describe one vulnerability in this protocol where Eve can impersonate Alice. Terms: - A is Alice, B is Bob - S is a Trusted Third Party and knows the public key PKA of Alice and public key PKB of Bob - Sign S() means the signature by entity S - PKB() means encryption with the public key of B - KAB is the session key to be shared by A and B - TA is a timestamp generated by A to prevent replay attacks (doesn't mean you cannot try to do replay attacks) - You can assume that at some point Alice talks to Eve (this is important!)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


