Question: Need Help With Finding and Describing the vulnerability in case below. Problem 4 (10 points) Consider the following key exchange protocol. Find and describe one
Need Help With Finding and Describing the vulnerability in case below.
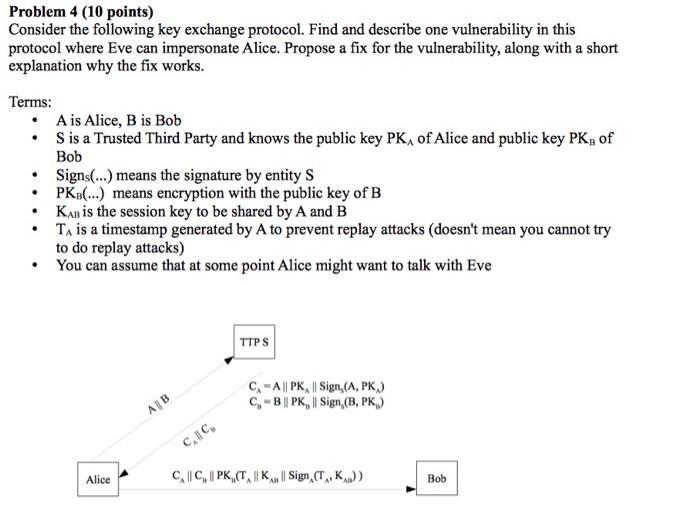
Problem 4 (10 points) Consider the following key exchange protocol. Find and describe one vulnerability in this protocol where Eve can impersonate Alice. Propose a fix for the vulnerability, along with a short explanation why the fix works. Terms: A is Alice, B is Bob Sis a Trusted Third Party and knows the public key PKA of Alice and public key PK, of Bob Signs(...) means the signature by entity S PK (...) means encryption with the public key of B Kap is the session key to be shared by A and B TA is a timestamp generated by A to prevent replay attacks (doesn't mean you cannot try to do replay attacks) You can assume that at some point Alice might want to talk with Eve . . . TIPS C-A || PK || Sign, (A, PK) C, - B || PK, || Sign (B, PK) | CIC, Alice Cill C, || PK (T, || K | Sign, T., K.) All Bob
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


