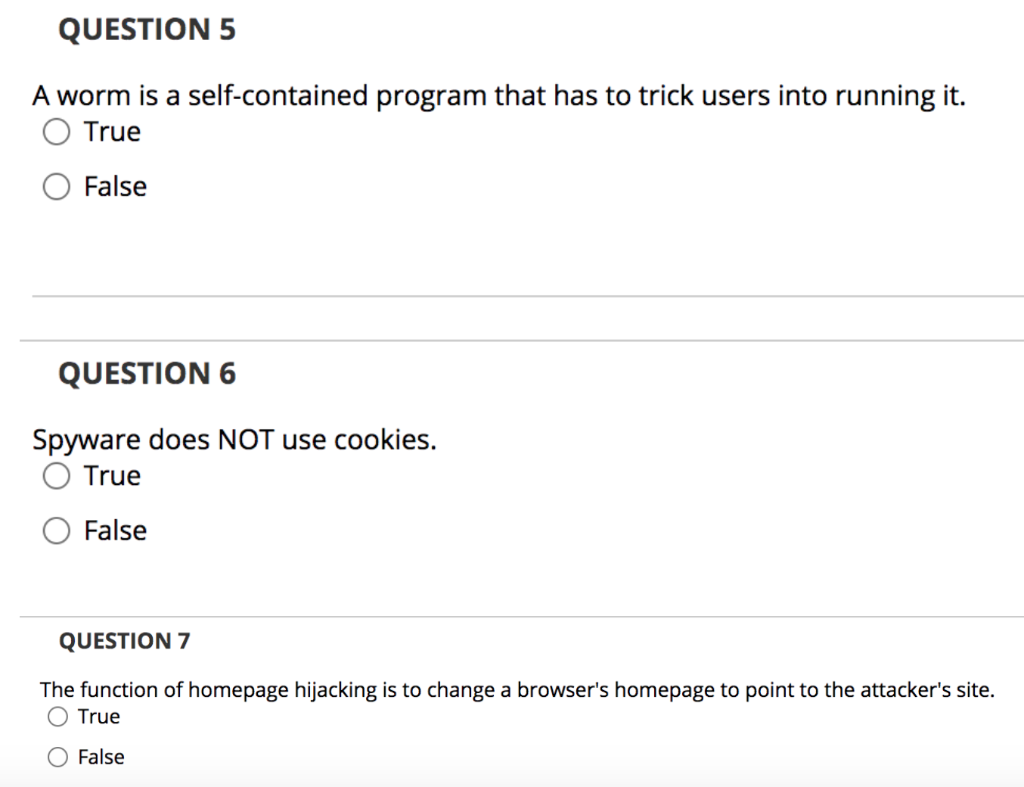
Question: Answer all for a thumbs up! QUESTION 5 A worm is a self-contained program that has to trick users into running it. O True False
 Answer all for a thumbs up!
Answer all for a thumbs up!
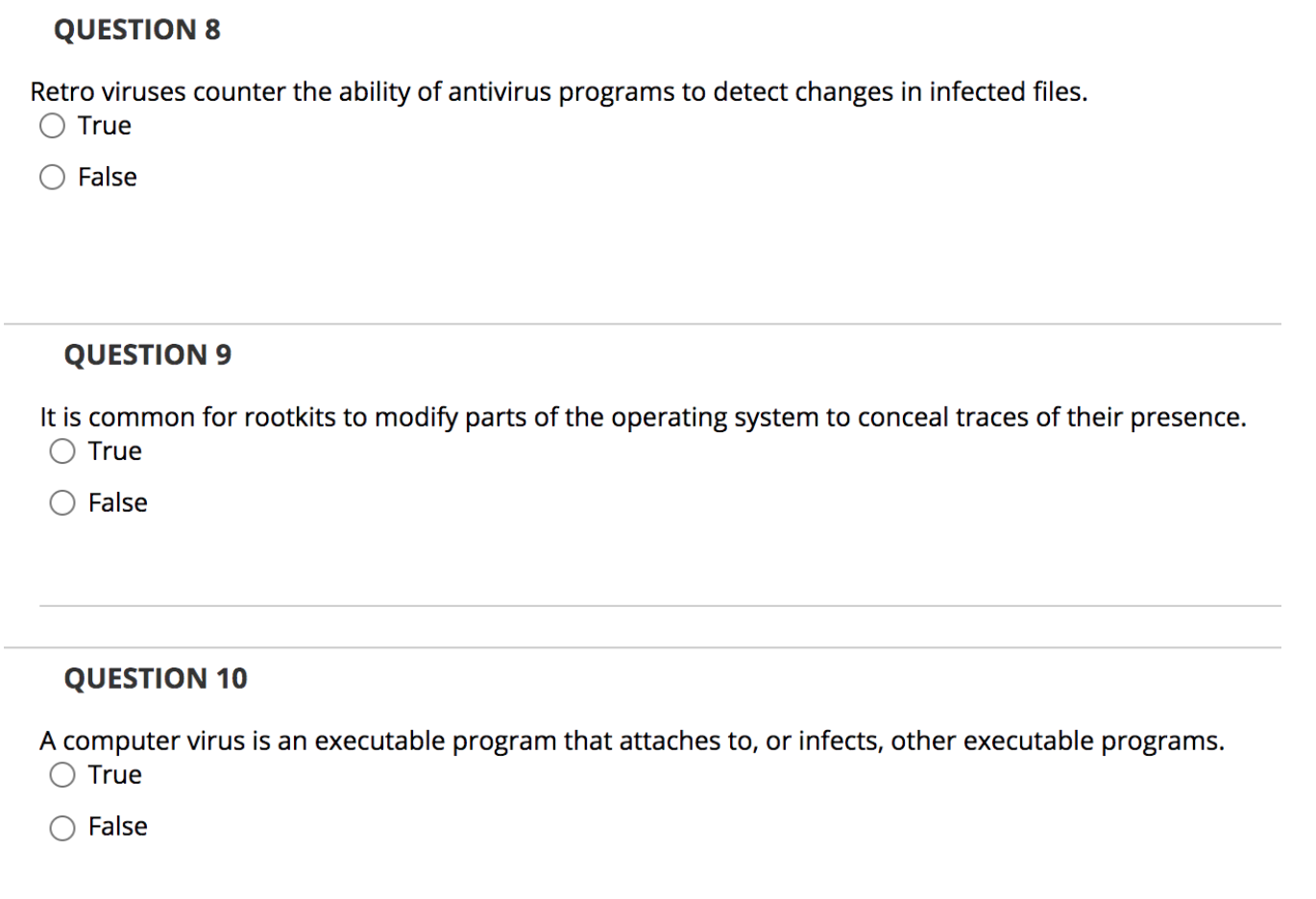
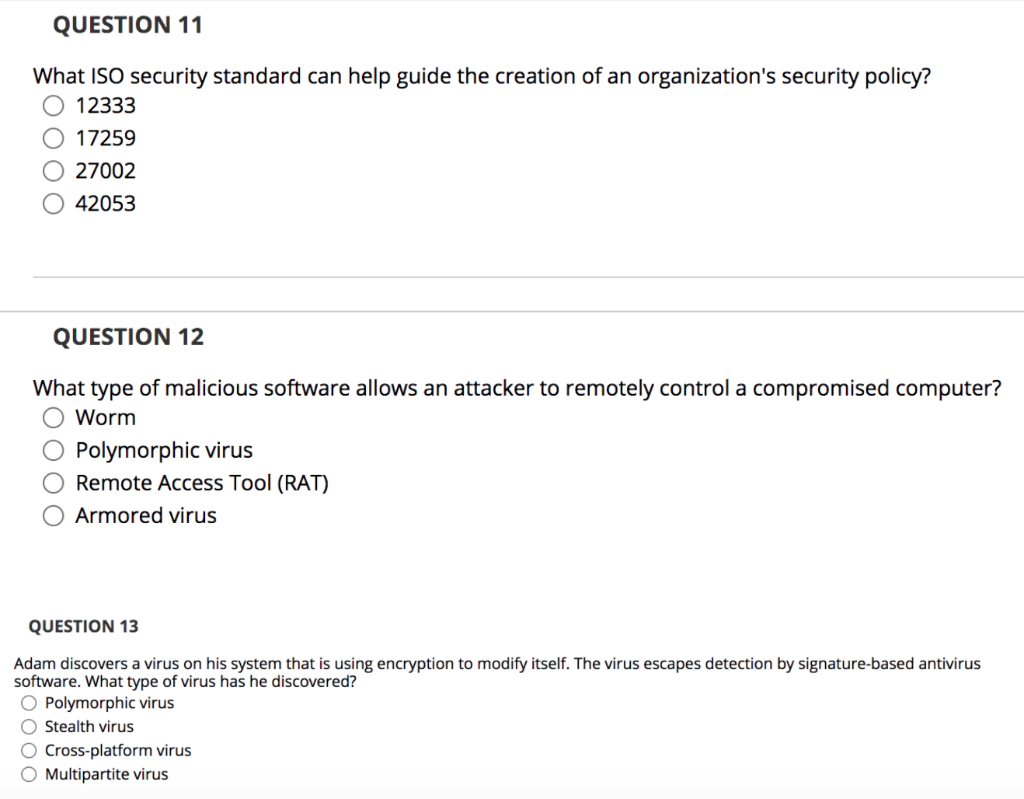
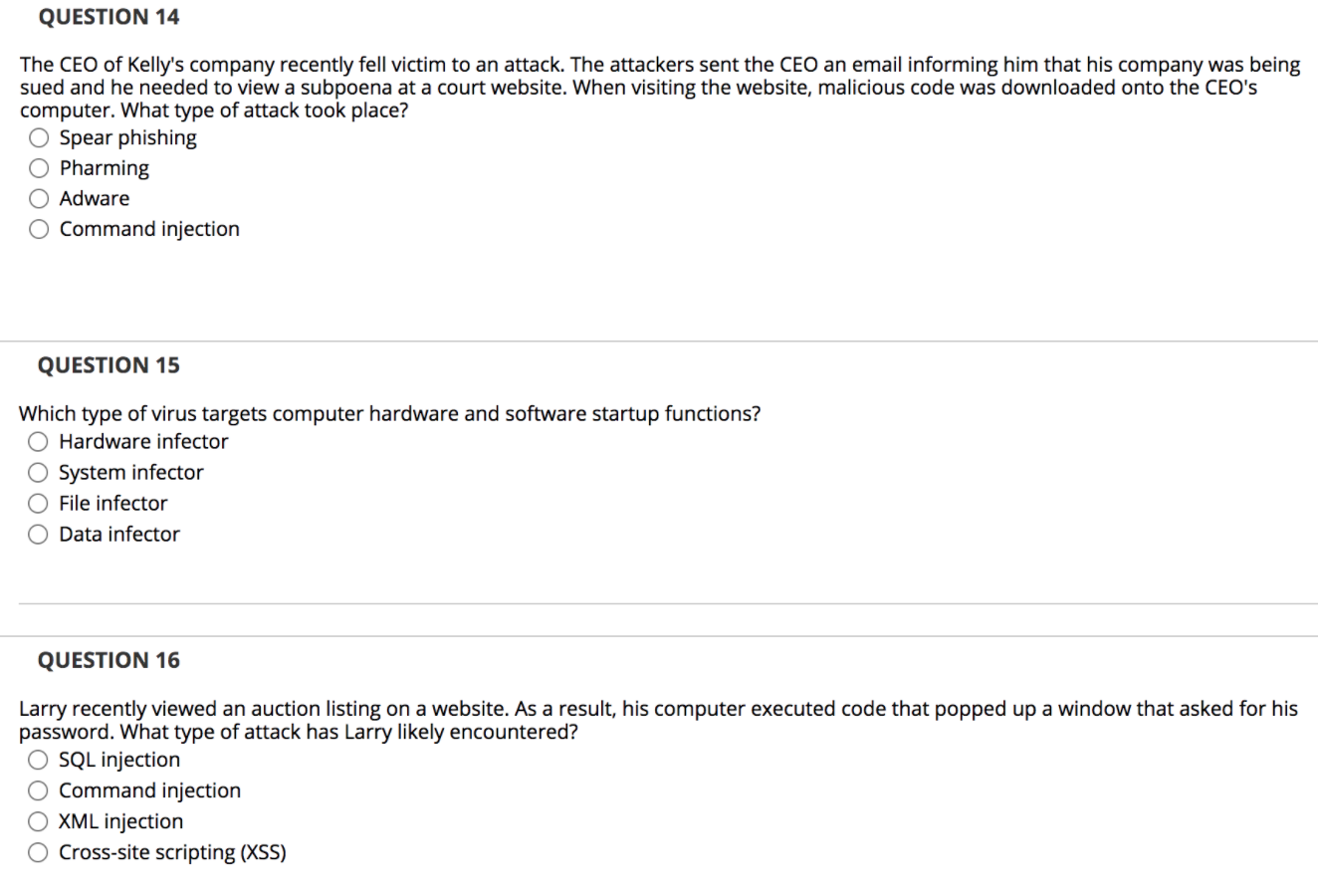
QUESTION 5 A worm is a self-contained program that has to trick users into running it. O True False QUESTION 6 Spyware does NOT use cookies. True False QUESTION 7 The function of homepage hijacking is to change a browser's homepage to point to the attacker's site. True False QUESTION 8 Retro viruses counter the ability of antivirus programs to detect changes in infected files. True False QUESTION 9 It is common for rootkits to modify parts of the operating system to conceal traces of their presence. True False QUESTION 10 A computer virus is an executable program that attaches to, or infects, other executable programs. True False QUESTION 11 What ISO security standard can help guide the creation of an organization's security policy? 12333 O 17259 O 27002 O 42053 QUESTION 12 What type of malicious software allows an attacker to remotely control a compromised computer? Worm Polymorphic virus Remote Access Tool (RAT) Armored virus QUESTION 13 Adam discovers a virus on his system that is using encryption to modify itself. The virus escapes detection by signature-based antivirus software. What type of virus has he discovered? O Polymorphic virus O Stealth virus O Cross-platform virus O Multipartite virus QUESTION 14 The CEO of Kelly's company recently fell victim to an attack. The attackers sent the CEO an email informing him that his company was being sued and he needed to view a subpoena at a court website. When visiting the website, malicious code was downloaded onto the CEO's computer. What type of attack took place? O Spear phishing Pharming Adware Command injection QUESTION 15 Which type of virus targets computer hardware and software startup functions? O Hardware infector O System infector O File infector Data infector QUESTION 16 Larry recently viewed an auction listing on a website. As a result, his computer executed code that popped up a window that asked for his password. What type of attack has Larry likely encountered? O SQL injection O Command injection O XML injection Cross-site scripting (XSS) QUESTION 17 Alison discovers that a system under her control has been infected with malware, which is using a key logger to report user keystrokes to a third party. What information security property is this malware attacking? O Integrity O Availability O Accounting O Confidentiality QUESTION 18 What is NOT a typical sign of virus activity on a system? Unexplained decrease in available disk space O Unexpected error messages O Unexpected power failures O Sudden sluggishness of applications QUESTION 19 Yolanda would like to prevent attackers from using her network as a relay point for a smurf attack. What protocol should she block? O Hypertext Transfer Protocol (HTTP) O Transmission Control Protocol (TCP) O Internet Control Message Protocol (ICMP) O User Datagram Protocol (UDP) QUESTION 20 Bob is developing a web application that depends upon a database backend. What type of attack could a malicious individual use to send commands through his web application to the database? O Cross-site scripting (XSS) O XML injection O SQL injection OLDAP injection
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


