Question: Binary Bomb Lab Phase 2. I know the answer is a six digit with spaces between (i.e. %d %d %d %d %d %d ). Please
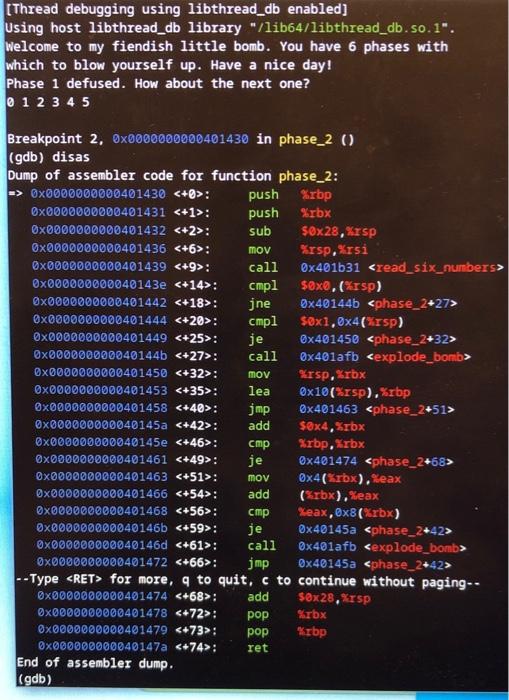
[Thread debugging using libthread_db enabled] Using host libthread_db library "/lib64/libthread_db.so.1". Welcome to my fiendish little bomb. You have 6 phases with which to blow yourself up. Have a nice day! Phase 1 defused. How about the next one? 012345 Breakpoint 2, 0x0000000000401430 in phase_2 () (gdb) disas Dump of assembler code for function phase_2: 0000000000401430 : push \%rbp 0x0000000000401431 +1>: push Krbx 00000000000401432+2>: sub 5028, xrsp 0x0000000000401436 +6>: mov Krsp, \%rsi 0x0000000000401439 +9>: call 0x401b31 0x000000000040143e +14>: cmpl soxe, (xrsp) 0x0000000000401442 +18>: jne 040144b 0x0000000000401444 : cmpl 501,04 (xrsp) 00000000000401449: je 0401450 0x000000000040144b +27>: call 0x401afb 0x0000000000401450 +32>: mov Krsp, Krbx 00000000000401453: lea 010( irpp), \%rbp 00000000000401458+40>: jmp 0x401463 0000000000040145a : add $04,5rbx 0000000000040145e \&46>: :mp Xrbp, Krbx 0x0000000000401461 : je 0401474 00000000000401463 : mov 04( \%rbx), Reax 00000000000401466: add ( rrbx), Yeax 00000000000401468 : cmp xeax, 0x8 (xrbx) 0x000000000040146b +59>: je 0x40145a phase_2+42> 0x000000000040146d : call ex401afb 0x0000000000401472 +66>: jmp 0x40145a - Type for more, q to quit, c to continue without paging.00000000000401474 s+68>: add s0x28, \%r sp 0x0000000000401478 +72>: pop \%rbx 0x0000000000401479 +73>: pop x : prp 0000000000040147a +74>: ret End of assembler dump. (gdb)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


