Question: Buffer Overflow Your task is to exploit a buffer - overflow in function f of code provided to you in file ex 1 . c
Buffer Overflow
Your task is to exploit a bufferoverflow in function f of code provided to you in file exc use the
Makefile to compile it You are not allowed to change the source code. The program receives three
arguments: your first and last name and the name of a file. The function f reads the content of that file
but doesn't check if there is enough space for all contents of the file.
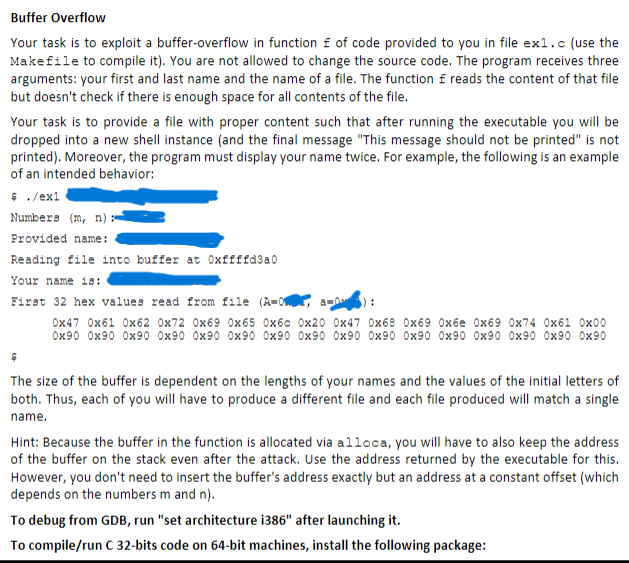
Your task is to provide a file with proper content such that after running the executable you will be
dropped into a new shell instance and the final message "This message should not be printed" is not
printed Moreover, the program must display your name twice. For example, the following is an example
of an intended behavior:
The size of the buffer is dependent on the lengths of your names and the values of the initial letters of
both. Thus, each of you will have to produce a different file and each file produced will match a single
name.
Hint: Because the buffer in the function is allocated via alloca, you will have to also keep the address
of the buffer on the stack even after the attack. Use the address returned by the executable for this.
However, you don't need to insert the buffer's address exactly but an address at a constant offset which
depends on the numbers m and n
To debug from GDB run "set architecture i after launching it
PLEASE SOLVE AND SHOW STEPS FROM TERMINAL
exc:
#include
#include
#include
void fint n int m char str
FILE f fopenstrr;
char bufn;
sizet pos;
if m n
fprintfstderr "Invalid call of f
;
exitEXITFAILURE;
if f NULL
perrorInvalid file with buffer";
exitEXITFAILURE;
printfReading file into buffer at p
buf;
fseekf SEEKEND;
pos ftellf;
fseekf SEEKSET;
here's the bug: pos should be at most n for legit calls
freadbuf sizeofbuf pos, f;
bufm;
printfYour name is: s
buf;
printfFirst hex values read from file Ax ax:;
for pos ; pos ; pos
if pos
printf
t;
printfxx unsigned charbufpos;
printf
;
int mainint argc, char argv
int m n;
if argc
fprintfstderr "Usage: ex firstname lastname filename
;
exitEXITFAILURE;
m argvAargvA;
if m m m;
n strlenargv strlenargv;
if m n m n ;
if m m ;
if n n ;
fprintfstdout "Numbers m n: d d
m n;
fprintfstdout "Provided name: s s
argv argv;
fm n argv;
printfThis message should not be printed
;
return ;
makefile:
PHONY: all clean md
TARGET ex
CC gcc
CFLAGS Wall Wextra g fnostackprotector mz execstack
LDFLAGS fnostackprotector mz execstack
all: md
md: $TARGET
mdsum $TARGET
clean:
$RM $TARGET
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


