Question: can you please write a program in JAVA (cryptography) Write a program that performs the simplified DES-type algorithm presented in Section 4.2 of the textbook.
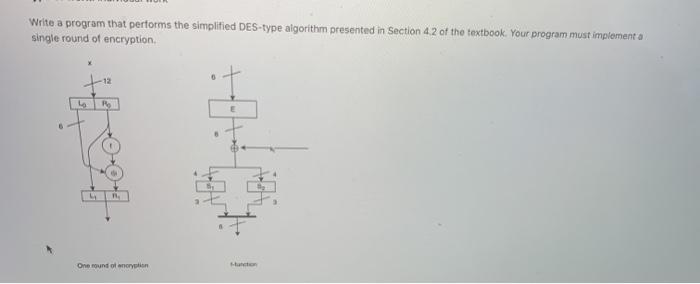
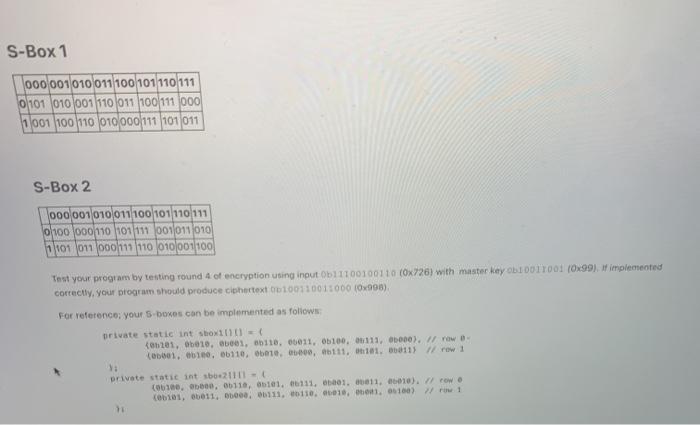
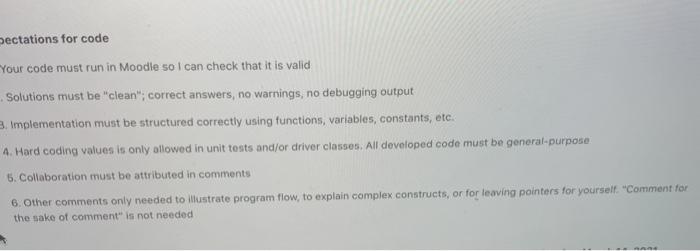
Write a program that performs the simplified DES-type algorithm presented in Section 4.2 of the textbook. Your program most implementa single round of encryption 0 LR 6 L One round of any S-Box 1 000 001010011 100101 110111 0101 010 001110011 100111.000 1 11001 100 110 010 000111 101011 S-Box 2 000 001010011 100 101 1011 choo 0110 10111 001011010 01 01 ooohm/110 0101001100 Test your program by testing round 4 of encryption using input 011100100110 (Ox726) with master key biolT001 (Ox99), implemented correctly, your program should produce cihettext 00100110011000 (0x900) For reference; your S-boxes can be implemented as follows: private static int show11111 = kone1, b010, 0, 60118, 06011, 0100, 00111, 000). W row (0601. 0100, 06110, 0, 0, 111, 101. 06011) row 1 private static int so2111 (06100, 60, 611, 101.6111. 01. 011, 06010). 1 row ob101, 0011, 000, 06111, 110, 1010, 01. 0100) 1 Sectations for code Your code must run in Moodle so I can check that it is valid Solutions must be "clean"; correct answers, no warnings, no debugging output 3. Implementation must be structured correctly using functions, variables, constants, etc. 4. Hard coding values is only allowed in unit tests and/or driver classes. All developed code must be general-purpose 5. Collaboration must be attributed in comments 6. Other comments only needed to illustrate program flow, to explain complex constructs, or for leaving pointers for yourself. "Comment for the sake of comment is not needed Write a program that performs the simplified DES-type algorithm presented in Section 4.2 of the textbook. Your program most implementa single round of encryption 0 LR 6 L One round of any S-Box 1 000 001010011 100101 110111 0101 010 001110011 100111.000 1 11001 100 110 010 000111 101011 S-Box 2 000 001010011 100 101 1011 choo 0110 10111 001011010 01 01 ooohm/110 0101001100 Test your program by testing round 4 of encryption using input 011100100110 (Ox726) with master key biolT001 (Ox99), implemented correctly, your program should produce cihettext 00100110011000 (0x900) For reference; your S-boxes can be implemented as follows: private static int show11111 = kone1, b010, 0, 60118, 06011, 0100, 00111, 000). W row (0601. 0100, 06110, 0, 0, 111, 101. 06011) row 1 private static int so2111 (06100, 60, 611, 101.6111. 01. 011, 06010). 1 row ob101, 0011, 000, 06111, 110, 1010, 01. 0100) 1 Sectations for code Your code must run in Moodle so I can check that it is valid Solutions must be "clean"; correct answers, no warnings, no debugging output 3. Implementation must be structured correctly using functions, variables, constants, etc. 4. Hard coding values is only allowed in unit tests and/or driver classes. All developed code must be general-purpose 5. Collaboration must be attributed in comments 6. Other comments only needed to illustrate program flow, to explain complex constructs, or for leaving pointers for yourself. "Comment for the sake of comment is not needed
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


