Question: Consider below user session - The users make requests necessary to perform whatever functions they want and the application provides its responses in fulfilment of
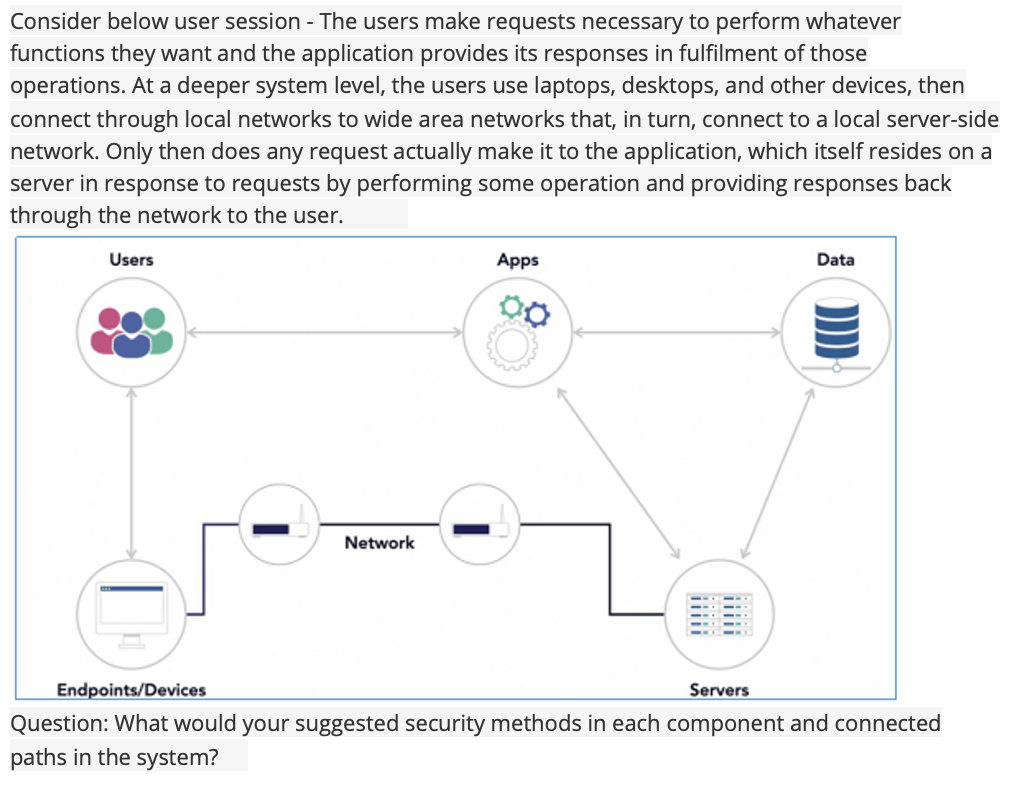
Consider below user session The users make requests necessary to perform whatever
functions they want and the application provides its responses in fulfilment of those
operations. At a deeper system level, the users use laptops, desktops, and other devices, then
connect through local networks to wide area networks that, in turn, connect to a local serverside
network. Only then does any request actually make it to the application, which itself resides on a
server in response to requests by performing some operation and providing responses back
through the network to the user.
Question: What would your suggested security methods in each component and connected
paths in the system?
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


