Question: Encryption Erryption in the proceso mending memega inimton such a way that only antheon partim commodit. Here, we will look at a simple method of
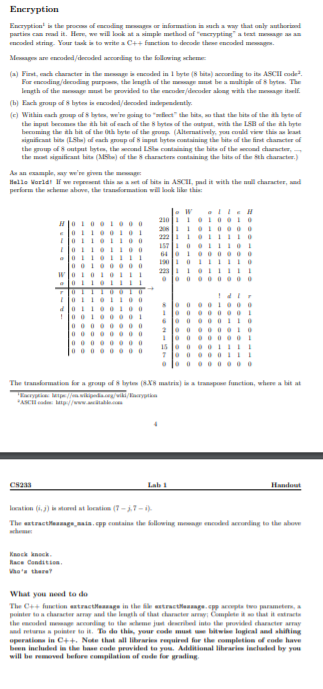
Encryption Erryption in the proceso mending memega inimton such a way that only antheon partim commodit. Here, we will look at a simple method of cryptinga testa coded string Your tak to write a C++ function to decade the coded mango Meaded/decoded according to the following (a) First, ma character in the smagscoded in 1 byte ( hita) ceding to it ASCII code? For coding decoding purpower, the best of the most be a multiple of byte. The length of the most be provided to the audiedecade alog with the maitself. (1) Ech group of the wedding (c) Within each map of time, we're going to the that the hits of the best of the input become theith bit of each of the bytes of the crapat, with these of theith byte becoming the ih bit of the the byter of the group (Altstily, you could view the last significant te LSL) of each group of input last containing the that of the first cance of the group of 8 outpat liste, the cod LScontaining the lata of the conducte, ther at kigaitirant lata (MS) of the characters staining the hits of the sth character.) As an example, we're in the Hello world! If we rupt this wat of bits in ASCII, and it with the wall cluster, and perform the cars have the most will look like this HOLBOLOOG 2101 TOLOGIO 20 .... 22:!!!!!! s!!!!! !!! OOOOOOOOO The traumatice sroup of byte (8X8 matrix) is a trapefruction, where a bit ut Beykeltp//.wikipedia.org/wiki/ Hot lati (1) locatie (7-17- The strategic the bed ning to the Knock knock Race Condition Who's there? What you need to do The C++ atractage in the structumge.cppp women, d tlar lauthal ilai thurate that in aminate the model and to the home thrribed into the provided the wa mapoker to it. To do this, your codem lite Ingla and hiking operation in C++. Note that all liber required for the completion of code have be included in the head provided to you. Additional learned by you will be removed before compilation of code for grading Encryption Erryption in the proceso mending memega inimton such a way that only antheon partim commodit. Here, we will look at a simple method of cryptinga testa coded string Your tak to write a C++ function to decade the coded mango Meaded/decoded according to the following (a) First, ma character in the smagscoded in 1 byte ( hita) ceding to it ASCII code? For coding decoding purpower, the best of the most be a multiple of byte. The length of the most be provided to the audiedecade alog with the maitself. (1) Ech group of the wedding (c) Within each map of time, we're going to the that the hits of the best of the input become theith bit of each of the bytes of the crapat, with these of theith byte becoming the ih bit of the the byter of the group (Altstily, you could view the last significant te LSL) of each group of input last containing the that of the first cance of the group of 8 outpat liste, the cod LScontaining the lata of the conducte, ther at kigaitirant lata (MS) of the characters staining the hits of the sth character.) As an example, we're in the Hello world! If we rupt this wat of bits in ASCII, and it with the wall cluster, and perform the cars have the most will look like this HOLBOLOOG 2101 TOLOGIO 20 .... 22:!!!!!! s!!!!! !!! OOOOOOOOO The traumatice sroup of byte (8X8 matrix) is a trapefruction, where a bit ut Beykeltp//.wikipedia.org/wiki/ Hot lati (1) locatie (7-17- The strategic the bed ning to the Knock knock Race Condition Who's there? What you need to do The C++ atractage in the structumge.cppp women, d tlar lauthal ilai thurate that in aminate the model and to the home thrribed into the provided the wa mapoker to it. To do this, your codem lite Ingla and hiking operation in C++. Note that all liber required for the completion of code have be included in the head provided to you. Additional learned by you will be removed before compilation of code for grading
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


