Question: Full soft, Inc. is a large software development company based in New York City. Full soft's software product development code is kept confidential in an
Full soft, Inc. is a large software development company based in New York City. Full soft's software product development code is kept confidential in an effort to safeguard the company's competitive advantage in the marketplace. You are a security professional who reports into Full soft's infrastructure operations team.
Full soft's chief security officer (CSO) wants analysis performed and a high-level plan created to mitigatefuture risks, threats, and vulnerabilities. As part of this request, you and your team members will design a plan for performing a gap analysis. An IT gap analysis may be a formal investigation or an informal survey of an organization's overall IT security. The first step of a gap analysis is to compose clear objectives and goals concerning an organization's IT security. For each objective or goal, the person performing the analysis must gather information about the environment, determine the present status, and identify what must be changed to achieve goals. The analysis most often reveals gaps in security between "where you are" and "where you want to be."
Scenario:
Future IT is an IT company which provide different IT services such as application development, technicalissues resolution, software support, Internet services, database services and others. It is operating all acrossAustraliawiththebranches in majorcitiessuchasMelbourne,Sydney,Perth andBrisbane.
It has around 133,240 clients and has been providing services to them from the last five years. The company hasbeenconsistent withprovidingservices andis givingtoughcompetitionin the industry.
Future IT has a large database of employees and customer, which contain sensitive information. If thesensitive information is breached, it will impact not only customers but will also impact the organizationreputationinthemarket.
Future IT have an orthodox incident response plan strategy which was developed five years ago and has notbeen updated since then. The incident response doesn't cover most of the key points which need to becovered incaseofan incident.
Theincident responseplanof FutureIt isgivenbelow:
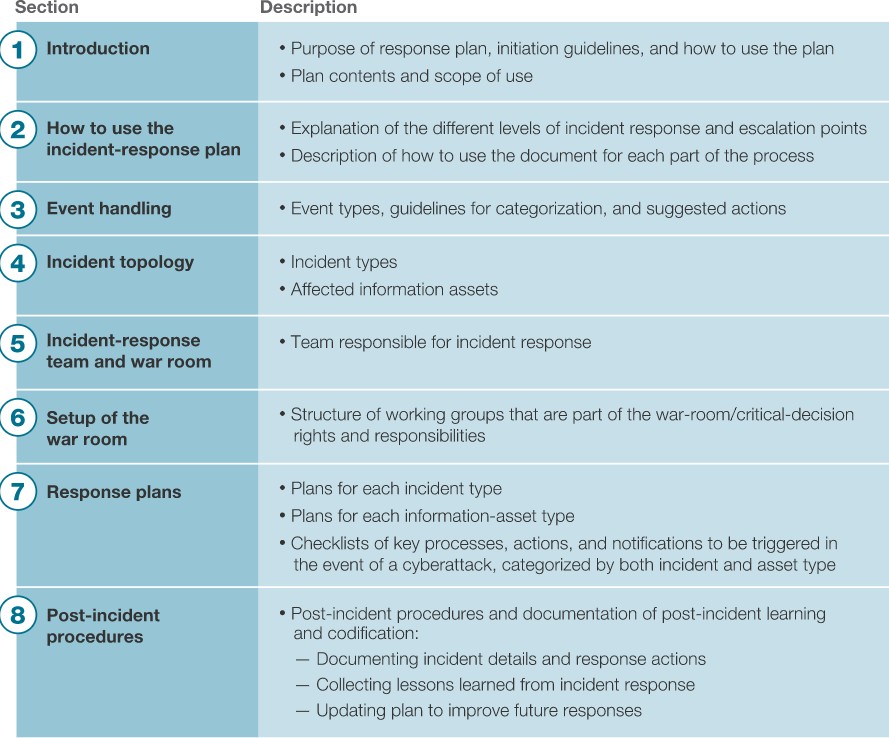          |
Section 1 Introduction 2) How to use the incident-response plan 3) Event handling 4) Incident topology 5) Incident-response team and war room 6) Setup of the war room 7) Response plans (8) Post-incident procedures Description Purpose of response plan, initiation guidelines, and how to use the plan Plan contents and scope of use Explanation of the different levels of incident response and escalation points Description of how to use the document for each part of the process Event types, guidelines for categorization, and suggested actions Incident types Affected information assets Team responsible for incident response Structure of working groups that are part of the war-room/critical-decision rights and responsibilities Plans for each incident type Plans for each information-asset type Checklists of key processes, actions, and notifications to be triggered in the event of a cyberattack, categorized by both incident and asset type Post-incident procedures and documentation of post-incident learning and codification: - Documenting incident details and response actions - Collecting lessons learned from incident response - Updating plan to improve future responses
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


