Question: Hello, i need help solving this question, couldn't solve it NOTE: CIA means confidentiality, Integrity, Availability Should be written in Java No need to write
Hello, i need help solving this question, couldn't solve it
NOTE: CIA means confidentiality, Integrity, Availability
Should be written in Java
No need to write read and write functions, just need the output if it is read or write

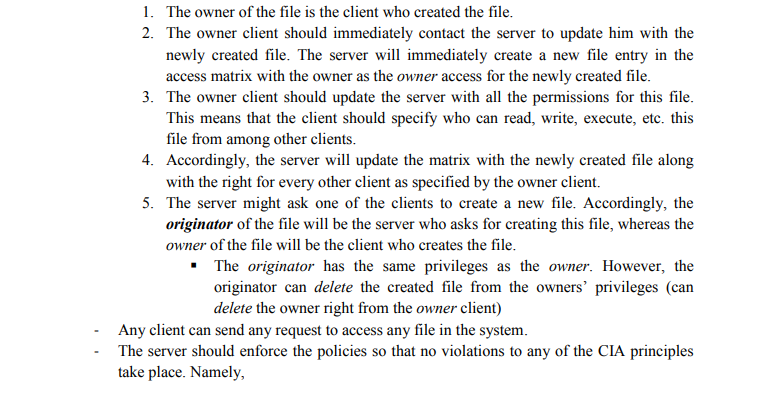

The goal of this assignment is to create a simulated environment that mimics access control principles so that the student will have better understanding of the access control lists System Description Your system will have a centralized server and a set of clients (exactly 5 clients). The server will be the core component in the system. The server will take care of making sure - that no violation of the CIA will take place by enforcing the system policies. 1. One of the clients (Client 1) should represent a parent system. In this case, this client (client 1) has the power over the system. This means that any request that comes from client 1 should have the highest privilege and hence should be enforced regardless of any policy that might be violated. 2. Other clients (client 2, client 3, client 4, and client 5) are just normal users that should be governed by the system for any violation of CIA. 3. Hence, any request should specify the client number as its first parameter. If it i:s client 1 then this has the highest privilege. Other clients should be governed by system policies. (Client#, Req.) An access control matrix should be created in the server side Any client can create any number of files Basic access rights should be supported (read, write, execute, delete, control, etc.) - Upon creation of a new file, the following rules should be enforced The goal of this assignment is to create a simulated environment that mimics access control principles so that the student will have better understanding of the access control lists System Description Your system will have a centralized server and a set of clients (exactly 5 clients). The server will be the core component in the system. The server will take care of making sure - that no violation of the CIA will take place by enforcing the system policies. 1. One of the clients (Client 1) should represent a parent system. In this case, this client (client 1) has the power over the system. This means that any request that comes from client 1 should have the highest privilege and hence should be enforced regardless of any policy that might be violated. 2. Other clients (client 2, client 3, client 4, and client 5) are just normal users that should be governed by the system for any violation of CIA. 3. Hence, any request should specify the client number as its first parameter. If it i:s client 1 then this has the highest privilege. Other clients should be governed by system policies. (Client#, Req.) An access control matrix should be created in the server side Any client can create any number of files Basic access rights should be supported (read, write, execute, delete, control, etc.) - Upon creation of a new file, the following rules should be enforced
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


