Question: i) Explaining how the attack as shown in Figure 2 works ii) Presenting a solution to address this attack PREMISE Alice's public key is KA,
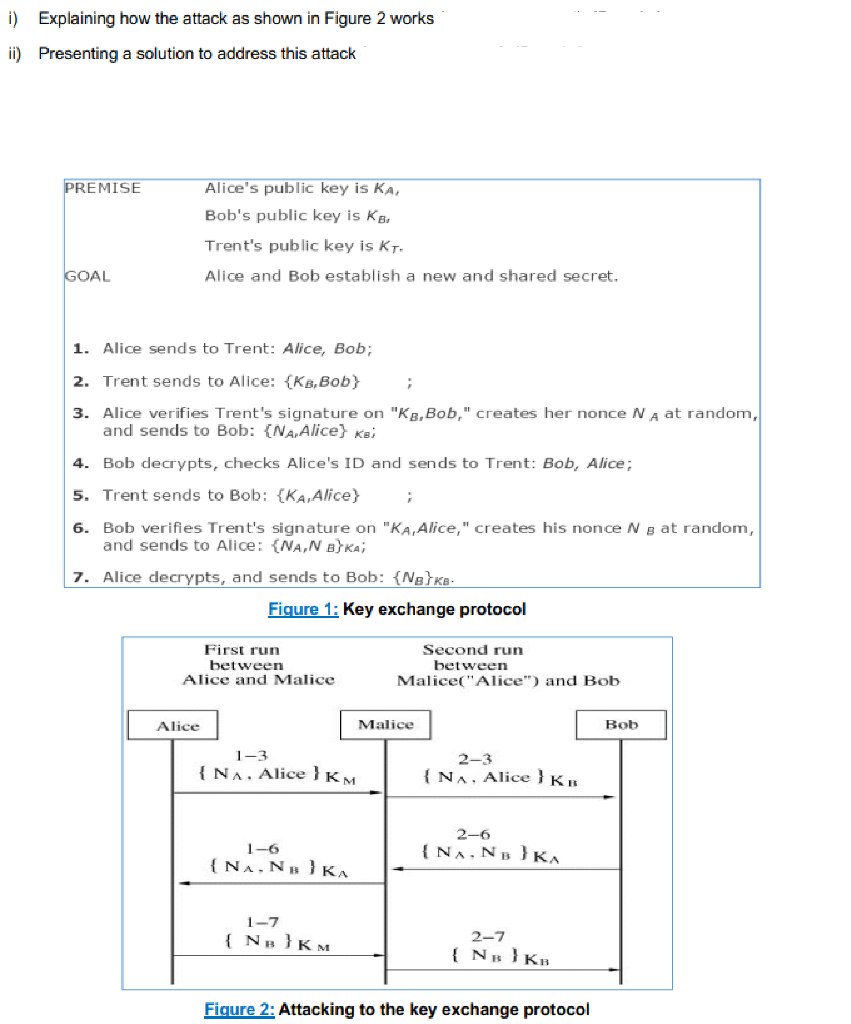
i) Explaining how the attack as shown in Figure 2 works ii) Presenting a solution to address this attack PREMISE Alice's public key is KA, Bob's public key is kB. Trent's public key is KT. Alice and Bob establish a new and shared secret. GOAL 1. Alice sends to Trent: Alice, Bob; 2. Trent sends to Alice: {KB,Bob} 3. Alice verifies Trent's signature on "Kg,Bob," creates her nonce N A at random, and sends to Bob: {NA, Alice) Kei Bob decrypts, checks Alice's ID and sends to Trent: Bob, Alice; 5. Trent sends to Bob: {KA, Alice} 6. Bob verifies Trent's signature on "KA, Alice,"creates his nonce Ng at random, and sends to Alice: NAN B) KA; 7. Alice decrypts, and sends to Bob: {Neke- Figure 1: Key exchange protocol First run between Alice and Malice Second run between Malice("Alice") and Bob Alice Malice Bob 1-3 { Na. Alice } KM 2-3 {NA. Alice } KR 1-6 {NA.NBK 2-6 {NAN KA 1-7 { NE } KM 2-7 {N} KR Figure 2: Attacking to the key exchange protocol
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


