Question: I need a solution ASAP please Problem 5: Taint analysis and security vulnerabilities The following diagram outlines the states used to track whether a variable
I need a solution ASAP please 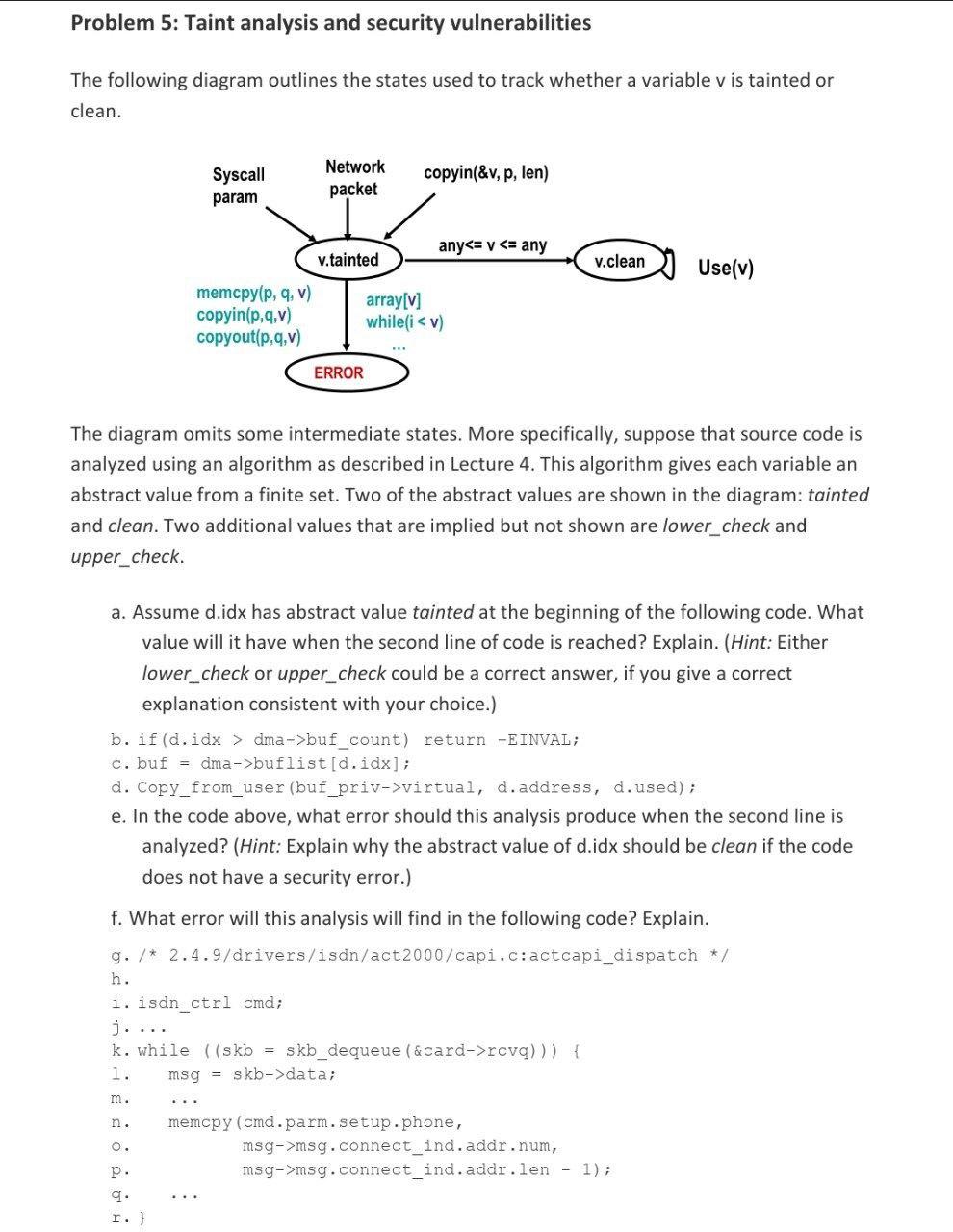
Problem 5: Taint analysis and security vulnerabilities The following diagram outlines the states used to track whether a variable v is tainted or clean. Syscall param Network packet copyin(&v, p, len) v.clean Use(v) any dma->buf_count) return -EINVAL; c. buf = dma->buflist[d.idx]; d. Copy_from_user (buf_priv->virtual, d.address, d.used); e. In the code above, what error should this analysis produce when the second line is analyzed? (Hint: Explain why the abstract value of d.idx should be clean if the code does not have a security error.) f. What error will this analysis will find in the following code? Explain. g. /* 2.4.9/drivers/isdn/act2000/capi.c:actcapi_dispatch */ h. i. isdn_ctrl cmd; j.... k. while ((skb = skb_dequeue (& card->rcvq))) { 1. msg = skb->data; m. n. O. memcpy(cmd.parm.setup.phone, msg->msg.connect_ind.addr.num, msg->msg.connect_ind.addr.len - 1); p. 9. r.)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


