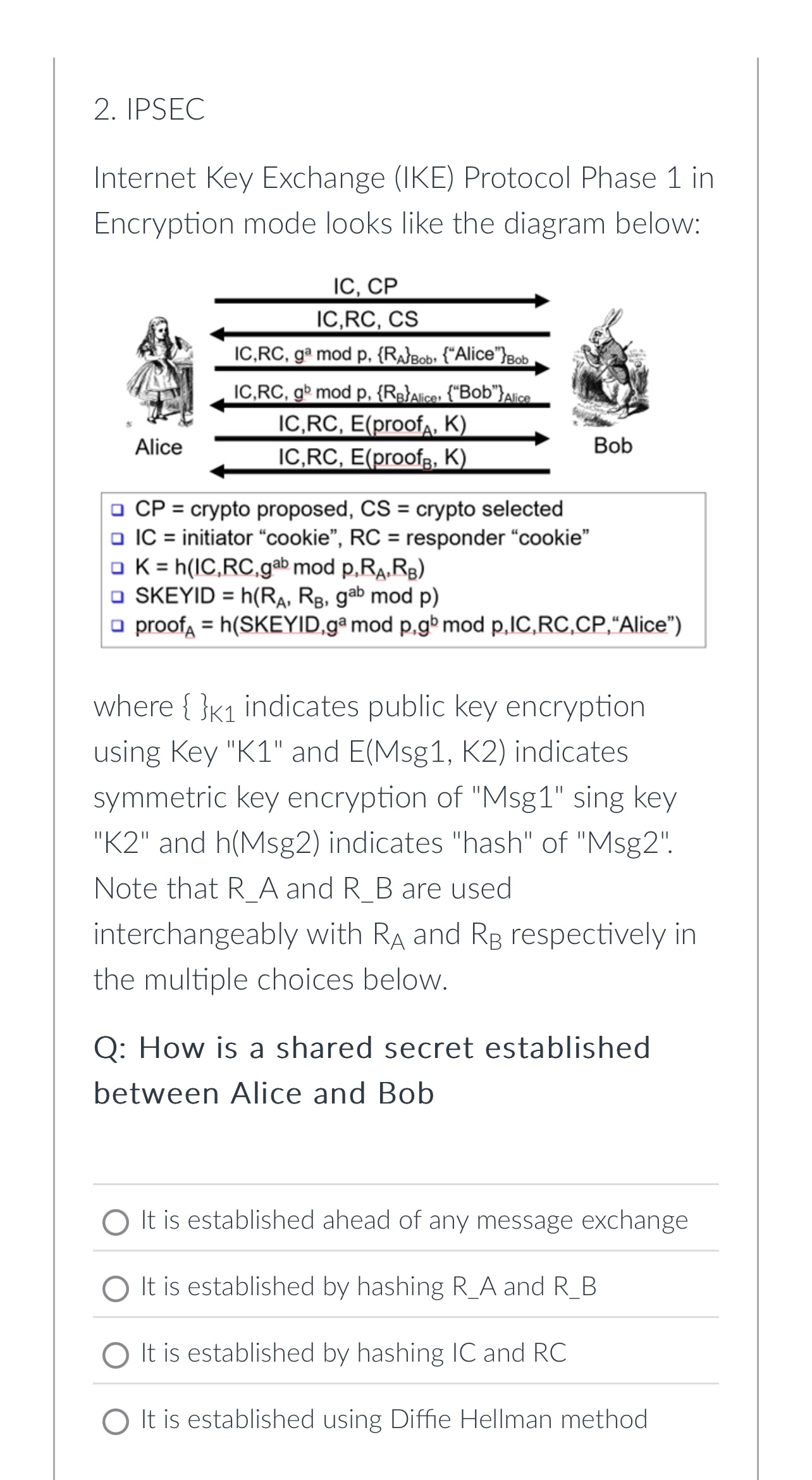
Question: IPSEC Internet Key Exchange ( IKE ) Protocol Phase 1 in Encryption mode looks like the diagram below:where } _ ( K 1 ) :
IPSEC
Internet Key Exchange IKE Protocol Phase in Encryption mode looks like the diagram below:where K: indicates public key encryption using Key K and EMsg K indicates symmetric key encryption of Msg sing key K and hMsg indicates "hash" of MsgNote that RA and RB are used interchangeably with RA and RB respectively in the multiple choices below.
Q: How is a shared secret established between Alice and Bob
It is established ahead of any message exchange
It is established by hashing and
It is established by hashing IC and RC
It is established using Diffie Hellman method
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


