Question: Making the Grade - Using COBIT to Study Computer Crime on a College Campus Abstract: ISACA, a non-profit, independent association that advocates for professionals involved
Making the Grade - Using COBIT to Study Computer Crime on a College Campus
Abstract: ISACA, a non-profit, independent association that advocates for professionals involved in information security, assurance, risk management and governance, recently updated its IT governance framework, COBIT. COBIT 2019 presents a logical approach to information technology and policy issues. Using a recent real-world computer crime that occurred at a community college, students address breaches of various COBIT components. Students then recommend approaches to minimize the risks and vulnerabilities that expose this school and others. This current case exposes students to COBIT's components and the value it provides.
Keywords: Case study, Information technology governance, COBIT model, controls
1. CASE SUMMARY
Using a recent real-world computer crimes case that occurred at a community college, students address aspects of COBIT to evaluate Information Technology governance and management. Students then recommend approaches to minimize the risks and vulnerabilities that expose this school and others.
2. CASE TEXT
2.1 Premeditation at the Mall[i]
Click, click, click, click tapped the heels of the two women's shoes on the mall's marble floor. The mall was air-conditioned on that hot July day. Shopping really hadn't been on Suzy Student's (name changed[ii]) mind though as she walked with her friend, Mary Accompliceii.
Mary asked Suzy what was the matter as she sensed her friend was abnormally quiet.
Suzy was stressed as she was struggling in her summer microbiology class at the local community college. Suzy contemplated finding a way to change her grades...but without studying. This indeed would violate the Academic Integrity Policy and Code of Conduct Policy at her school, but cracking her professor's password to his gradebook seemed more palatable. Suzy asked Mary for help.
Mary was confused. While she worked as an administrative assistant in radiology at a local medical clinic, she didn't have the knowledge to assist with biology topics. She also didn't possess hacking skills to break into a computer system. Mary wondered how she could help.
Suzy explained that her instructor, Professor Microbiology, lived locally and may have been a patient at the medical clinic. Suzy asked, "Can you see if this guy has gone to your work or come into your work?"
Mary asked why.
Suzy explained she had been to his office multiple times before class for extra help and observed his computer login ended in 161. She'd tried to guess his password several times but had been unsuccessful. She'd even attempted to use the "change my password" feature in the college's system, but realized she needed the last four digits of the professor's social security number.
Mary wondered about the username. Suzy cleared that up. The college configured its IT infrastructure where faculty's and staff's usernames are the same for all systems: it is the last name and their first initial, up to 8 characters[iii]. Guessing the username was simple. However, if someone did forget the username, it could be retrieved by either entering the SSN or the college ID number and last name.
2.2 Profile and Password Manager
The college's website openly detailed how to setup and/or change a faculty or staff's password. To setup the account initially, one needed the person's username and the last four digits of the person's SSN. In the setup, the program asked for security questions and gave many options from which to choose. Examples were: "What is your mother's maiden name?" "What is the name of your favorite childhood friend?" and "In what city or town was your first job?"
To validate the user's identity, the person needed to re-enter the username, last four digits of the SSN, and his or her birthdate. Then, one of the security questions appeared and the person needed to answer it identically to how it was entered originally. The user then could choose a password that met the following requirements:
-Cannot contain any part of the username, full name or date of birth
-Must be a minimum of 8 characters in length and a maximum of 14 characters
-Must contain both uppercase and lowercase letters.
-Must contain at least one number.
-Must be a new password, not a previously used one. (The college's website states that it enforces changing of a password every 180 days.)
When the account holder changed his or her password, the Password Manager alerted the user that it had been updated.
The college's Electronics Communications Policy describes appropriate and inappropriate use of electronic resources, monitoring and confidentiality, reporting misuse, consequences of failure to comply with guidelines for responsible use, and email user responsibilities.
Once in possession of a valid username and password, a user could access many of the college's systems such as email, the learning platform for courses and other general information such as registration and billing.
2.3 Identity Theft
Later, Suzy texted Mary. "Has Prof. Microbiologyii ever been a patient?"
Mary wrote back that she would check the next day.
Indeed, the next day Suzy's phone buzzed. It was from Mary! It read, "This guy?"
Her text included a photo of Professor Microbiology's personal information - his partial social security number, date of birth, address and mother's maiden name. Suzy immediately recognized the name! It was him!
Suzy texted back that it was the correct person.
"Don't do anything!" Mary shot back. "I could lose my job!"
Suzy didn't do anything with that information right away but she kept the idea in the back of her mind.
2.4 Computer Crime
As noted before, Suzy had watched the professor log in and believed the password ended in "161." In the past, Suzy had tried to guess the password several times. Frustrated, Suzy had then tried the "change my password" feature, but this required the last four digits of the professor's social security number. She also had needed the maiden name of Prof. Microbiology's mother (one of the security questions asked for validation purposes). This is where Mary had been helpful. However if those didn't work, she needed to discover another way to get that password.
Professor Microbiology's password met the conditions of the college's password requirements as it contained one upper-case letter, one lower-case letter, and at least one numeral....it was also something obscure that only had meaning to him.
However, Suzy eventually cracked the password. How do you think she did it? iii
Sitting alone behind her computer, Suzy not only changed her own grades but also the grades of 37 other students in two different microbiology classes. The jarring image of opening the gradebook and finding atypical scores for ALL of his students led Professor Microbiology to alert the administration.
2.5 Investigation and Confession
2.5.1 Suzy's Confession
On July 27, 2017, the local township police sergeant traveled to the community college for the report of a computer crime. During the initial investigation, the sergeant learned that someone had accessed a faculty's computerized gradebook and changed the grades of 38 students in two different microbiology classes by using the professor's personal and private username and password.
Upon speaking with the professor, the sergeant ascertained that the professor had not given anyone permission to access or alter the grades using the faculty credentials. After examining the grade changes and IP address records, the sergeant uncovered a suspect....Suzy Student. At the time Suzy changed the grades, she had also accessed her own student account and ex@m grades, using the exact same IP address that had accessed Prof. Microbiology's faculty account.
Almost one week later, the sergeant interviewed Suzy in the presence of her attorney. Suzy confessed to accessing the grades under the identity of her microbiology professor, without his permission, and changing her grade and 37 other students' grades.
The sergeant prodded Suzy on how she had accomplished this. During tutoring sessions, Suzy had watched the professor log in and believed the password ended in "161." Suzy had tried to guess the password several times and was unable to figure out the password. Suzy had then tried the "change my password" feature, but his required the last four digits of the professor's social security number. She had asked her friend for help.
Mary had texted Suzy a photograph of the professor's personal information the next morning asking "Is this who you're talking about?" When the sergeant asked Suzy on what day this occurred, she stated that the sergeant could "probably access the texts and find out."
The sergeant questioned how Mary had benefitted from helping Suzy, and Suzy replied that Mary had not benefitted in any way. The sergeant also asked if Mary knew Prof. Microbiology. Mary did not know him. The sergeant then inquired, "This was a roll of the dice" as far as whether Prof. Microbiology was a patient.
Suzy answered, "Yes, yes, I wish he was not."
2.5.2 Mary's Confession
After the confession from Suzy, the sergeant paid a visit to Mary at the medical center where she worked. Voluntarily, Mary agreed to speak with the sergeant, and the sergeant explained he was investigating Suzy for changing her grades at her college.
The sergeant asked Mary if she had confirmed that Prof. Microbiology was a patient, and Mary admitted that she had logged into the medical center's records and confirmed Prof. Microbiology had been a patient at one time. The sergeant asked if Mary had provided any of the Prof. Microbiology's personal information to Suzy and she ignored the question.
"Suzy already knew the last four digits of Prof. Microbiology's social security number, but needed the remaining digits."
At first, Mary assured the sergeant that she hadn't given any of Prof. Microbiology's personal information to Suzy. Then, Mary exclaimed, "I told her not to do it!"
The sergeant questioned if Mary had sent a photo containing Prof. Microbiology's personal information. Mary asked, "Do I need an attorney?" The sergeant replied that it was her choice. Mary then ended the interview.
2.6 Search Warrant
Four days after the confessions, the sergeant served a search warrant to the medical center seeking records pertaining to Mary's access to Prof. Microbiology's records. The sergeant obtained computer screen captures of Mary's access. Those screen captures displayed Prof. Microbiology's partial social security number, date of birth, address and mother's maiden name.
Based on the above facts and circumstances, the sergeant requested the issuance of arrest warrants for Suzy Student and Mary Accomplice.
2.7 Aftermath
According to the Court of Common Pleas Criminal Dockets[iv], both Suzy and Mary were convicted of identity theft, unlawful use of computer by accessing it to disrupt functions, and computer trespassing by altering data. Suzy was sentenced to 12 months but served her sentence through 100 hours of community service. Interestingly, Mary was sentenced to 24 months and served her sentence through 200 hours of community service.
3. REQUIREMENTS
1. Consider the seven interacting components of COBIT 2019's Governance system. Describe how the breakdown in at least five of these components contributed to the crimes noted in the case. Make sure to use specific examples from the case to support your answer.
2. Considering your answer in Question 1, provide at least five recommendations to improve IT governance and management at this college (or other colleges/universities with similar policies and procedures).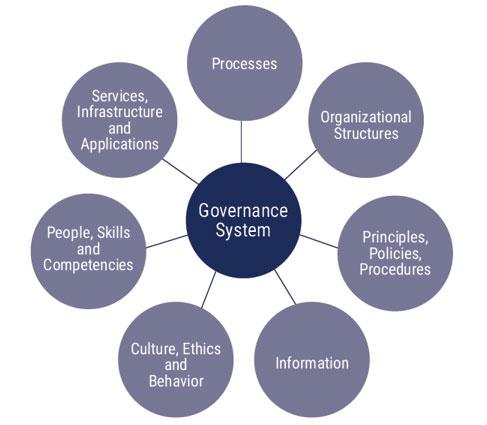
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


