Question: Match the following terms as described in the example highlighted in blue. Choose the closest definition that matches the concept. For this part, please refer
Match the following terms as described in the example highlighted in blue. Choose the closest definition that matches the concept.
For this part, please refer to textbook Chapters
See the full table on the next page.
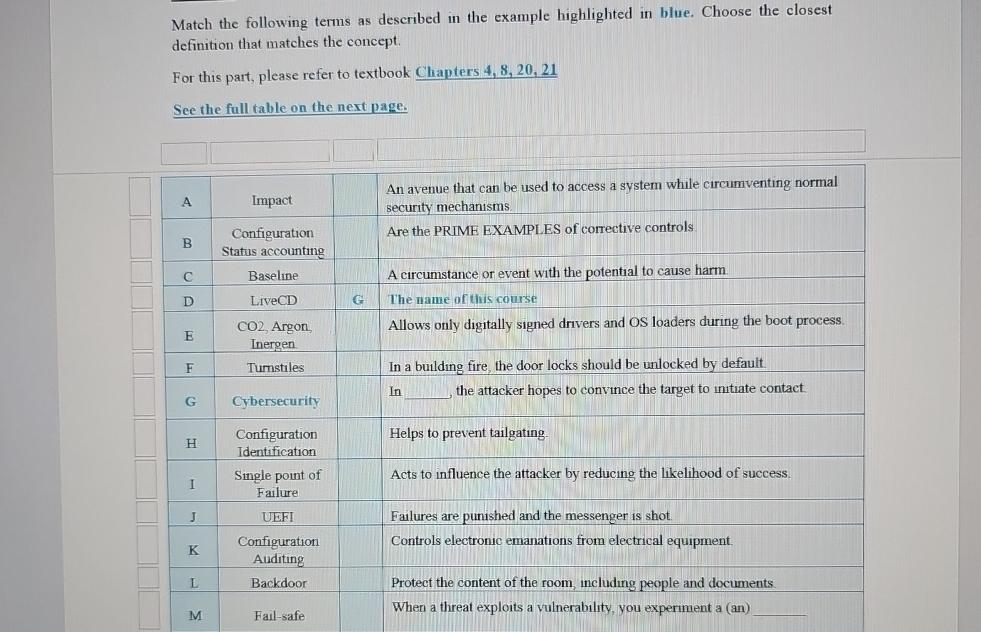
tableAImpact,,tableAn avenue that can be used to access a system while circumventing normalsecurity mechanisms.BtableConfigurationStatus accountingAre the PRIME EXAMPLES of corrective controlsCBaseline,,A circumstance or event with the potential to cause harm.DLiveCD,GThe name of this courseEtable Argon,InergenAllows only digitally signed drivers and OS loaders during the boot process.FTurnstiles,,In a building fire, the door locks should be unlocked by default.GCybersecurity,,In the attacker hopes to convince the target to intiate contact.tableConfigurationIdentificationHelps to prevent tailgating.ItableSingle point ofFailureActs to influence the attacker by reducing the likelihood of success.JUEFI,,Failures are punished and the messenger is shot.KtableConfigurationAlditingControls electronic emanations from electrical equipment.LBackdoor,,Protect the content of the room, including people and documents.MFailsafe,,When a threat exploits a vulnerability, you experiment a an
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


