Question: NEED HELP WITH THIS PLEASE WILL LEAVE GOOD REVIEW Case study A new startup is developing a subscription-based application for time management. The basic idea
NEED HELP WITH THIS PLEASE WILL LEAVE GOOD REVIEW
Case study
A new startup is developing a subscription-based application for time management. The basic idea is that users are able to define TODO items and then track time that is spend on completing them. Each TODO item can have a title, a description, a deadline, and an estimate of how much time it is expected to take. TODO items can also be assigned to other users of the platform.
Before somebody can use the app, they need to sign up by providing basic information, such as their name, email address, and credit card details. All these details are stored in the backend database.
After registration, the user can interact with the application via a mobile app, or (through a browser) via a web site. All data is stored on a backend database and is accessed via an API (Application Programmer's Interface). The architecture is visually displayed in the diagram below. It is expected that the organization needs an infrastructure of approximately 15 servers during its startup stage.
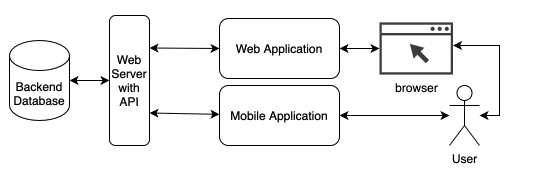
The startup employs 25 employees who work from home. Each employee is provided with a computer and a cell phone. There is (small) corporate office with a data center as well.
Assignment
For this assignment, you are a consultant who has been asked to give recommendations about how to secure the data and the application.
You are tasked with developing a threat model and with recommending what controls must be implemented to secure this application.
Given a budget of $325,000 per year, choose from the controls listed below. Explain why you chose each control, what its function is, and what the overall application's architecture looks like once you have implemented all of your recommendations.
| Control | Cost per year |
|---|---|
| Chief information security officer | $200,000 |
| Information security engineer | $125,000 |
| Information security analyst | $100,000 |
| Virtual Private Network | $10,000 |
| Firewall (each) | $25,000 |
| Phishing Awareness Training | $20,000 |
| Antivirus/Endpoint Protection | $20,000 |
| Patch management platform | $20,000 |
| Vulnerability scanning service | $10,000 |
| Whole disk encryption (per device) | $1,000 |
| TLS encryption (per server) | $1,500 |
| Penetration test (per engagement) | $30,000 |
| Threat Intelligence Subscription | $30,000 |
| Cloud Security Platform | $40,000 |
| Multi factor Authentication Service | $25,000 |
| Additional Security Consultancy | $20,000 |
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


