Question: Needs all componets. make sure text is text and not an image please and thank you. Search Old Dominion University and the Web for examples
Needs all componets. make sure text is text and not an image please and thank you. 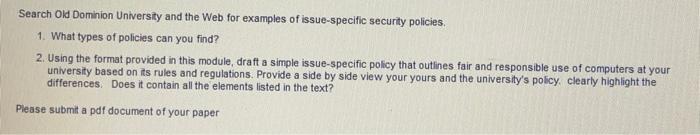


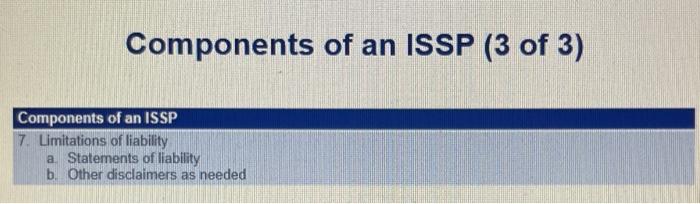
Search Old Dominion University and the Web for examples of issue-specific security policies. 1. What types of policies can you find? 2. Using the format provided in this module, draft a simple issue-specific policy that outlines fair and responsible use of computers at your university based on its rules and regulations. Provide a side by side view your yours and the university's policy, clearly highlight the differences. Does it contain all the elements listed in the text? Please submit a pdf document of your paper Components of an ISSP (1 of 3) Components of an ISSP 1. Statement of policy a. Scope and applicability b. Definition of technology addressed 6. Responsibilities 2. Authorized access and usage of equipment a. User access b. Fair and responsible use C Protection of privacy 3. Prohibited use of equipment a. Disruptive use or misuse b. Criminal use c Offensive or harassing materials d. Copyrighted licensed, or other intellectual property e. Other restrictions Components of an ISSP (2 of 3) Components of an ISSP 4. Systems management a. Management of stored materials b. Employee monitoring C Virus protection d Physical security e. Encryption 5. Violations of policy a. Procedures for reporting violations b. Penalties for violations 6. Policy review and modification a. Scheduled review of policy procedures for modification b. Legal disclaimers Components of an ISSP (3 of 3) Components of an ISSP 7. Limitations of liability a. Statements of liability b. Other disclaimers as needed




Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


