Question: Please ANSWER all question for thumbs up. Please ANSWER all question for thumbs up. Which of the following is a public, routable IP address according
Please ANSWER all question for thumbs up.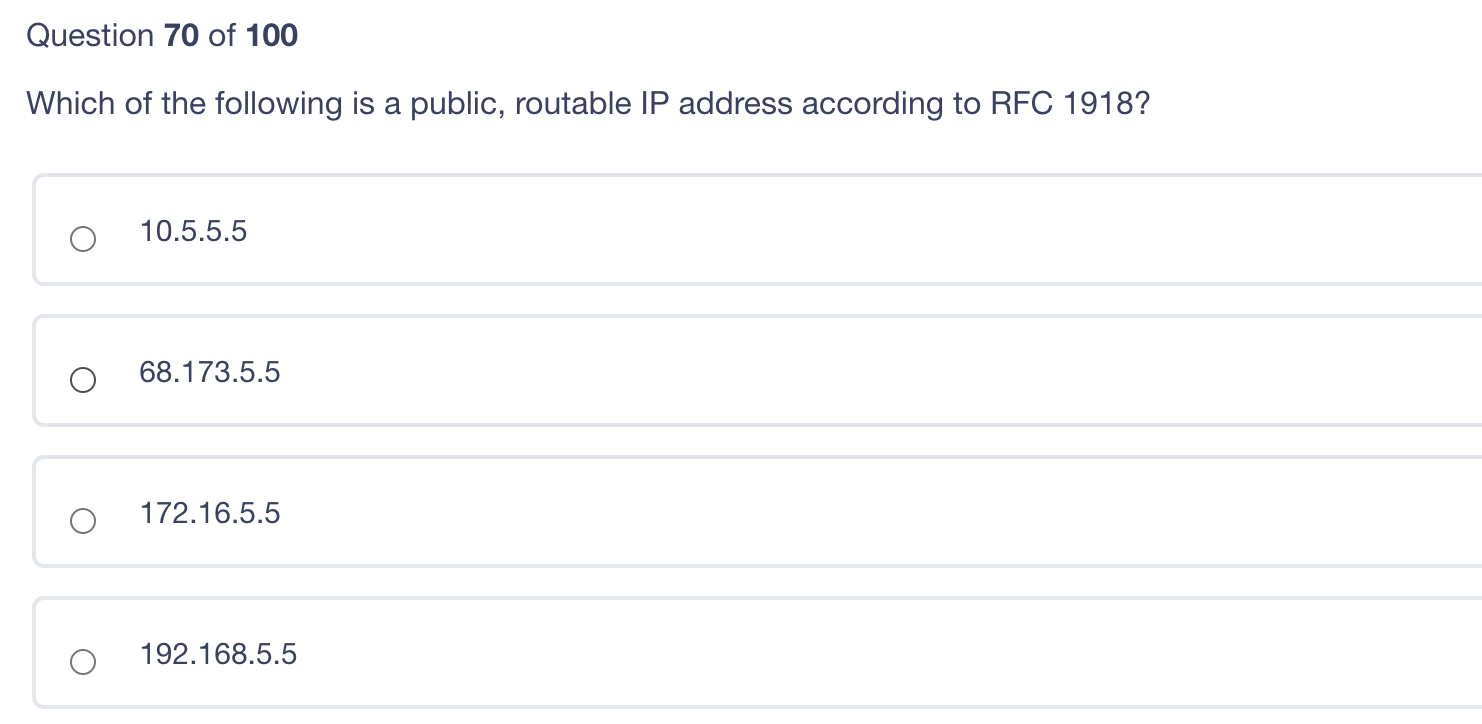
 Please ANSWER all question for thumbs up.
Please ANSWER all question for thumbs up.
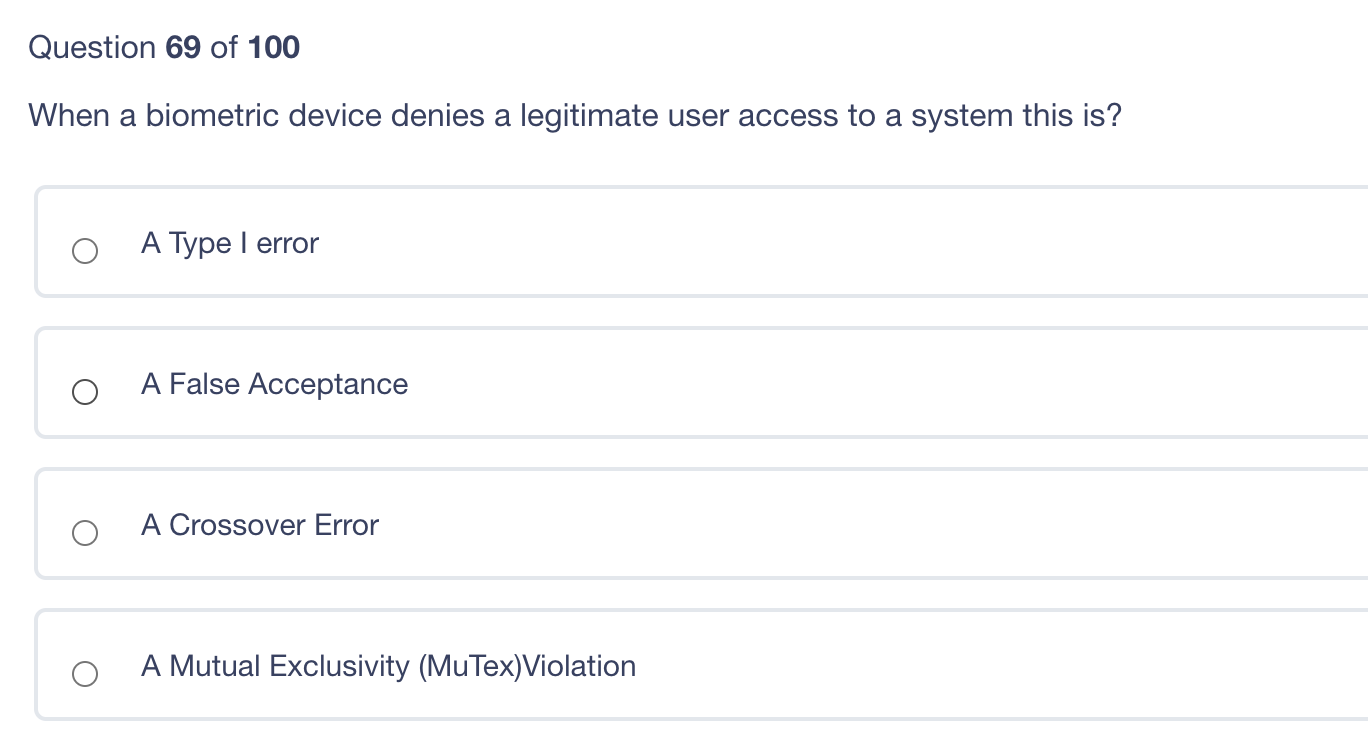
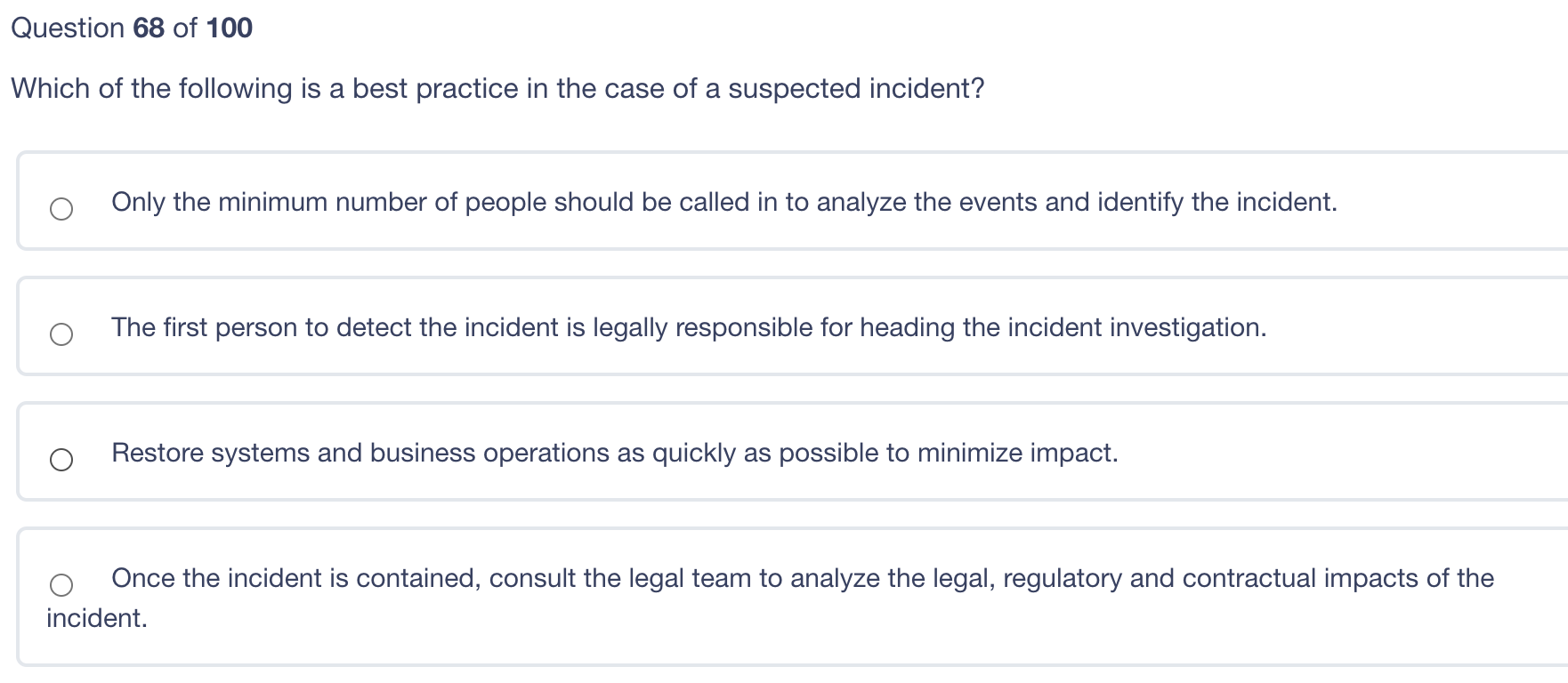
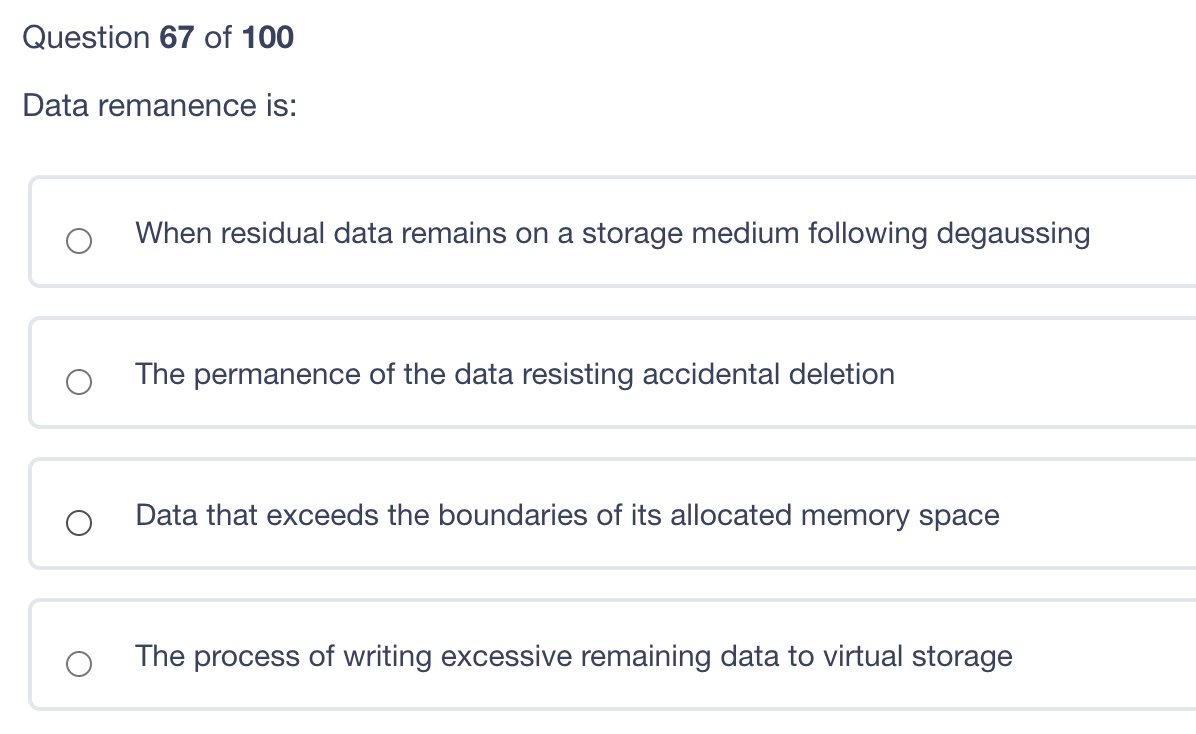
Which of the following is a public, routable IP address according to RFC 1918? 10.5.5.5 68.173.5.5 172.16.5.5 192.168.5.5 Question 69 of 100 When a biometric device denies a legitimate user access to a system this is? A Type I error A False Acceptance A Crossover Error A Mutual Exclusivity (MuTex)Violation Question 68 of 100 Which of the following is a best practice in the case of a suspected incident? Only the minimum number of people should be called in to analyze the events and identify the incident. The first person to detect the incident is legally responsible for heading the incident investigation. Restore systems and business operations as quickly as possible to minimize impact. Once the incident is contained, consult the legal team to analyze the legal, regulatory and contractual impacts of the incident. Question 67 of 100 Data remanence is: When residual data remains on a storage medium following degaussing The permanence of the data resisting accidental deletion Data that exceeds the boundaries of its allocated memory space The process of writing excessive remaining data to virtual storage After a vulnerability assessment has been completed, what should be the first action taken by management? Selecting scan targets Prioritizing Remedial Actions Patching Vulnerable systems Removing outdated applications
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


