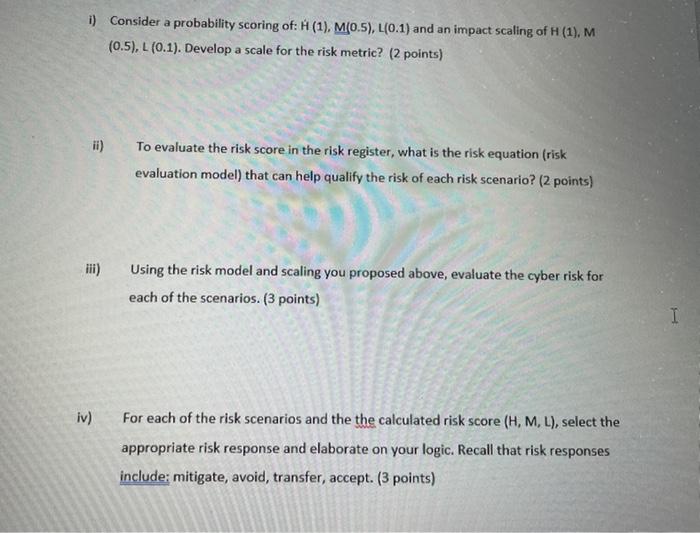
Question: please answer it. Consider the following risk register for The Confident Firm, which details a few risk scenarios that are being assessed. The firm leadership
please answer it.
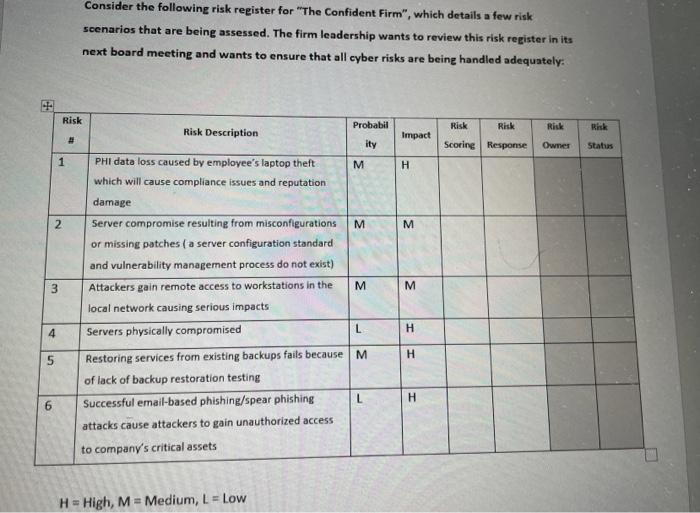
Consider the following risk register for "The Confident Firm", which details a few risk scenarios that are being assessed. The firm leadership wants to review this risk register in its next board meeting and wants to ensure that all cyber risks are being handled adequately: Risk Probabil Risk Risk Risk Risk Risk Description Impact ity Scoring Response Owner Status 1 M H PHI data loss caused by employee's laptop theft which will cause compliance issues and reputation damage 2 M 3 M 4 H Server compromise resulting from misconfigurations M or missing patches (a server configuration standard and vulnerability management process do not exist) Attackers gain remote access to workstations in the M local network causing serious impacts Servers physically compromised L Restoring services from existing backups fails because M of lack of backup restoration testing Successful email-based phishing/spear phishing L attacks cause attackers to gain unauthorized access to company's critical assets H 5 H 6 H = High, M = Medium, L = Low i) Consider a probability scoring of: M(1), M(0.5), L(0.1) and an impact scaling of H (1). M (0.5), L (0.1). Develop a scale for the risk metric? (2 points) ii) To evaluate the risk score in the risk register, what is the risk equation (risk evaluation model) that can help qualify the risk of each risk scenario? (2 points) iii) Using the risk model and scaling you proposed above, evaluate the cyber risk for each of the scenarios. (3 points) I iv) For each of the risk scenarios and the the calculated risk score (H, M, L), select the appropriate risk response and elaborate on your logic. Recall that risk responses include: mitigate, avoid, transfer, accept. (3 points) Consider the following risk register for "The Confident Firm", which details a few risk scenarios that are being assessed. The firm leadership wants to review this risk register in its next board meeting and wants to ensure that all cyber risks are being handled adequately: Risk Probabil Risk Risk Risk Risk Risk Description Impact ity Scoring Response Owner Status 1 M H PHI data loss caused by employee's laptop theft which will cause compliance issues and reputation damage 2 M 3 M 4 H Server compromise resulting from misconfigurations M or missing patches (a server configuration standard and vulnerability management process do not exist) Attackers gain remote access to workstations in the M local network causing serious impacts Servers physically compromised L Restoring services from existing backups fails because M of lack of backup restoration testing Successful email-based phishing/spear phishing L attacks cause attackers to gain unauthorized access to company's critical assets H 5 H 6 H = High, M = Medium, L = Low i) Consider a probability scoring of: M(1), M(0.5), L(0.1) and an impact scaling of H (1). M (0.5), L (0.1). Develop a scale for the risk metric? (2 points) ii) To evaluate the risk score in the risk register, what is the risk equation (risk evaluation model) that can help qualify the risk of each risk scenario? (2 points) iii) Using the risk model and scaling you proposed above, evaluate the cyber risk for each of the scenarios. (3 points) I iv) For each of the risk scenarios and the the calculated risk score (H, M, L), select the appropriate risk response and elaborate on your logic. Recall that risk responses include: mitigate, avoid, transfer, accept. (3 points)