Question: please need help with these thank you Partial Question 4 0.67 /2 pts Which of the following can lead to successful breach of encrypted information
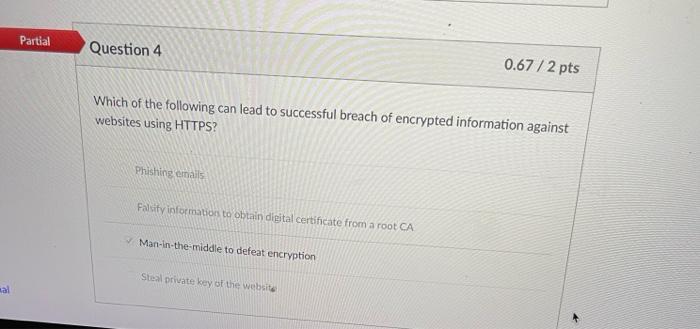
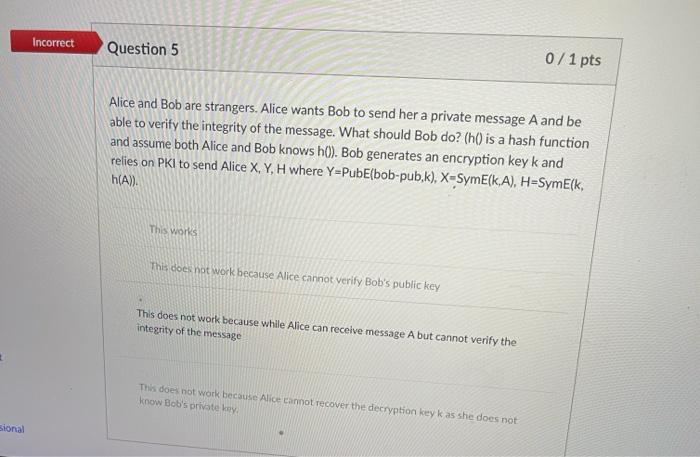
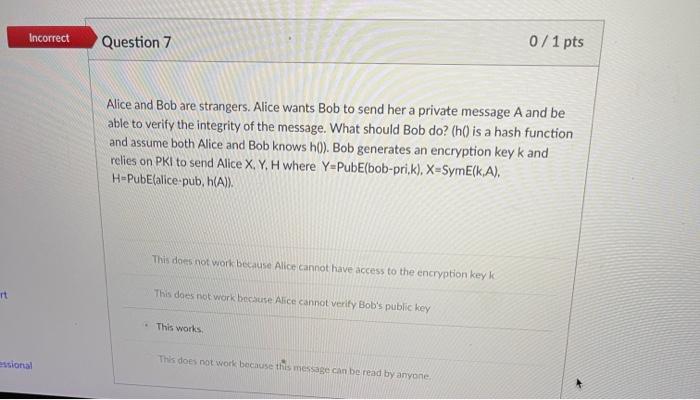
Partial Question 4 0.67 /2 pts Which of the following can lead to successful breach of encrypted information against websites using HTTPS? Phishing emails Falufy information to obtain digital certificate from a root CA Man-in-the-middle to defeat encryption Steal private key of the website al Incorrect Question 5 0/1 pts Alice and Bob are strangers. Alice wants Bob to send her a private message A and be able to verify the integrity of the message. What should Bob do? (h() is a hash function and assume both Alice and Bob knows h0). Bob generates an encryption key k and relies on PKI to send Alice X, Y, H where Y=PubEbob-pub,k), X-SymEk,A), H-SymE(k, h(A)). This works This does not work because Alice cannot verify Bob's public key This does not work because while Alice can receive message A but cannot verify the integrity of the message This does not work because Alice cannot recover the decryption keyk as she does not know Bob's private key sional Incorrect Question 7 0/1 pts Alice and Bob are strangers. Alice wants Bob to send her a private message A and be able to verify the integrity of the message. What should Bob do? (h() is a hash function and assume both Alice and Bob knows h0). Bob generates an encryption key k and relies on PKI to send Alice X, Y, H where Y=PubE(bob-pri,k), X-SymE(k.A), H-PubE(alice-pub, h(A)). This does not work because Alice cannot have access to the encryption key k it This does not work because Alice cannot verify Bob's public key This works essional This does not work because this message can be read by anyone
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


