Question: ** Please with an explanation if possible ** *Please answers all or leave it to another expert* Q1-An organization is developing an authentication service for
** Please with an explanation if possible **
*Please answers all or leave it to another expert*
Q1-An organization is developing an authentication service for use at the entry and exit ports of country borders. The service will use data feeds obtained from passport systems, passenger manifests, and high-definition video feeds from CCTV systems that are located at the ports. The service will incorporate machine-learning techniques to eliminate biometric enrollment processes while still allowing authorities to identify passengers with increasing accuracy over time. The more frequently passengers travel, the more accurately the service will identify them. Which of the following biometrics will MOST likely be used, without the need for enrollment? (Choose two.) A. Voice B. Gait C. Vein D. Facial E. Retina F. Fingerprint
..............................................................
Q2-After entering a username and password, and administrator must gesture on a touch screen. Which of the following demonstrates what the administrator is providing? A. Multifactor authentication B. Something you can do C. Biometric D. Two-factor authentication
..............................................................
Q3-An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following:  Which of the following is the MOST likely cause of the issue?
Which of the following is the MOST likely cause of the issue?
A. The end user purchased and installed a PUP from a web browser B. A bot on the computer is brute forcing passwords against a website C. A hacker is attempting to exfiltrate sensitive data D. Ransomware is communicating with a command-and-control server.
..............................................................
Q4-A security analyst is reviewing logs on a server and observes the following output: 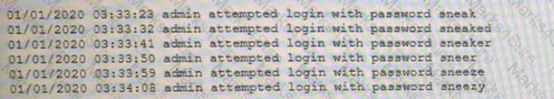
Which of the following is the security analyst observing? A. A rainbow table attack B. A password-spraying attack C. A dictionary attack D. A keylogger attack
..............................................................
Q5-A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output: 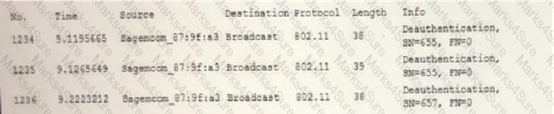 Which of the following attacks does the analyst MOST likely see in this packet capture? A. Session replay B. Evil twin C. Bluejacking D. ARP poisoning
Which of the following attacks does the analyst MOST likely see in this packet capture? A. Session replay B. Evil twin C. Bluejacking D. ARP poisoning
..............................................................
Q6-A security analyst is performing a packet capture on a series of SOAP HTTP requests for a security assessment. The analyst redirects the output to a file After the capture is complete, the analyst needs to review the first transactions quickly and then search the entire series of requests for a particular string Which of the following would be BEST to use to accomplish the task? (Select TWO). A. Head B. Tcpdump C. grep D. rail E. curl F. openssi G. dd
..............................................................
Q7-A security analyst is configuring a large number of new company-issued laptops. The analyst received the :following requirements .The devices will be used internationally by staff who travel extensively .Occasional personal use is acceptable due to the travel requirements Users must be able to install and configure sanctioned programs and productivity .suites .The devices must be encrypted .The devices must be capable of operating in low-bandwidth environments Which of the following would provide the GREATEST benefit to the security posture ?of the devices A.Configuring an always-on VPN B. Implementing application whitelisting
C. Requiring web traffic to pass through the on-premises content filter D. Setting the antivirus DAT update schedule to weekly
..............................................................
Q8-A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the companys data? A. A.Containerization B. Geofencing C. C. Full-disk encryption D. Remote wipe
..............................................................
Q9-A user contacts the help desk to report the following: Two days ago, a pop-up browser window prompted the user for a name and password after connecting to the corporate wireless SSID. This had never happened before, but the user entered the information as requested. The user was able to access the Internet but had trouble accessing the department share until the next day. The user is now getting notifications from the bank about unauthorized transactions. Which of the following attack vectors was MOST likely used in this scenario? A. Rogue access point B. Evil twin C. DNS poisoning D. ARP poisoning
Mais S lar Time: 06:32:29 UTC Event Description: This Process Blocked: False File Quarantined: False Operating system: Windows 10 File Name: Device\HarddiskVolume4\U Connection Details: 35.242.219.204:80 en geen etca TEN Naruto Sure Marke Sure Marigo Sure Markhure Manors Narkour Marehe Mark Sade Masters Markare Mars Marker Mange Marketer Market larks4sur Martin Marks 4 Sure Mar Marks Sur Mare Marks Sur Mars Man 01/01/2020 03:33:23 admin attempted login with password aneak 01/01/2020 03:33:32 admin attempted login with password aneaked 01/01/2020 03:33:41 admin attempted login with password sneaker 01/01/2020 03:33:50 admin attempted login with password sneer 01/01/2020 03:33:59 amin attempted login with password aneeze 01/01/2020 03:34:08 amin attempted login with password sneezy Marks Mark any Marsu 299 Marksies ure Marksas tanks 9540 38 Marks De 10 9.1265 87:9:23 Broadcas17 Source Destination Protocol Length Info 9.1195665 Broadcast 802.11 9655, EN 802.11 92655, 10 Deauthentication, 1236 87:98: a3 Harks4Sure darksas an Marks 3212 PASur SASur Manasure arks Su
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


