Question: Q.2 Below an authentication protocol, based on shared secret key, is called Two-way authentication using a challenge-response protocol. If you are intruder, say your name
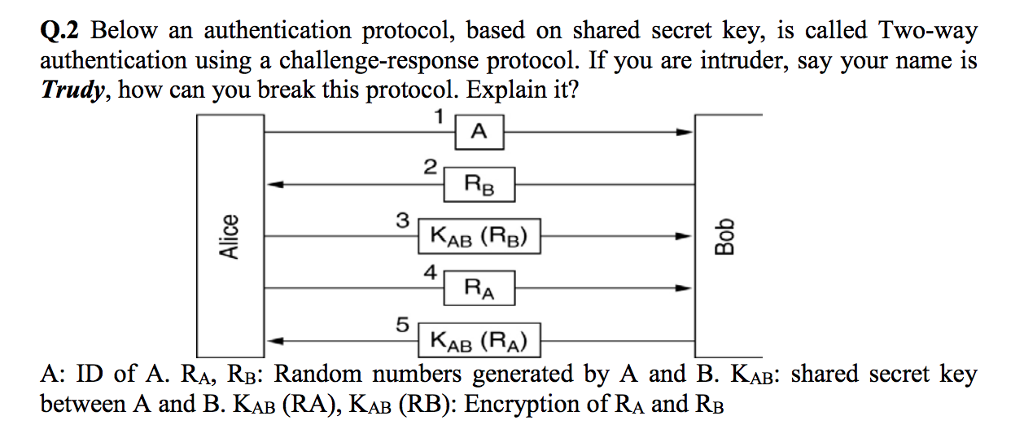
Q.2 Below an authentication protocol, based on shared secret key, is called Two-way authentication using a challenge-response protocol. If you are intruder, say your name is Trudy, how can you break this protocol. Explain it? 1 2 AB (RB) - 4 RA 5 KAB (RA) A: ID of A. RA, RB: Random numbers generated by A and B. KAB: shared secret key between A and B. KaB (RA), KAB (RB): Encryption of RA and RB
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


