Question: Question 1: The malicious user of host E uses the Man-in-the-Middle (MiM) attack to sniff the traffic between the hosts A and D. To do
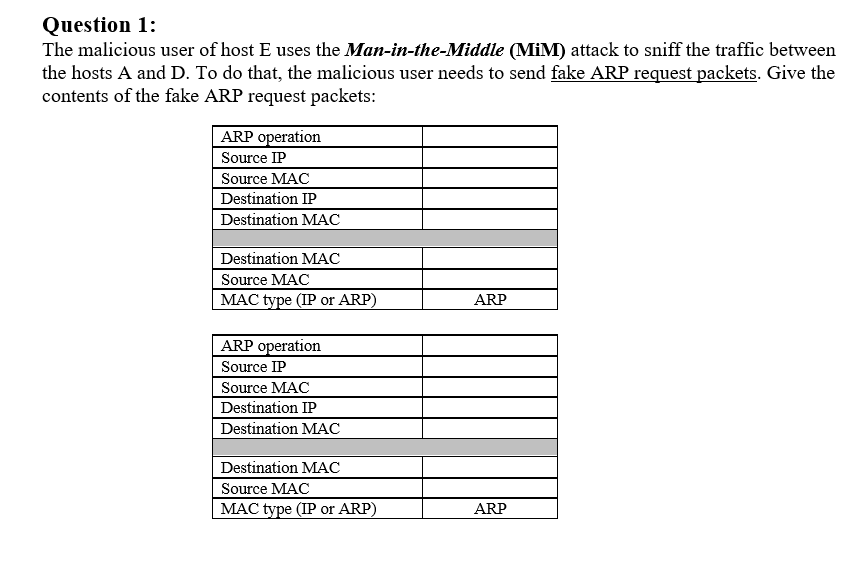
Question 1: The malicious user of host E uses the Man-in-the-Middle (MiM) attack to sniff the traffic between the hosts A and D. To do that, the malicious user needs to send fake ARP request packets. Give the contents of the fake ARP request packets
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


