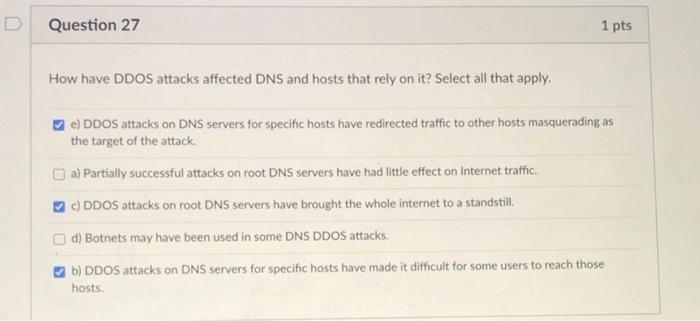
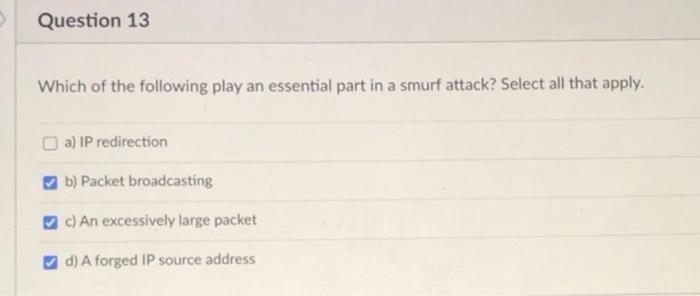
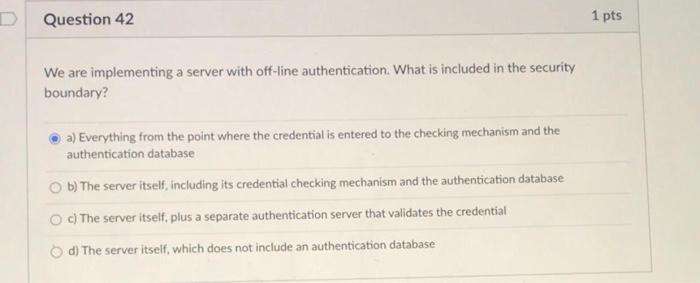
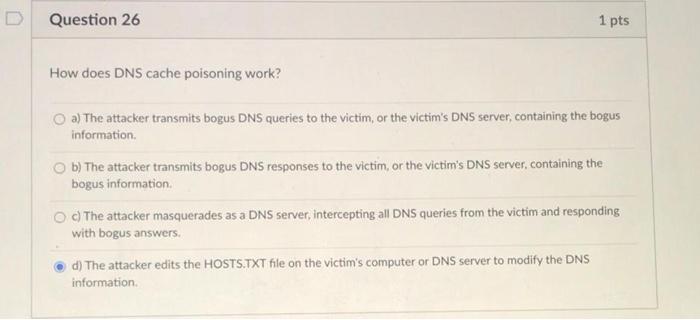
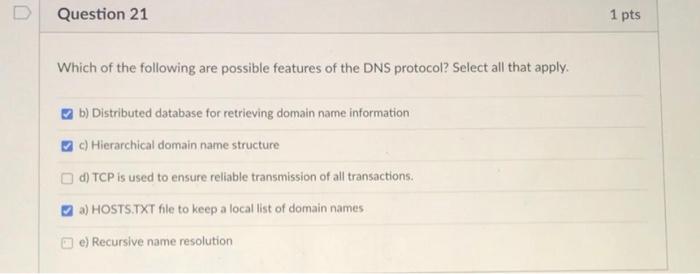
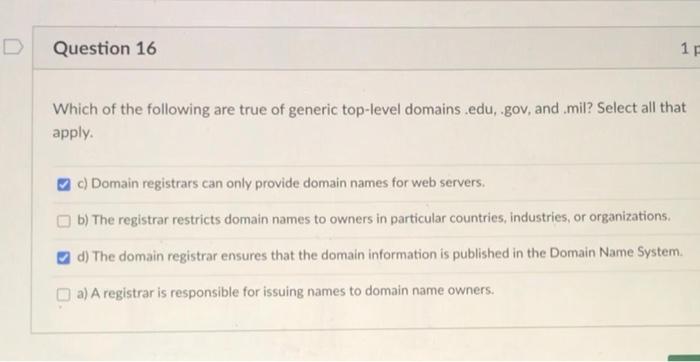
Question: Question 27 1 pts How have DDOS attacks affected DNS and hosts that rely on it? Select all that apply. c) DDOS attacks on DNS
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


