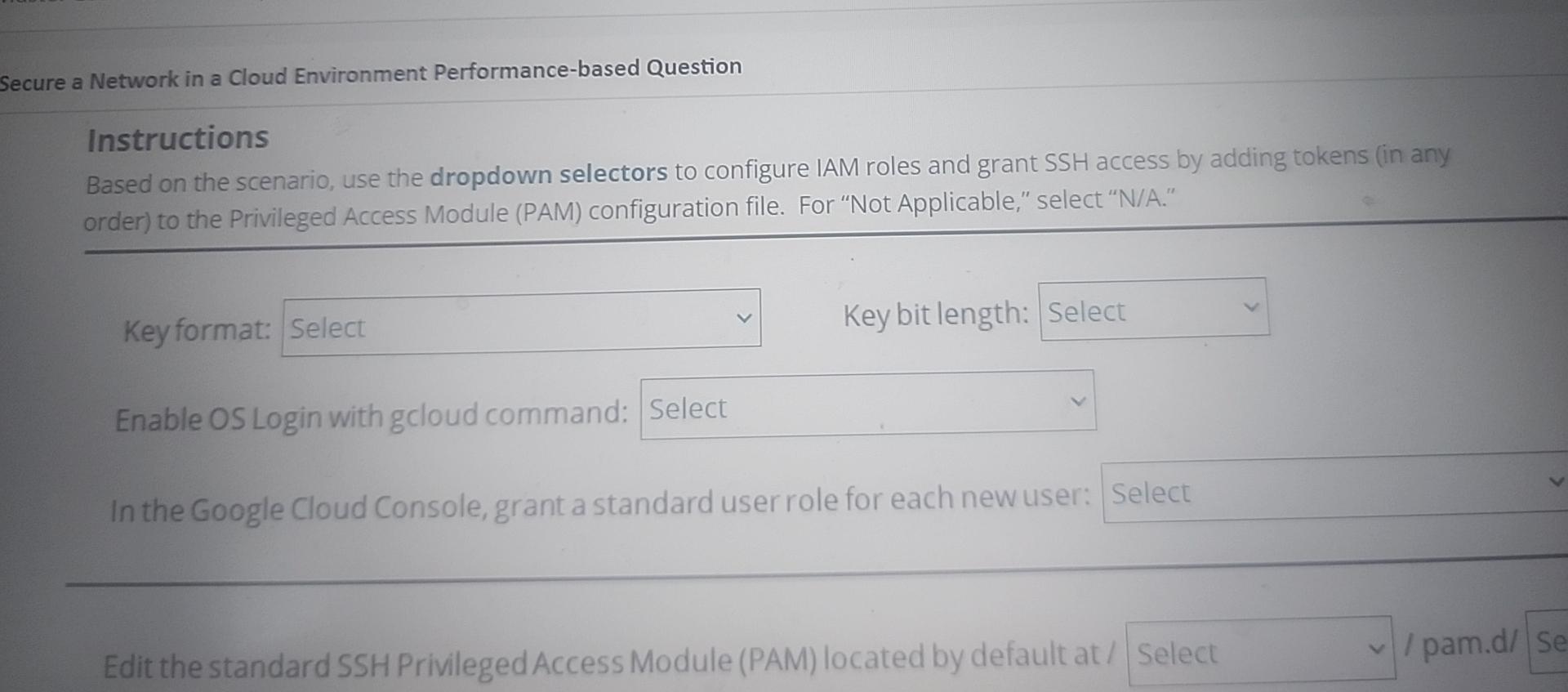
Question: Secure a Network in a Cloud Environment Performance - based Question Instructions Based on the scenario, use the dropdown selectors to configure IAM roles and
Secure a Network in a Cloud Environment Performancebased Question
Instructions
Based on the scenario, use the dropdown selectors to configure IAM roles and grant SSH access by adding tokens in any order to the Privileged Access Module PAM configuration file. For "Not Applicable," select NA
Key format:
Key bit length:
Enable OS Login with gcloud command:
In the Google Cloud Console, grant a standard user role for each new user:
Edit the standard SSH Privileged Access Module PAM located by default at
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


